 Operation and Maintenance
Operation and Maintenance
 Windows Operation and Maintenance
Windows Operation and Maintenance
 How to close ports 135, 139, 445, 593, 1025, etc.
How to close ports 135, 139, 445, 593, 1025, etc.
How to close ports 135, 139, 445, 593, 1025, etc.
Operation essentials: Close the ports and prevent network viruses from accessing these ports to ensure computer security and reduce the impact of viruses on Internet speed.
Recently, it was discovered that some people are infected with a new network worm virus. This virus cannot be killed using the shock wave virus killing tool. Please upgrade the anti-virus software virus database on your computer as soon as possible and scan the hard disk while disconnecting the computer network. , check and kill viruses. Users who have installed firewall software, please
Block TCP 135, 139, 445, 593, 1025 ports and UDP 135, 137, 138, 445
In addition, you can also block the backdoor ports of some popular viruses, such as TCP 2745, 3127, 6129
ports, so you can also temporarily block incoming connections to those ports.
At present, many viruses will guess the username and password of computer users and brute force crack them. For the security of your computer, please set a secure password for your computer that is not easy to guess.
Operation steps
Open the "Control Panel" (the connection to open the "Control Panel" can be found in the "Settings" menu of "My Computer" or the "Start Menu")
In the "Control Panel" Find "Administrative Tools".
Double-click to open "Administrative Tools" and find "Local Security Policy".
Double-click to open "Local Security Policy" and find "IP Security Policy", as shown in Figure 1. 
Figure 1: Find "IP Security Policy" in "Local Security Policy"
Right-click the blank space in the right pane, and select "Create IP Security" in the pop-up shortcut menu Policy" 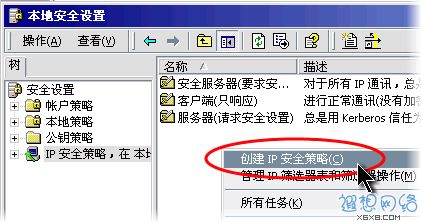
Figure 2: Create a new policy
Click the "Next" button in the wizard, go to the second page to name the new security policy, or directly Click "Next" again. When you reach the "Secure Communication Request", "Activate Default Corresponding Rules" is selected by default. Please click this option box with the mouse to change the selected
status to the unselected state, as shown in Figure 3, and then Click "Next". 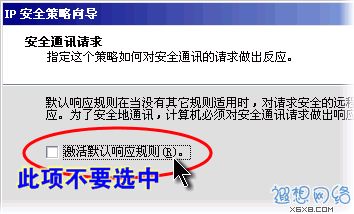 Figure 3: Do not activate the default selected state
Figure 3: Do not activate the default selected state
Click the "Finish" button and "Edit
Properties", as shown in Figure 4. 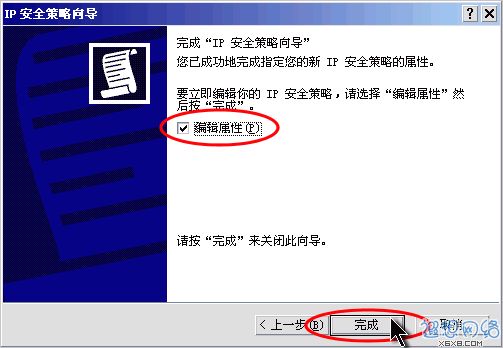 Figure 4: Complete the new strategy addition
Figure 4: Complete the new strategy addition
In the "Properties" dialog box, check whether "Use the Add Wizard" is selected. If it is selected, please click it with the mouse to make it become unselected and click the "Add" button. As shown in Figure 5. 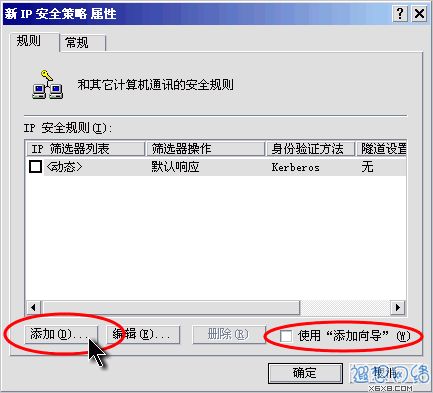 Figure 5: Click the "Add" button to add a new connection rule
Figure 5: Click the "Add" button to add a new connection rule
In the "New Rule Properties" dialog box, click the "Add" button, as shown in Figure 6. 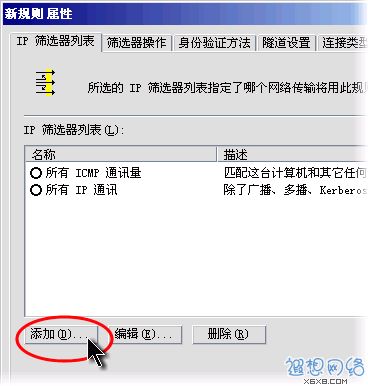 Figure 6: Add new rule
Figure 6: Add new rule
In the IP policy list, first uncheck "Use Add Wizard", and then click the "Add" button. As shown in Figure 7. 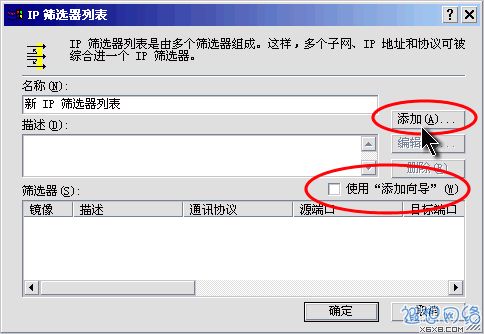 Figure 7: Add a new filter
Figure 7: Add a new filter
Come to the "Filter Properties" dialog box. The first thing you see is addressing. Select "Any IP Address" for the source address and select "Any IP Address" for the destination address. "My IP address", as shown in Figure 8. 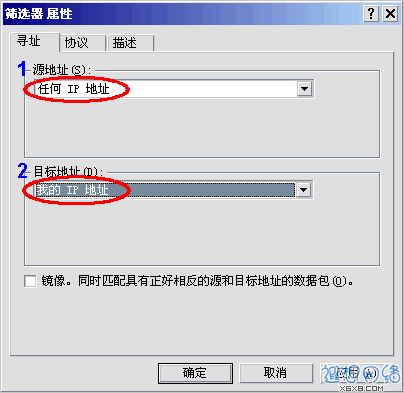 Figure 8: Filter Properties
Figure 8: Filter Properties
Click the "Protocol" tab, first select "TCP" in the
drop-down list under "Select Protocol Type", and then The gray "Set Protocol Port" will turn colored, then enter "135" in the text box under "To this port" and click the "OK" button. As shown in Figure 9. 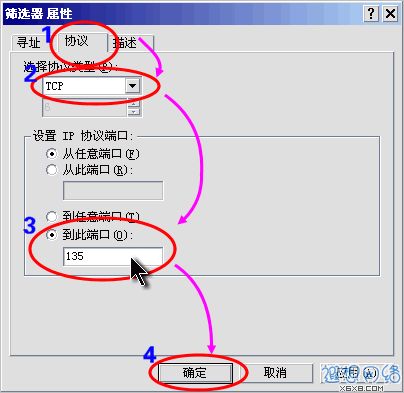 Figure 9: Add a filter to block TCP 135 (RPC) port
Figure 9: Add a filter to block TCP 135 (RPC) port
Return to the filter list dialog box, you can see that a policy has been added, repeat steps 11, 12, 13. Continue to add TCP 137, 139, 445, 593 ports and UDP
135, 139, 445 ports. Because some worms currently scan your computer for TCP 1025, 2745, 3127, 6129
ports, so you can also temporarily add blocking policies for these ports, discard data packets accessing these ports, and do not respond, thereby reducing the impact on your Internet access. Click the Close button. As shown in Figure 10. 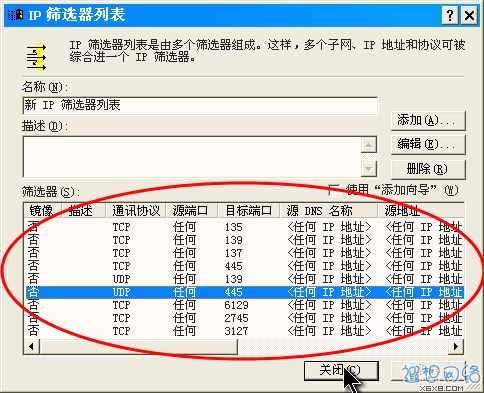
Figure 10: Repeat the steps to add each port filter
In the "New Rule Properties" dialog box, click "New IP Filter List", a dot will be added to the circle on the left, indicating Already activated, then click the "Filter Operations" tab, as shown in Figure 11. 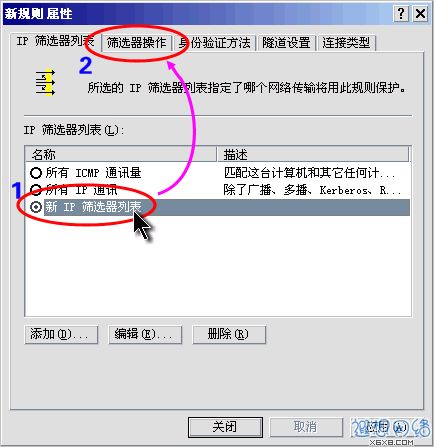
Figure 11: Activate "New IP Filter List"
In the "Filter Action" tab, first leave "Use Add Wizard" unchecked, and then click "Add" button. As shown in Figure 12. 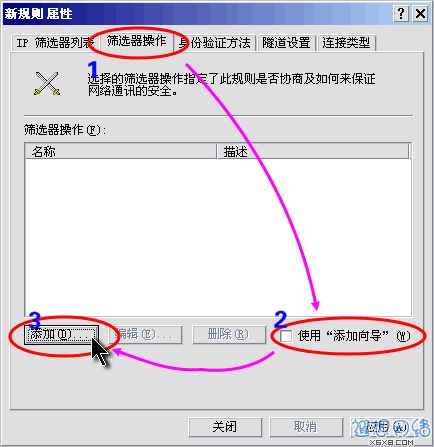
Figure 12: Add filter operation
In the "Security Measures" tab of "New Filter Operation Properties", select "Block", and then click the "OK" button. As shown in Figure 13. 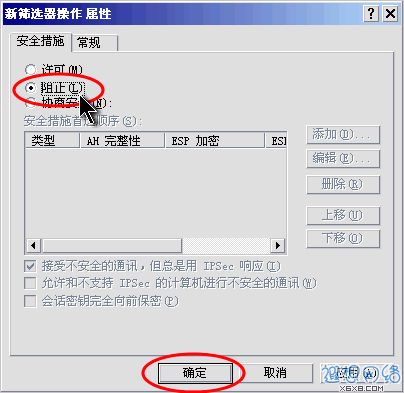
Figure 13: Add the "Block" operation
In the "New Rule Properties" dialog box, you can see that there is a new "Filter Operation", click this "New Filter" "Operation", a dot will be added to the circle to the left of it, indicating that it has been activated, and then you can click the "Close" button to close the dialog box. As shown in Figure 14. 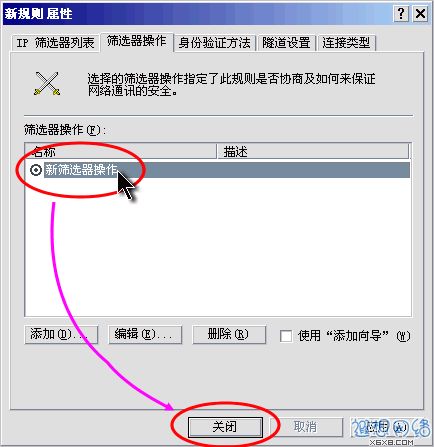
Figure 14: Activate "New Filter Action"
Return to the "New IP Security Policy Properties" dialog box and press the "Close" button to close the dialog box. As shown in Figure 15. 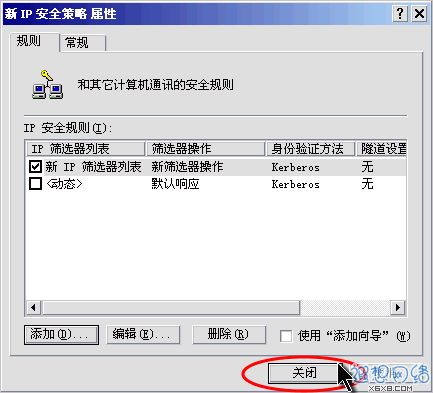
Figure 15: Close the "New IP Security Policy Properties" dialog box
Finally, return to the "Local Security Policy" window, right-click the newly added IP security policy, and then select "Assign", as shown in Figure 16. 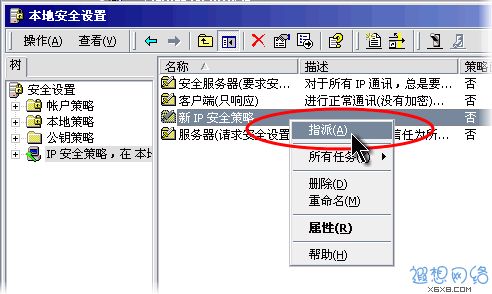
Figure 16: Assign a new IP security policy
At this time, your computer already has the ability to temporarily protect against RPC worms.
Finally, please visit the RPC vulnerability and MS04-011 security vulnerability notice patch download webpage provided here to download the patch suitable for your computer, and then go to the Windows Update website to download it for your computer Latest updatepatch for Windows.
The above is the detailed content of How to close ports 135, 139, 445, 593, 1025, etc.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
![Soundbar detected as monitor screen on Windows PC [Fix]](https://img.php.cn/upload/article/000/465/014/170835733166289.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) Soundbar detected as monitor screen on Windows PC [Fix]
Feb 19, 2024 pm 11:42 PM
Soundbar detected as monitor screen on Windows PC [Fix]
Feb 19, 2024 pm 11:42 PM
On Windows PCs, some users have discovered that the Soundbar is recognized as a monitor when connected to the HDMI port. This may cause some confusion, but the solution is not the only one. How to Connect a Soundbar to a PC via HDMI Most soundbars use HDMI, optical, or 3.5mm audio connections. If your soundbar only supports HDMI connections, it must be connected to an HDMI port labeled HDMIARC. Many TVs or monitors are usually equipped with multiple HDMI ports, one of which should support the ARC protocol that complies with the HDMI standard. In other words, HDMI is an interface used to transmit audio and video. If the device does not have an HDMI port, consider using a monitor.
 How to check whether the remote server port is open in Linux
Mar 21, 2023 am 09:50 AM
How to check whether the remote server port is open in Linux
Mar 21, 2023 am 09:50 AM
How to check whether the remote server port is open in Linux: 1. Use the "nmap ip -p port" command to check whether the port is open. The specific command is such as "nmap 172.17.193.18 -p 5902"; 2. Use the "nc -v ip port" command Check whether the port is open. The specific command is "nc -v 172.17.193.18 5902".
 What ports are com1 and com2?
Aug 25, 2022 am 10:53 AM
What ports are com1 and com2?
Aug 25, 2022 am 10:53 AM
com1 and com2 are serial communication ports, referred to as serial ports; a motherboard generally has two COM serial interfaces, which are usually used to connect mice, which are communication devices. The serial interface refers to the sequential transmission of data bit by bit, which is characterized by communication The circuit is simple, and only a pair of transmission lines can achieve two-way communication.
 How to close port 445 in Win11
Jul 04, 2023 pm 12:17 PM
How to close port 445 in Win11
Jul 04, 2023 pm 12:17 PM
How to close port 445 in Win11? Port No. 445 is a TCP port, a shared folder and printer port, which provides file or printer sharing services within the LAN. Recently, some Win11 users want to close port 445, so how should they do it? Many friends don’t know how to operate in detail. The editor below has compiled the detailed operations for closing port 445 in Win11. If you are interested, follow the editor to read below! Detailed operation of closing port 445 in Win11 1. First, press the Win+S key combination, or click the search icon on the bottom taskbar, open the Windows search window, enter Windows Firewall at the top, and then click the best option given by the system.
 Your iPhone won't charge after iOS 17 update? Here's what you can do
Sep 21, 2023 pm 11:41 PM
Your iPhone won't charge after iOS 17 update? Here's what you can do
Sep 21, 2023 pm 11:41 PM
What is the cause of iOS17 charging problem? There are several possible reasons why your iPhone may not be charging after updating to iOS17. One possibility is that there is a bug in the software update. Apple is usually quick to fix bugs in iOS updates, so if you're having charging issues it's worth checking to see if a new update is available. Another possibility is that there is a problem with the charging cable or adapter. If you're using a third-party charging cable or adapter, make sure it's certified by Apple. How to Fix iPhone Not Charging Issue Here are some tips on how to fix iPhone not charging issue after iOS17 update: Restart your Apple phone This usually resolves minor issues that may be the root cause of iOS17 charging issue
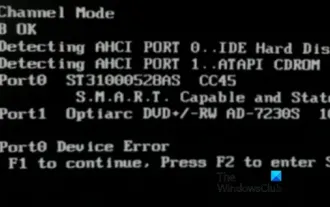 Fix AHCI Port 0 Device Error on Windows Computer
Feb 19, 2024 pm 12:45 PM
Fix AHCI Port 0 Device Error on Windows Computer
Feb 19, 2024 pm 12:45 PM
If you encounter an AHCI port 0 device error every time you start your computer, you need to follow the methods provided in this article to solve the problem. What is AHCI port 0 device error? AHCI device errors are reported by the BIOS. SMART has indicated that the hard drive on port 0 is faulty and may not be accessible. The hard drive may have problems at any time. If it is a desktop computer, it is recommended to try changing the hard drive connection port. If the problem persists, it may be a problem with the hard drive itself. You can run a disk check tool, disable the failed hard drive and check the ports to resolve this issue. Fixing AHCI Port 0 Device Errors on Windows Computers Typically, AHCI Port0 device errors do not originate from operating system issues, but rather from the hard drive failing on port 0.
 What to do if there is an error in docker mapping port
Oct 21, 2022 pm 03:29 PM
What to do if there is an error in docker mapping port
Oct 21, 2022 pm 03:29 PM
Solution to docker mapping port error: 1. Switch to the root account; 2. Use the "netstat -nap" command to check the pid of the program running; 3. Use the "kill -9 2901 su u260517" command to kill the program and switch the program. .
 How to use LSOF to monitor ports in real time
Mar 20, 2024 pm 02:07 PM
How to use LSOF to monitor ports in real time
Mar 20, 2024 pm 02:07 PM
LSOF (ListOpenFiles) is a command line tool mainly used to monitor system resources similar to Linux/Unix operating systems. Through the LSOF command, users can get detailed information about the active files in the system and the processes that are accessing these files. LSOF can help users identify the processes currently occupying file resources, thereby better managing system resources and troubleshooting possible problems. LSOF is powerful and flexible, and can help system administrators quickly locate file-related problems, such as file leaks, unclosed file descriptors, etc. Via LSOF Command The LSOF command line tool allows system administrators and developers to: Determine which processes are currently using a specific file or port, in the event of a port conflict





