PHP's true and false random numbers
This article mainly introduces the detailed explanation of pseudo-random numbers and true random numbers in PHP. This article first explains the related concepts of true random numbers and pseudo-random numbers, and gives a better pseudo-random number than using the mt_rand() function. A piece of example code. I hope to be helpful.
The first thing that needs to be stated is that computers do not generate absolutely random numbers. Computers can only generate "pseudo-random numbers". In fact, absolutely random numbers are just ideal random numbers. No matter how the computer develops, it will not generate a string of absolutely random numbers. Computers can only generate relatively random numbers, that is, pseudo-random numbers.
Pseudo-random numbers are not pseudo-random numbers. The "pseudo" here means regular, that is, the pseudo-random numbers generated by computers are both random and regular. How to understand it? The generated pseudo-random numbers sometimes follow certain rules, and sometimes they do not follow any rules; some of the pseudo-random numbers follow certain rules; the other part does not follow any rules. For example, "There are no two leaves with the same shape in the world." This points to the characteristics of things, that is, randomness, but the leaves of every tree have similar shapes, which is the commonality of things, that is, regularity. From this perspective, you will probably accept the fact that computers can only generate pseudo-random numbers but cannot generate absolutely random numbers.
First, let’s understand the concepts of true random numbers and pseudo-random numbers.
True random number generators: English: true random number generators, abbreviated as: TRNGs, are random numbers generated by unpredictable physical methods.
Pseudo-random number generators: English: pseudo-random number generators, abbreviated as: PRNGs, are generated by computers using certain algorithms.
Compare the pictures of random numbers generated by the two methods.
Random.org (uses atmospheric noise to generate random numbers, and atmospheric noise is generated by thunderstorms in the air) Random bitmap generated:

Random pictures generated by the rand() function of PHP under Windows:
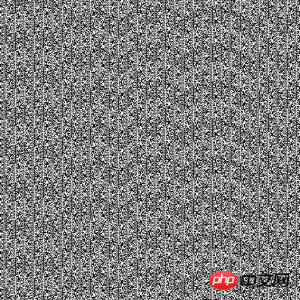
Obviously, the pictures generated by the latter pseudo-random number generator have such obvious stripes.
The code that uses PHP's rand random function to generate this picture is:
//需要开启gd库
header("Content-type: image/png");
$im = imagecreatetruecolor(512, 512)
or die("Cannot Initialize new GD image stream");
$white = imagecolorallocate($im, 255, 255, 255);
for ($y=0; $y<512; $y++) {
for ($x=0; $x<512; $x++) {
if (rand(0,1) === 1) {
imagesetpixel($im, $x, $y, $white);
}
}
}
imagepng($im);
imagedestroy($im);
In fact, not all pseudo-random number generators (PRNGs) are so bad. , it just happens that the rand() function of PHP under Windows is like this. If the same code is tested under Linux, the resulting picture will not show obvious stripes. Under Windows, if the mt_rand() function is used instead of the rand() function, the effect will be much better. This is because mt_rand() uses the Mersenne Twister algorithm to generate random numbers. The PHP documentation also says: mt_rand() can generate random values on average four times faster than the rand() provided by libc.
In addition, the Linux kernel (1.3.30 and above) includes a random number generator /dev/random, which is sufficient for many security purposes.
The following is an introduction to the principles of Linux’s random number generator:
The Linux operating system provides libraries that are inherently random (or at least have components with strong randomness) data. This data usually comes from the device driver. For example, a keyboard driver collects information about the time between two key presses and then fills this ambient noise into a random number generator library.
Random data is stored in an entropy pool (the Linux kernel maintains an entropy pool to collect environmental noise from device drivers and other sources. In theory, the data in the entropy pool is completely random and can be generated A sequence of true random numbers. To track the randomness of the data in the entropy pool, the kernel estimates the randomness of the data when adding it to the pool. This process is called entropy estimation. The entropy estimate describes the number of random numbers contained in the pool. A larger value means more randomness in the data in the pool), which is "stirred" every time new data comes in. This stirring is actually a mathematical transformation that helps improve randomness. As data is added to the entropy pool, the system estimates how many truly random bits it has obtained.
It is important to determine the total amount of randomness. The problem is that some quantities are often less random than they appear when first considered. For example, adding a 32-bit number representing the number of seconds since the last keystroke was not actually providing a new 32-bit random information, since most keystrokes are close together.
After the bytes are read from /dev/random, the entropy pool uses the MD5 algorithm to hash the password, and the individual bytes in the hash are converted into numbers and then returned.
If there are no randomness bits available in the entropy pool, /dev/random waits until there is enough randomness in the pool, without returning a result. This means that if you use /dev/random to generate many random numbers, you will find that it is too slow to be practical. We often see /dev/random generate dozens of bytes of data and then produce no results for many seconds.
幸运的是有熵池的另一个接口可以绕过这个限制:/dev/urandom。即使熵池中没有随机性可用,这个替代设备也总是返回随机数。如果您取出许 多数而不给熵池足够的时间重新充满,就再也不能获得各种来源的合用熵的好处了;但您仍可以从熵池的 MD5 散列中获得非常好的随机数!这种方式的问题是,如果有任何人破解了 MD5 算法,并通过查看输出了解到有关散列输入的信息,那么您的数就会立刻变得完全可预料。大多数专家都认为这种分析从计算角度来讲是不可行的。然而,仍然认为 /dev/urandom 比 /dev/random 要“不安全一些”(并通常值得怀疑)。
Windows下没有/dev/random可用,但可以使用微软的“capicom.dll”所提供的CAPICOM.Utilities 对象。
以下是使用PHP时比用mt_rand()函数产生更好的伪随机数的一段例子代码:
<?php
// get 128 pseudorandom bits in a string of 16 bytes
$pr_bits = '';
// Unix/Linux platform?
$fp = @fopen('/dev/urandom','rb');
if ($fp !== FALSE) {
$pr_bits .= @fread($fp,16);
@fclose($fp);
}
// MS-Windows platform?
if (@class_exists('COM')) {
try {
$CAPI_Util = new COM('CAPICOM.Utilities.1');
$pr_bits .= $CAPI_Util->GetRandom(16,0);
// if we ask for binary data PHP munges it, so we
// request base64 return value. We squeeze out the
// redundancy and useless ==CRLF by hashing...
if ($pr_bits) { $pr_bits = md5($pr_bits,TRUE); }
} catch (Exception $ex) {
// echo 'Exception: ' . $ex->getMessage();
}
}
if (strlen($pr_bits) < 16) {
// do something to warn system owner that
// pseudorandom generator is missing
}
?>所以PHP要产生真随机数 还是要调用外部元素来支持的!
相关推荐:
PHP函数:生成N个不重复的随机数,php 随机数_PHP教程
The above is the detailed content of PHP's true and false random numbers. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1666
1666
 14
14
 1425
1425
 52
52
 1324
1324
 25
25
 1272
1272
 29
29
 1251
1251
 24
24
 PHP and Python: Comparing Two Popular Programming Languages
Apr 14, 2025 am 12:13 AM
PHP and Python: Comparing Two Popular Programming Languages
Apr 14, 2025 am 12:13 AM
PHP and Python each have their own advantages, and choose according to project requirements. 1.PHP is suitable for web development, especially for rapid development and maintenance of websites. 2. Python is suitable for data science, machine learning and artificial intelligence, with concise syntax and suitable for beginners.
 PHP in Action: Real-World Examples and Applications
Apr 14, 2025 am 12:19 AM
PHP in Action: Real-World Examples and Applications
Apr 14, 2025 am 12:19 AM
PHP is widely used in e-commerce, content management systems and API development. 1) E-commerce: used for shopping cart function and payment processing. 2) Content management system: used for dynamic content generation and user management. 3) API development: used for RESTful API development and API security. Through performance optimization and best practices, the efficiency and maintainability of PHP applications are improved.
 PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP: A Key Language for Web Development
Apr 13, 2025 am 12:08 AM
PHP is a scripting language widely used on the server side, especially suitable for web development. 1.PHP can embed HTML, process HTTP requests and responses, and supports a variety of databases. 2.PHP is used to generate dynamic web content, process form data, access databases, etc., with strong community support and open source resources. 3. PHP is an interpreted language, and the execution process includes lexical analysis, grammatical analysis, compilation and execution. 4.PHP can be combined with MySQL for advanced applications such as user registration systems. 5. When debugging PHP, you can use functions such as error_reporting() and var_dump(). 6. Optimize PHP code to use caching mechanisms, optimize database queries and use built-in functions. 7
 PHP vs. Python: Understanding the Differences
Apr 11, 2025 am 12:15 AM
PHP vs. Python: Understanding the Differences
Apr 11, 2025 am 12:15 AM
PHP and Python each have their own advantages, and the choice should be based on project requirements. 1.PHP is suitable for web development, with simple syntax and high execution efficiency. 2. Python is suitable for data science and machine learning, with concise syntax and rich libraries.
 The Enduring Relevance of PHP: Is It Still Alive?
Apr 14, 2025 am 12:12 AM
The Enduring Relevance of PHP: Is It Still Alive?
Apr 14, 2025 am 12:12 AM
PHP is still dynamic and still occupies an important position in the field of modern programming. 1) PHP's simplicity and powerful community support make it widely used in web development; 2) Its flexibility and stability make it outstanding in handling web forms, database operations and file processing; 3) PHP is constantly evolving and optimizing, suitable for beginners and experienced developers.
 PHP vs. Other Languages: A Comparison
Apr 13, 2025 am 12:19 AM
PHP vs. Other Languages: A Comparison
Apr 13, 2025 am 12:19 AM
PHP is suitable for web development, especially in rapid development and processing dynamic content, but is not good at data science and enterprise-level applications. Compared with Python, PHP has more advantages in web development, but is not as good as Python in the field of data science; compared with Java, PHP performs worse in enterprise-level applications, but is more flexible in web development; compared with JavaScript, PHP is more concise in back-end development, but is not as good as JavaScript in front-end development.
 PHP and Python: Code Examples and Comparison
Apr 15, 2025 am 12:07 AM
PHP and Python: Code Examples and Comparison
Apr 15, 2025 am 12:07 AM
PHP and Python have their own advantages and disadvantages, and the choice depends on project needs and personal preferences. 1.PHP is suitable for rapid development and maintenance of large-scale web applications. 2. Python dominates the field of data science and machine learning.
 PHP and Python: Different Paradigms Explained
Apr 18, 2025 am 12:26 AM
PHP and Python: Different Paradigms Explained
Apr 18, 2025 am 12:26 AM
PHP is mainly procedural programming, but also supports object-oriented programming (OOP); Python supports a variety of paradigms, including OOP, functional and procedural programming. PHP is suitable for web development, and Python is suitable for a variety of applications such as data analysis and machine learning.




