本篇文章给大家分享了php绕过open_basedir限制操作文件的三种方法以及相关技巧,有兴趣的朋友参考学习下。
0x00 预备知识
关于open_basedir
open_basedir是php.ini中的一个配置选项它可将用户访问文件的活动范围限制在指定的区域,假设open_basedir=/home/wwwroot/home/web1/:/tmp/,那么通过web1访问服务器的用户就无法获取服务器上除了/home/wwwroot/home/web1/和/tmp/这两个目录以外的文件。注意用open_basedir指定的限制实际上是前缀,而不是目录名。举例来说: 若"open_basedir = /dir/user", 那么目录 "/dir/user" 和 "/dir/user1"都是可以访问的。所以如果要将访问限制在仅为指定的目录,请用斜线结束路径名。
关于符号链接
符号链接又叫软链接,是一类特殊的文件,这个文件包含了另一个文件的路径名(绝对路径或者相对路径)。
立即学习“PHP免费学习笔记(深入)”;
路径可以是任意文件或目录,可以链接不同文件系统的文件。在对符号文件进行读或写操作的时候,系统会自动把该操作转换为对源文件的操作,但删除链接文件时,系统仅仅删除链接文件,而不删除源文件本身。
0x01 命令执行函数
由于open_basedir的设置对system等命令执行函数是无效的,所以我们可以使用命令执行函数来访问限制目录。
我们首先创建一个目录
/home/puret/test/
且在该目录下新建一个1.txt 内容为abc
nano 1.txt
再在该目录下创建一个目录命名为b
mkdir b
并且在该目录下创建一个1.php文件内容为
1 2 3 |
|
且在php.ini中设置好我们的open_basedir
open_basedir = /home/puret/test/b/
我们尝试执行1.php看看open_basedir是否会限制我们的访问
执行效果如图
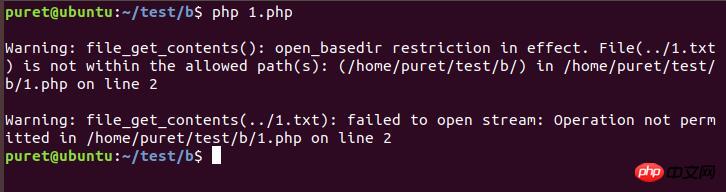
很明显我们无法直接读取open_basedir所规定以外的目录文件。
接下来我们用system函数尝试绕open_basedir的限制来删除1.txt
编辑1.php为
1 2 3 |
|
先来看看执行1.php之前的文件情况

执行1.php之后
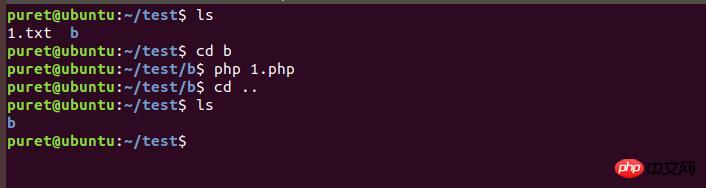
成功通过命令执行函数绕过open_basedir来删除文件。
由于命令执行函数一般都会被限制在disable_function当中,所以我们需要寻找其他的途径来绕过限制。
0x02 symlink()函数
我们先来了解一下symlink函数
bool symlink ( string $target , string $link )
symlink函数将建立一个指向target的名为link的符号链接,当然一般情况下这个target是受限于open_basedir的。
由于早期的symlink不支持windows,我的测试环境就放在Linux下了。
测试的PHP版本是5.3.0,其他的版本大家自测吧。
在Linux环境下我们可以通过symlink完成一些逻辑上的绕过导致可以跨目录操作文件。
我们首先在/var/www/html/1.php中 编辑1.php的内容为
1 2 3 4 5 6 7 8 9 10 11 12 13 |
|
接着在/var/www/中新建一个1.txt文件内容为
"abc"
再来设置一下我们的open_basedir
open_basedir = /var/www/html/
在html目录下编辑一个php脚本检验一下open_basedir
1 2 3 |
|
执行看下。
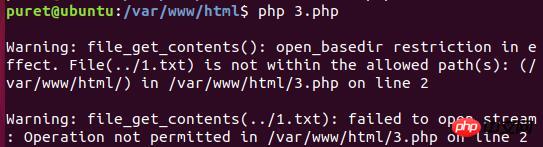
意料之中,文件无法访问。
我们执行刚才写好的脚本,1.php
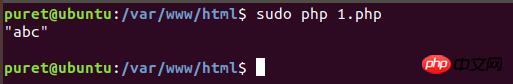
可以看到成功读取到了1.txt的文件内容,逃脱了open_basedir的限制
问题的关键就在于
symlink("tmplink/../../1.txt","exploit");
此时tmplink还是一个符号链接文件,它指向的路径是c/d,因此exploit指向的路径就变成了
c/d/../../1.txt
由于这个路径在open_basedir的范围之内所以exploit成功建立了。
之后我们删除tmplink符号链接文件再新建一个同名为tmplink的文件夹,这时exploit所指向的路径为
tmplink/../../
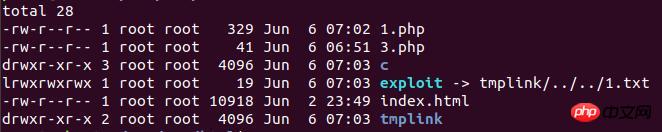
由于这时候tmplink变成了一个真实存在的文件夹所以tmplink/../../变成了1.txt所在的目录即/var/www/
然后再通过访问符号链接文件exploit即可直接读取到1.txt的文件内容
当然,针对symlink()只需要将它放入disable_function即可解决问题,所以我们需要寻求更多的方法。
0x03 glob伪协议
glob是php自5.3.0版本起开始生效的一个用来筛选目录的伪协议,由于它在筛选目录时是不受open_basedir的制约的,所以我们可以利用它来绕过限制,我们新建一个目录在/var/www/下命名为test
并且在/var/www/html/下新建t.php内容为
1 2 3 4 5 6 7 8 9 |
|
执行结果如图:
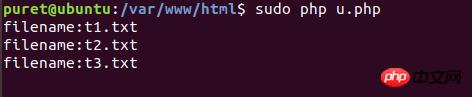
成功躲过open_basedir的限制读取到了文件。
以上就是本文的全部内容,希望对大家的学习有所帮助,更多相关内容请关注PHP中文网!
相关推荐:
关于ThinkPHP中Common/common.php文件常用函数的功能分析
PHP的Cannot use object of type stdClass as array in错误的解决办法
以上就是如何通过PHP绕过open_basedir限制操作文件的详细内容,更多请关注php中文网其它相关文章!

PHP怎么学习?PHP怎么入门?PHP在哪学?PHP怎么学才快?不用担心,这里为大家提供了PHP速学教程(入门到精通),有需要的小伙伴保存下载就能学习啦!

Copyright 2014-2025 https://www.php.cn/ All Rights Reserved | php.cn | 湘ICP备2023035733号