The difference between nginx reverse proxy and forward proxy
I have never understood how to understand the reverse direction of the reflection agent. After learning about it through Baidu, and combining it with the picture below, I finally figured it out a little bit. Simply put, the forward direction is from a LAN to the server, and the reverse direction is from the client to a LAN.
Concept:
The reverse proxy method refers to using a proxy server to accept connection requests on the Internet, then forwarding the requests to the server on the internal network, and returning the results obtained from the server to the client requesting a connection on the Internet. At this time, the proxy server appears as a server to the outside world.
Overview:
A common proxy server is only used to proxy internal network connection requests to the Internet. The client must specify a proxy server and send the http request that is to be sent directly to the Web server to the proxy server. Since hosts on the external network will not configure and use this proxy server, ordinary proxy servers are also designed to search for multiple uncertain servers on the Internet, rather than accessing a fixed server in response to requests from multiple clients on the Internet. server, so ordinary web proxy servers do not support external access requests to the internal network. When a proxy server can proxy a host on the external network to access the internal network, this proxy service is called a reverse proxy service. At this time, the proxy server appears as a Web server to the outside world, and the external network can simply treat it as a standard Web server without specific configuration. The difference is that this server does not store the real data of any web pages. All static web pages or CGI programs are stored on the internal Web server. Therefore, attacks on the reverse proxy server will not destroy web page information, thus enhancing the security of the web server.
There is no conflict between the reverse proxy method and the packet filtering method or the ordinary proxy method, so both methods can be used in the firewall device at the same time. The reverse proxy is used when the external network accesses the internal network, and the forward proxy or packet filtering method is used. Used to deny other external access methods and provide internal network access to external networks. These methods can therefore be combined to provide the best secure access.
Why is it called reverse:
But this does not explain why it is called reverse. In principle, the proxy server processes the request from the client and forwards it to the destination server, so the work of the proxy server does not have any reverse meaning. The picture below illustrates why reverse proxy is called reverse: 
<code> 对了,从结构上来看,正向代理和反向代理的左右两边换了一下,原本代理服务器的客户端来自内网.其和代理服务器组成一个LAN,而反向代理之后.代理服务器和服务器组成了一组.所以从结构来看,是reverse的,从英文的角度来看,reverse这个词包含翻转的意思,其意思就是指结构图上的这种反转,但是由于翻译的关系.到了中文变成反向代理.其实proxy并没有做和以前有什么不同的事情.它仍旧是将来自客户端的请求转发给实际端.,而时至今日,由于CDN的大量使用,反向代理后面的服务器为了适应这种跨网络的架构,而均采用实际IP地址.这样就往往更不容易使得大家对”反向代理这个名词中的反向到底指什么”这个问题有个清晰的答案了。 </code>
The above introduces the difference between nginx reverse proxy and forward proxy, including the relevant aspects. I hope it will be helpful to friends who are interested in PHP tutorials.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1419
1419
 52
52
 1313
1313
 25
25
 1262
1262
 29
29
 1236
1236
 24
24
 How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
How to use Nginx web server caddy
May 30, 2023 pm 12:19 PM
Introduction to Caddy Caddy is a powerful and highly scalable web server that currently has 38K+ stars on Github. Caddy is written in Go language and can be used for static resource hosting and reverse proxy. Caddy has the following main features: Compared with the complex configuration of Nginx, its original Caddyfile configuration is very simple; it can dynamically modify the configuration through the AdminAPI it provides; it supports automated HTTPS configuration by default, and can automatically apply for HTTPS certificates and configure it; it can be expanded to data Tens of thousands of sites; can be executed anywhere with no additional dependencies; written in Go language, memory safety is more guaranteed. First of all, we install it directly in CentO
 Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web server processing in Java API development
Jun 18, 2023 am 10:42 AM
Using Jetty7 for Web Server Processing in JavaAPI Development With the development of the Internet, the Web server has become the core part of application development and is also the focus of many enterprises. In order to meet the growing business needs, many developers choose to use Jetty for web server development, and its flexibility and scalability are widely recognized. This article will introduce how to use Jetty7 in JavaAPI development for We
 How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
How to configure nginx to ensure that the frps server and web share port 80
Jun 03, 2023 am 08:19 AM
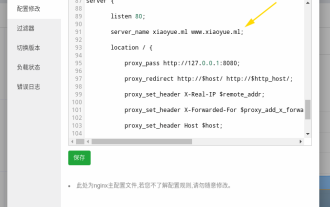
First of all, you will have a doubt, what is frp? Simply put, frp is an intranet penetration tool. After configuring the client, you can access the intranet through the server. Now my server has used nginx as the website, and there is only one port 80. So what should I do if the FRP server also wants to use port 80? After querying, this can be achieved by using nginx's reverse proxy. To add: frps is the server, frpc is the client. Step 1: Modify the nginx.conf configuration file in the server and add the following parameters to http{} in nginx.conf, server{listen80
 Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Real-time protection against face-blocking barrages on the web (based on machine learning)
Jun 10, 2023 pm 01:03 PM
Face-blocking barrage means that a large number of barrages float by without blocking the person in the video, making it look like they are floating from behind the person. Machine learning has been popular for several years, but many people don’t know that these capabilities can also be run in browsers. This article introduces the practical optimization process in video barrages. At the end of the article, it lists some applicable scenarios for this solution, hoping to open it up. Some ideas. mediapipeDemo (https://google.github.io/mediapipe/) demonstrates the mainstream implementation principle of face-blocking barrage on-demand up upload. The server background calculation extracts the portrait area in the video screen, and converts it into svg storage while the client plays the video. Download svg from the server and combine it with barrage, portrait
 How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
How to implement form validation for web applications using Golang
Jun 24, 2023 am 09:08 AM
Form validation is a very important link in web application development. It can check the validity of the data before submitting the form data to avoid security vulnerabilities and data errors in the application. Form validation for web applications can be easily implemented using Golang. This article will introduce how to use Golang to implement form validation for web applications. 1. Basic elements of form validation Before introducing how to implement form validation, we need to know what the basic elements of form validation are. Form elements: form elements are
 What are web standards?
Oct 18, 2023 pm 05:24 PM
What are web standards?
Oct 18, 2023 pm 05:24 PM
Web standards are a set of specifications and guidelines developed by W3C and other related organizations. It includes standardization of HTML, CSS, JavaScript, DOM, Web accessibility and performance optimization. By following these standards, the compatibility of pages can be improved. , accessibility, maintainability and performance. The goal of web standards is to enable web content to be displayed and interacted consistently on different platforms, browsers and devices, providing better user experience and development efficiency.
 How to solve the problem of unable to access the Internet in win11? Guide to solving the problem of Win11 computer being unable to connect to the internet
Jan 29, 2024 pm 08:57 PM
How to solve the problem of unable to access the Internet in win11? Guide to solving the problem of Win11 computer being unable to connect to the internet
Jan 29, 2024 pm 08:57 PM
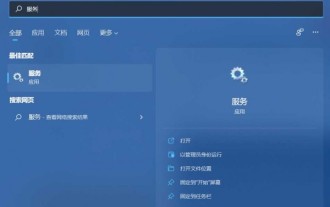
When we use computers, we are all connected to the Internet. Only with the Internet can we surf the Internet. Recently, many users have asked me how to solve the problem of Win11 unable to connect to the Internet? Users can directly open the best matching service application provided by the system to set it up. Let this site carefully introduce to users the solution to the problem that Win11 computers cannot access the Internet. Solution 1 for Win11 computers unable to access the internet: You can press the Win+S key combination, or click the search icon next to the bottom taskbar to open the Windows search window. Enter "service" in the search box, and then click to open the best matching service application given by the system. Method Two
 How to delete temporary Internet files
Dec 06, 2023 am 10:56 AM
How to delete temporary Internet files
Dec 06, 2023 am 10:56 AM
Steps to delete temporary Internet files: 1. Press win+r to open "Run", enter: %temp% command in the run dialog box, click OK or press Enter to open the user account temporary folder; 2. After opening the Temp folder Press the Ctrl+A keys, select all temporary files, right-click, and click "Delete" in the right-click menu; 3. If there are individual temporary files that cannot be deleted, restart the computer to delete them.




