 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Enhanced version of communication process design between mobile terminal and PHP server interface
Enhanced version of communication process design between mobile terminal and PHP server interface
Enhanced version of communication process design between mobile terminal and PHP server interface
As mentioned before: Mobile terminal and PHP server interface communication process design (basic version)
For the verification of api_token, its security can be further enhanced:
Enhancement 1:
Add 2 more There are two tables, one interface table and one authorization table. The design reference is as follows:
interface table
| field name | field type | note |
| api_id | int | Interface ID |
| api_name | varchar(120) | Interface name, with "/" as the dividing line, such as blog/Index/addBlog |
| api_domain | varchar(256) | Domain |
| is_enabled | tinyint(1) | is available 1: Available 0: Not available |
| add_time | int | Add time (stamp) |
(Note: Only core fields are listed, others Expand it again! ! )
Authorization table
| Comment | client_id | |
| Client ID | api_id | |
| api number | api_name | |
| Interface name, with "/" as the dividing line, such as blog/Index/addBlog | is_enabled | |
| is available 1: Available 0: Not available | add_time | |
| Add time (stamp) | expire_time | |
| Expiration time (stamp) | (Note: only core fields are listed, other Let’s expand it! ! ) |
1. Compare the api_token generated by the mobile terminal and the server. If they are not equal, an error will be returned directly. Otherwise, go to the next step;
2. According to the interface URL, assemble api_name, plus the client_id returned by the client as a parameter, search for the "authorization table" record, if the record exists and is valid (whether it is available, whether it has expired), it means that the permission verification is passed, and the interface data is returned, otherwise it is returned Error message;
Enhancement Part 2:For some very special interfaces, I don’t know how they are special and which ones are special. In short, I feel that the http request may be hijacked and the parameters passed may be tampered with. Let me give you an example: There is a direct transfer interface. I entered 5 yuan on the page, which means that I want to transfer 5 yuan to the other party. As a result, someone hijacked it during the HTTP transfer process. And changed it to 10,000 yuan, and the account was changed to the account of a "hacker". That's not a big loss. After thinking about it, there should be two solutions to this problem.
Option 1: Use https, this is not the case More to say, it is a relatively recognized security mechanism;
Option 2: Use digital signature, the implementation principle is as follows:
An http request, if you need to pass the following 3 parameters
Parameter name 1=Parameter value 1
Parameter name 2= Parameter value 2
Parameter name 3 = Parameter value 3
We can add another parameter, the parameter’s name is
identity_key(the name is not important), the value of this parameter is
The first few parameter values are in order The result is added and then encrypted.That is:
identity_key= md5('parameter value 1' + 'parameter value 2' + 'parameter value 3' + '
encryption key');So, the final parameters passed are: Parameter name 1=Parameter value 1
Parameter name 2=Parameter value 2
Parameter name 3=Parameter value 3
client_id=client_id value
identity_key=md5('Parameter value 1' + 'Parameter value 2' + 'Parameter value 3' + 'client_id value' + '
Encryption key')
After receiving the parameters, the server regenerates an identity_key according to the same encryption rules, the server's
identity_keyand the client Check the identity_key on the terminal. If they are not equal, it means it has been tampered with. You can figure out what to do next! The above introduces the enhanced version of the communication process design between the mobile terminal and the PHP server interface, including various aspects. I hope it will be helpful to friends who are interested in PHP tutorials.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1422
1422
 52
52
 1316
1316
 25
25
 1268
1268
 29
29
 1242
1242
 24
24
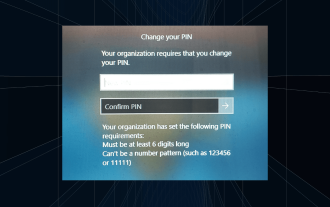 Solution: Your organization requires you to change your PIN
Oct 04, 2023 pm 05:45 PM
Solution: Your organization requires you to change your PIN
Oct 04, 2023 pm 05:45 PM
The message "Your organization has asked you to change your PIN" will appear on the login screen. This happens when the PIN expiration limit is reached on a computer using organization-based account settings, where they have control over personal devices. However, if you set up Windows using a personal account, the error message should ideally not appear. Although this is not always the case. Most users who encounter errors report using their personal accounts. Why does my organization ask me to change my PIN on Windows 11? It's possible that your account is associated with an organization, and your primary approach should be to verify this. Contacting your domain administrator can help! Additionally, misconfigured local policy settings or incorrect registry keys can cause errors. Right now
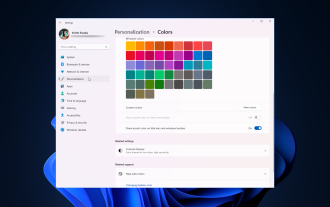 How to adjust window border settings on Windows 11: Change color and size
Sep 22, 2023 am 11:37 AM
How to adjust window border settings on Windows 11: Change color and size
Sep 22, 2023 am 11:37 AM
Windows 11 brings fresh and elegant design to the forefront; the modern interface allows you to personalize and change the finest details, such as window borders. In this guide, we'll discuss step-by-step instructions to help you create an environment that reflects your style in the Windows operating system. How to change window border settings? Press + to open the Settings app. WindowsI go to Personalization and click Color Settings. Color Change Window Borders Settings Window 11" Width="643" Height="500" > Find the Show accent color on title bar and window borders option, and toggle the switch next to it. To display accent colors on the Start menu and taskbar To display the theme color on the Start menu and taskbar, turn on Show theme on the Start menu and taskbar
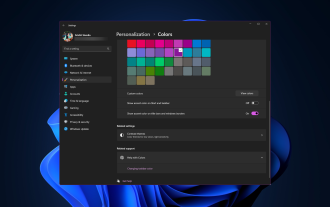 How to change title bar color on Windows 11?
Sep 14, 2023 pm 03:33 PM
How to change title bar color on Windows 11?
Sep 14, 2023 pm 03:33 PM
By default, the title bar color on Windows 11 depends on the dark/light theme you choose. However, you can change it to any color you want. In this guide, we'll discuss step-by-step instructions for three ways to change it and personalize your desktop experience to make it visually appealing. Is it possible to change the title bar color of active and inactive windows? Yes, you can change the title bar color of active windows using the Settings app, or you can change the title bar color of inactive windows using Registry Editor. To learn these steps, go to the next section. How to change title bar color in Windows 11? 1. Using the Settings app press + to open the settings window. WindowsI go to "Personalization" and then
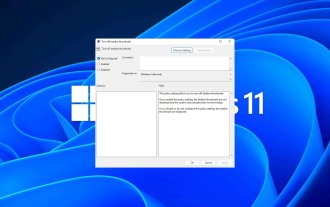 How to enable or disable taskbar thumbnail previews on Windows 11
Sep 15, 2023 pm 03:57 PM
How to enable or disable taskbar thumbnail previews on Windows 11
Sep 15, 2023 pm 03:57 PM
Taskbar thumbnails can be fun, but they can also be distracting or annoying. Considering how often you hover over this area, you may have inadvertently closed important windows a few times. Another disadvantage is that it uses more system resources, so if you've been looking for a way to be more resource efficient, we'll show you how to disable it. However, if your hardware specs can handle it and you like the preview, you can enable it. How to enable taskbar thumbnail preview in Windows 11? 1. Using the Settings app tap the key and click Settings. Windows click System and select About. Click Advanced system settings. Navigate to the Advanced tab and select Settings under Performance. Select "Visual Effects"
 OOBELANGUAGE Error Problems in Windows 11/10 Repair
Jul 16, 2023 pm 03:29 PM
OOBELANGUAGE Error Problems in Windows 11/10 Repair
Jul 16, 2023 pm 03:29 PM
Do you see "A problem occurred" along with the "OOBELANGUAGE" statement on the Windows Installer page? The installation of Windows sometimes stops due to such errors. OOBE means out-of-the-box experience. As the error message indicates, this is an issue related to OOBE language selection. There is nothing to worry about, you can solve this problem with nifty registry editing from the OOBE screen itself. Quick Fix – 1. Click the “Retry” button at the bottom of the OOBE app. This will continue the process without further hiccups. 2. Use the power button to force shut down the system. After the system restarts, OOBE should continue. 3. Disconnect the system from the Internet. Complete all aspects of OOBE in offline mode
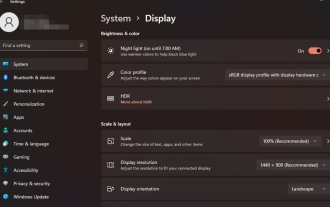 Display scaling guide on Windows 11
Sep 19, 2023 pm 06:45 PM
Display scaling guide on Windows 11
Sep 19, 2023 pm 06:45 PM
We all have different preferences when it comes to display scaling on Windows 11. Some people like big icons, some like small icons. However, we all agree that having the right scaling is important. Poor font scaling or over-scaling of images can be a real productivity killer when working, so you need to know how to customize it to get the most out of your system's capabilities. Advantages of Custom Zoom: This is a useful feature for people who have difficulty reading text on the screen. It helps you see more on the screen at one time. You can create custom extension profiles that apply only to certain monitors and applications. Can help improve the performance of low-end hardware. It gives you more control over what's on your screen. How to use Windows 11
 10 Ways to Adjust Brightness on Windows 11
Dec 18, 2023 pm 02:21 PM
10 Ways to Adjust Brightness on Windows 11
Dec 18, 2023 pm 02:21 PM
Screen brightness is an integral part of using modern computing devices, especially when you look at the screen for long periods of time. It helps you reduce eye strain, improve legibility, and view content easily and efficiently. However, depending on your settings, it can sometimes be difficult to manage brightness, especially on Windows 11 with the new UI changes. If you're having trouble adjusting brightness, here are all the ways to manage brightness on Windows 11. How to Change Brightness on Windows 11 [10 Ways Explained] Single monitor users can use the following methods to adjust brightness on Windows 11. This includes desktop systems using a single monitor as well as laptops. let's start. Method 1: Use the Action Center The Action Center is accessible
 How to Fix Activation Error Code 0xc004f069 in Windows Server
Jul 22, 2023 am 09:49 AM
How to Fix Activation Error Code 0xc004f069 in Windows Server
Jul 22, 2023 am 09:49 AM
The activation process on Windows sometimes takes a sudden turn to display an error message containing this error code 0xc004f069. Although the activation process is online, some older systems running Windows Server may experience this issue. Go through these initial checks, and if they don't help you activate your system, jump to the main solution to resolve the issue. Workaround – close the error message and activation window. Then restart the computer. Retry the Windows activation process from scratch again. Fix 1 – Activate from Terminal Activate Windows Server Edition system from cmd terminal. Stage – 1 Check Windows Server Version You have to check which type of W you are using



