
When we write some destructive programs, we need to traverse the process and extract the ID
For the above functions, we first introduce several APIs
1.CreateToolhelp32Snapshout function
Get a snapshot of a process, module or thread
The syntax is as follows:
HANDLE WINAPI CreateToolhelp32Snapshot( _In_ DWORD dwFlags, _In_ DWORD th32ProcessID );
The first parameter: the snapshot contains part of the system , the parameters are as follows:
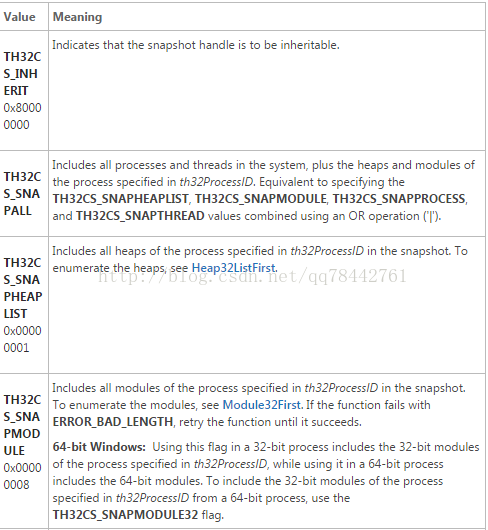
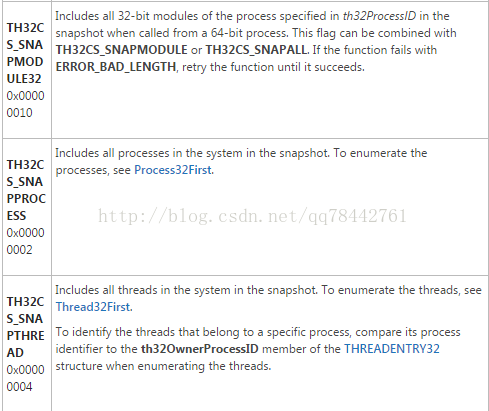
typedef struct tagPROCESSENTRY32 {
DWORD dwSize;
DWORD cntUsage;
DWORD th32ProcessID;
ULONG_PTR th32DefaultHeapID;
DWORD th32ModuleID;
DWORD cntThreads;
DWORD th32ParentProcessID;
LONG pcPriClassBase;
DWORD dwFlags;
TCHAR szExeFile[MAX_PATH];
} PROCESSENTRY32, *PPROCESSENTRY32;
#include <Windows.h>
#include <stdio.h>
#include <TlHelp32.h>
int main()
{
HANDLE hProceessnap = CreateToolhelp32Snapshot(TH32CS_SNAPPROCESS, 0);
if (hProceessnap == INVALID_HANDLE_VALUE)
{
printf_s("创建进行快照失败\n");
return -1;
}
else
{
PROCESSENTRY32 pe32;
pe32.dwSize = sizeof(pe32);
BOOL hProcess = Process32First(hProceessnap, &pe32);
char buff[1024];
while (hProcess)
{
wsprintf(buff, "进程名:%s--------------------进程ID:%d", pe32.szExeFile, pe32.th32ParentProcessID);
printf_s("%s\n", buff);
memset(buff, 0x00, 1024);
hProcess = Process32Next(hProceessnap, &pe32);
}
}
CloseHandle(hProceessnap);
return 0;
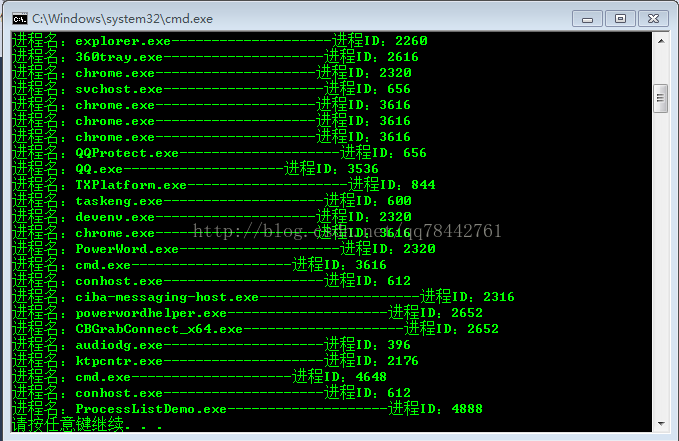
}
 How to recover browser history on computer
How to recover browser history on computer
 How to solve the problem that the folder does not have security options
How to solve the problem that the folder does not have security options
 file_get_contents
file_get_contents
 How to resume use of gas after payment
How to resume use of gas after payment
 Linux restart command type
Linux restart command type
 BigDecimal method to compare sizes
BigDecimal method to compare sizes
 Dynamic link library initialization routine failed
Dynamic link library initialization routine failed
 how to change ip address
how to change ip address




