 Operation and Maintenance
Operation and Maintenance
 Linux Operation and Maintenance
Linux Operation and Maintenance
 Linux user management (1) graphic tutorial on creating and deleting users
Linux user management (1) graphic tutorial on creating and deleting users
Linux user management (1) graphic tutorial on creating and deleting users
1. Commonly used commands:
(1) Two commands to create a user:
adduser
useradd
(2) User Delete command:
userdel
2. The difference between the two user creation commands
adduser: will automatically specify the home directory and system shell for the created user version, the user password will be entered when creating.
useradd: You need to use parameter options to specify the above basic settings. If no parameters are used, the created user will have no password, no home directory, and no specified shell version.
3. Use adduser
For example:
$ adduser apple
The output displays:

This way When you create a username, you create the user's home directory and password.
By default:
adduser will actively call /etc/adduser.conf when creating a user;
When creating a user's home directory, it will be under /home by default, and Created as /home/user name
If the home directory already exists, it will not be created. However, although this home directory serves as the new user’s home directory and will be entered into this directory when logging in by default, this directory does not exist. It does not belong to the new user. When userdel is used to delete a new user, the home directory will not be deleted because the home directory already existed before it was created and does not belong to the user.
Specify the shell version of the user:/bin/bash
Therefore, the commonly used parameter options are:
(1) -HOME: Specify the path to create the main directory, default It is to create a directory with the same name as the user name in the /home directory, which can be specified here; if the directory with the same name as the home directory exists, it will not be created, and the home directory will only be entered when logging in.
(2) -QUIET: Just print only warnings and error information , ignore other information.
(3) --debug: Locate error information.
(4) --conf: Use the specified configuration file when creating a user.
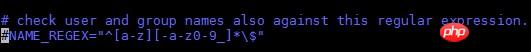
(5) --force-badname: By default, when creating a user, the regular expression in /etc/adduser.conf will be used to check whether the user name is It's legal. If you want to use weak checking, use this option. If you don't want to check, you can block the relevant options in /etc/adduser.conf. For example:
4. Use useradd
Note: When using the useradd command to create a new user, the home directory will not be created for the user. The shell version will be specified for the user and no password will be created for the user.
For example:
1. Create a user without using any parameter options:
For example, create a new user tt
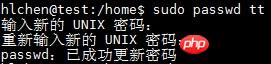
$ sudo useradd tt
(1) You need to specify a login for the user Password:
(2) You need to specify the shell version and user loginhome directory
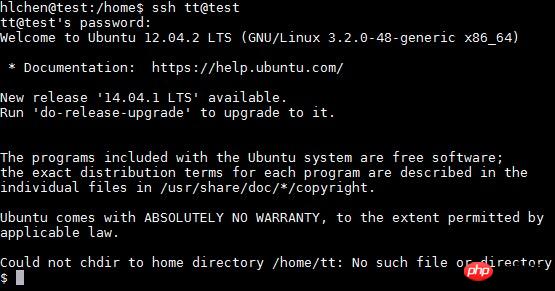
As shown in the picture above, the last line only appears at the beginning:
$
Check the shell version and find that it is /bin/sh:

Explanation that this is not specifying the shell version
The directory where the user logs in is the root directory: /
Although $HOME environmentVariables For /home/tt
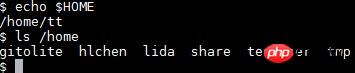
2. Useradd command to specify parameters for the user:
Common command line options:
(1) -d: Specify the user's home directory
(2) -m: If it exists, it will not be created, but this directory does not belong to the newly created user; if the main directory If the directory does not exist, it is forcibly created; -m and -d are used together.
(3) -s: Specify the shell version when the user logs in
(4) -M: Do not create a home directory
For example:
$ sudo useradd -d "/home/tt" -m -s "/bin/bash" tt
Explanation: -d "/home/tt": specifies /home/tt as the main directory
-m means forcing if /home/tt does not exist create
-s 就是指定shell版本
修改tt密码:
$ sudo passwd tt
五、删除用户命令
userdel
(1)只删除用户:
sudo userdel 用户名
(2)连同用户主目录一块删除:
sudo userdel -r 用户名
如果创建时主目录已经存在,即主目录不属于当前要删除的用户,则无法删除主目录,例如:
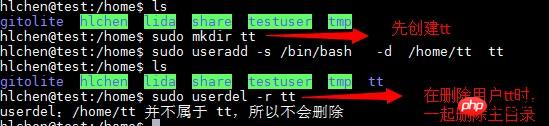
可以看出无法删除已有主目录/home/tt。
六、相关文件:
/etc/passwd - 使 用 者 帐 号 资 讯,可以查看用户信息
/etc/shadow - 使 用 者 帐 号 资 讯 加 密
/etc/group - 群 组 资 讯
/etc/default/useradd - 定 义 资 讯
/etc/login.defs - 系 统 广 义 设 定
/etc/skel - 内 含 定 义 档 的 目 录The above is the detailed content of Linux user management (1) graphic tutorial on creating and deleting users. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
 How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use docker desktop
Apr 15, 2025 am 11:45 AM
How to use Docker Desktop? Docker Desktop is a tool for running Docker containers on local machines. The steps to use include: 1. Install Docker Desktop; 2. Start Docker Desktop; 3. Create Docker image (using Dockerfile); 4. Build Docker image (using docker build); 5. Run Docker container (using docker run).
 How to view the docker process
Apr 15, 2025 am 11:48 AM
How to view the docker process
Apr 15, 2025 am 11:48 AM
Docker process viewing method: 1. Docker CLI command: docker ps; 2. Systemd CLI command: systemctl status docker; 3. Docker Compose CLI command: docker-compose ps; 4. Process Explorer (Windows); 5. /proc directory (Linux).
 What to do if the docker image fails
Apr 15, 2025 am 11:21 AM
What to do if the docker image fails
Apr 15, 2025 am 11:21 AM
Troubleshooting steps for failed Docker image build: Check Dockerfile syntax and dependency version. Check if the build context contains the required source code and dependencies. View the build log for error details. Use the --target option to build a hierarchical phase to identify failure points. Make sure to use the latest version of Docker engine. Build the image with --t [image-name]:debug mode to debug the problem. Check disk space and make sure it is sufficient. Disable SELinux to prevent interference with the build process. Ask community platforms for help, provide Dockerfiles and build log descriptions for more specific suggestions.
 vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
vscode cannot install extension
Apr 15, 2025 pm 07:18 PM
The reasons for the installation of VS Code extensions may be: network instability, insufficient permissions, system compatibility issues, VS Code version is too old, antivirus software or firewall interference. By checking network connections, permissions, log files, updating VS Code, disabling security software, and restarting VS Code or computers, you can gradually troubleshoot and resolve issues.
 What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
What computer configuration is required for vscode
Apr 15, 2025 pm 09:48 PM
VS Code system requirements: Operating system: Windows 10 and above, macOS 10.12 and above, Linux distribution processor: minimum 1.6 GHz, recommended 2.0 GHz and above memory: minimum 512 MB, recommended 4 GB and above storage space: minimum 250 MB, recommended 1 GB and above other requirements: stable network connection, Xorg/Wayland (Linux)
 Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
Can vscode be used for mac
Apr 15, 2025 pm 07:36 PM
VS Code is available on Mac. It has powerful extensions, Git integration, terminal and debugger, and also offers a wealth of setup options. However, for particularly large projects or highly professional development, VS Code may have performance or functional limitations.
 What is vscode What is vscode for?
Apr 15, 2025 pm 06:45 PM
What is vscode What is vscode for?
Apr 15, 2025 pm 06:45 PM
VS Code is the full name Visual Studio Code, which is a free and open source cross-platform code editor and development environment developed by Microsoft. It supports a wide range of programming languages and provides syntax highlighting, code automatic completion, code snippets and smart prompts to improve development efficiency. Through a rich extension ecosystem, users can add extensions to specific needs and languages, such as debuggers, code formatting tools, and Git integrations. VS Code also includes an intuitive debugger that helps quickly find and resolve bugs in your code.
 How to back up vscode settings and extensions
Apr 15, 2025 pm 05:18 PM
How to back up vscode settings and extensions
Apr 15, 2025 pm 05:18 PM
How to back up VS Code configurations and extensions? Manually backup the settings file: Copy the key JSON files (settings.json, keybindings.json, extensions.json) to a safe location. Take advantage of VS Code synchronization: enable synchronization with your GitHub account to automatically back up all relevant settings and extensions. Use third-party tools: Back up configurations with reliable tools and provide richer features such as version control and incremental backups.



