So starten Sie schnell mit Nmap
1. Installation
https://nmap.org/, keine Notwendigkeit, auf Details einzugehen
2. Zielmaschinenkonstruktion
Dieser Artikel verwendet die Zielmaschine für das OWASP Broken Web Applications Project
https://sourceforge .net/projects /owaspbwa/
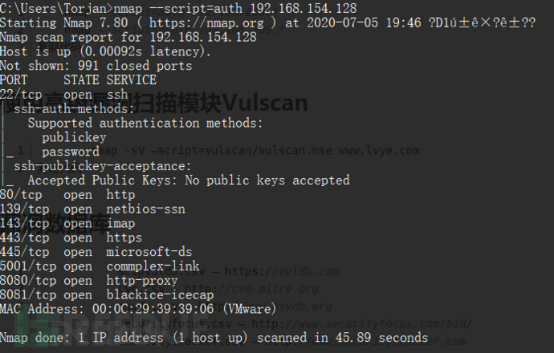
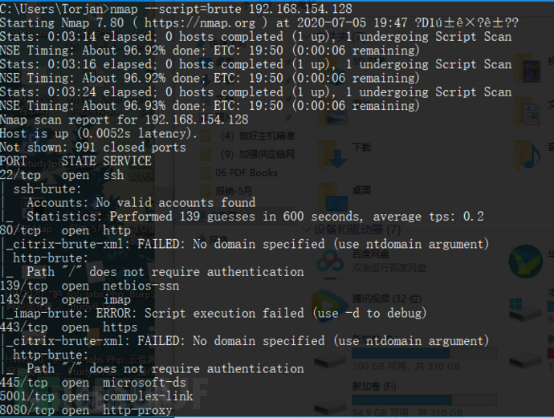
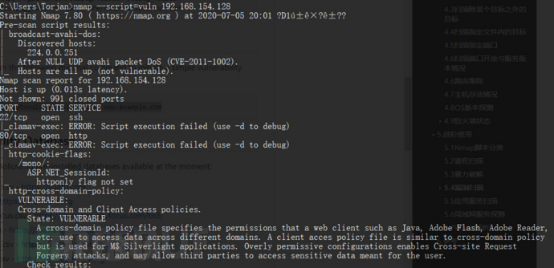
Zieladresse 1: 192.168.154.128
Zieladresse 2: 192.168.3.7
3. Befehlszeile
C:\Users\Torjan>nmap --helpNmap 7.80 ( https://nmap.org )Usage: nmap [Scan Type(s)] [Options] {target specification}TARGET SPECIFICATION:Can pass hostnames, IP addresses, networks, etc.Ex: scanme.nmap.org, microsoft.com/24, 192.168.0.1; 10.0.0-255.1-254-iL: Input from list of hosts/networks,"从文件中导入目标主机或目标网段"-iR: Choose random targets,"随机选择目标主机"--exclude: Exclude hosts/networks,"后面跟的主机或网段将不在扫描范围内"--excludefile: Exclude list from file,"后面跟的文件中的主机或网段将不在扫描范围内HOST DISCOVERY:["主机发现"]-sL:List Scan,"List Scan(列表扫描),仅列举指定目标的IP,不进行主机发现"-sn: Ping Scan - disable port scan,"Ping Scan,只进行主机发现,不进行端口扫描" -Pn: Treat all hosts as online -- skip host discovery,"将所有指定的主机视作已开启,跳过主机发现的过程。"-PS/PA/PU/PY[portlist]: TCP SYN/ACK, UDP or SCTP discovery to given ports,"使用 TCP SYN/ACk或SCTP INIT/ECHO方式来发现。"-PE/PP/PM: ICMP echo, timestamp, and netmask request discovery probes,"使用 ICMP echo、 timestamp、 netmask请求包发现主机"-PO[protocol list]: IP Protocol Ping,"使用IP协议包探测对方主机是否开启。"-n/-R: Never do DNS resolution/Always resolve [default: sometimes],"-n表示不进行DNS解析;-R表示总是进行DNS解析。"--dns-servers: Specify custom DNS servers,"指定DNS服务器。"--system-dns: Use OS s DNS resolver,"指定使用系统的DNS服务器。"--traceroute: Trace hop path to each host,"追踪每个路由节点。SCAN TECHNIQUES:["扫描参数"]-sS/sT/sA/sW/sM: TCP SYN/Connect()/ACK/Window/Maimon scans,"指定使用 TCP SYN/Connect()/Ack/Window/Maimon scans的方式对目标主机进行扫描。"-sU: UDP Scan,"指定使用UDP扫描的方式确定目标主机的UDP端口状况。"-sN/sF/sX: TCP Null, FIN, and Xmas scans,"指定使用 TCP Null/FiN/Xmas scans秘密扫描的方式协助探测对方的TCP端口状态。"--scanflags: Customize TCP scan flags,"定制TCP包的flags"-sI: Idle scan,"指定使用 Idle scan的方式扫描目标主机(前提是需要找到合适的僵尸主机zombie host)。"-sY/sZ: SCTP INIT/COOKIE-ECHO scans,"使用 SCTP INIT/COOKIE-ECHO扫描SCTP协议端口的开放情况"-sO: IP protocol scan,"使用 IP protocol扫描确定目标机支持的协议类型。"-b: FTP bounce scan,"使用 FTP bounce scan扫描方式。PORT SPECIFICATION AND SCAN ORDER:["端口扫描参数和顺序"]-p: Only scan specified ports,":扫描指定的端口"Ex("例如"): -p22; -p1-65535; -p U:53,111,137,T:21-25,80,139,8080,S:9--exclude-ports: Exclude the specified ports from scanning,"不扫描的端口"-F: Fast mode - Scan fewer ports than the default scan,"(快速模式),仅扫描TOP100的端口"-r: Scan ports consecutively - dont randomize,"不进行端口随机打乱的操作(如无该参数,Nmap会将要扫描的端口以随机顺序的方式进行扫描,让Nmap的扫描不易被对方防火墙检测到),即顺序扫描。"--top-ports: Scanmost common ports,"扫描开放概率最高的 number个端口(Nmap的作者曾做过大规模的互联网扫描,以此统计网络上各种端口可能开放的概率,并排列出最有可能开放端口的列表,具体可以参见nmap- -services文件。默认情况下,Nmap会扫描最有可能的1000个TCP端口)。"--port-ratio: Scan ports more common than,"扫描指定频率以上的端口。与上述top-ports类似,这里以概率作为参数,概率大于port--ratio的端口才被扫描。显然参数必须在0~1之间,想了解具体的概率范围可以查看nmap- -services文件。SERVICE/VERSION DETECTION:["版本探测"]-sV: Probe open ports to determine service/version info,"指定让Nmap进行版本侦测。"--version-intensity: Set from 0 (light) to 9 (try all probes),"指定版本侦测的强度(0~9),默认为7。数值越高,探测出的服务越准确,但是运行时间会比较长。"--version-light: Limit to most likely probes (intensity 2),"指使用轻量级侦测方式(intensity2)"--version-all: Try every single probe (intensity 9),"尝试使用所有的 probes进行侦测( intensity9)。"--version-trace: Show detailed version scan activity (for debugging),"显示出详细的版本侦测过程信息。SCRIPT SCAN:["扫描脚本"]-sC/--script=default: "使用默认的脚本进行扫描。"--script=:is a comma separated list of,"使用某个脚本进行扫描。"directories, script-files or script-categories--script-args=: provide arguments to scripts,"该参数用于传递脚本里的参数key是参数名,该参数对应valuel这个值。如有更多的参数,使用逗号连接。"--script-args-file=filename: provide NSE script args in a file,"使用文件为脚本提供参数。"--script-trace: Show all data sent and received,"如设置该参数,则显示脚本执行过程中发送与接收的数据。"--script-updatedb: Update the script database."在Nmap 的scripts目录里有一个db文件,该文件保存了当前Nmap可用的脚本,类似于一个小型数据库,如果我们开启Nmap并调用了此参数,则Nmap会自行扫描scripts扫描目录中的扩展脚本,进行数据库更新"--script-help=: Show help about scripts."查看扫描脚本帮助文档"is a comma-separated list of script-files orscript-categoriesOS DETECTION:["系统探测"]-O: Enable OS detection,"系统探测"--osscan-limit: Limit OS detection to promising targets,"只对满足“同时具备状态为Open和closed的端口”的主机进行操作系统探测"--osscan-guess: Guess OS more aggressively,"猜测最有可能的系统版本TIMING AND PERFORMANCE:["时间与性能"]Options which takeare in seconds, or append 'ms' (milliseconds),'s' (seconds), 'm' (minutes), or 'h' (hours) to the value (e.g. 30m)."时间单位说明"-T: Set timing template (higher is faster),"时间扫描级别,数字越高越快"--min-hostgroup/max-hostgroup: Parallel host scan group sizes,"指定并行扫描的主机数量,每次最大或者最小扫描多少个主机"--min-parallelism/max-parallelism: Probe parallelization--min-rtt-timeout/max-rtt-timeout/initial-rtt-timeout: Specifiesprobe round trip time.--max-retries: Caps number of port scan probe retransmissions."最大的探测次数"--host-timeout: Give up on target after this long,"超时时间"--scan-delay/--max-scan-delay: Adjust delay between probes,"扫描探测的延时时间/间隔时间"--min-rate: Send packets no slower thanper second,"每秒发包不少于number"--max-rate: Send packets no faster thanper second,"每秒发包不多于numberFIREWALL/IDS EVASION AND SPOOFING:["防火墙/IDS绕过和欺骗"]-f; --mtu: fragment packets (optionally w/given MTU),"分片"-D: Cloak a scan with decoys,"伪造源地址,但并不是正真的源地址,而是增加一些噪声源,用以迷惑目标ip,增加对方的分析难度。"-S: Spoof source address,"源地址伪造"-e: Use specified interface,"使用特殊接口"-g/--source-port: Use given port number,"使用指定源端口"--proxies: Relay connections through HTTP/SOCKS4 proxies,"代理"--data: Append a custom payload to sent packets,"添加自定义数据字段,但字段必须是16进制"--data-string: Append a custom ASCII string to sent packets,"添加ASCII码发送数据"--data-length: Append random data to sent packets,"数据长度"--ip-options: Send packets with specified ip options,"特殊IP选项"--ttl: Set IP time-to-live field,"设置IP存活时间"--spoof-mac: Spoof your MAC address,"MAC欺骗"--badsum: Send packets with a bogus TCP/UDP/SCTP checksumOUTPUT:,"差错校验"-oN/-oX/-oS/-oG: Output scan in normal, XML, s|<ript><h3 id="Einfache-schnelle-Verwendung">4. Einfache schnelle Verwendung</h3>
<p>Ziel 1: 192 .168.154.128</p>
<p> Ziel Drohne 2IP: 192.168.3.7</p>
<h4 id="Ein-einzelnes-Ziel-scannen">4.1 Ein einzelnes Ziel scannen </h4>
<pre class="brush:php;toolbar:false">nmap 192.168.154.128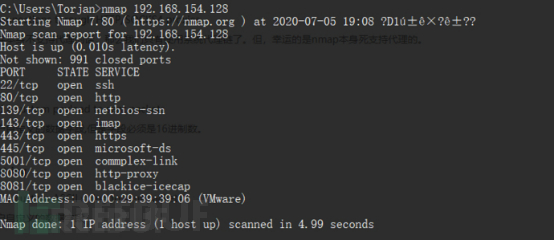
4.2 Mehrere Ziele scannen
nmap 192.168.154.128 192.168.3.7
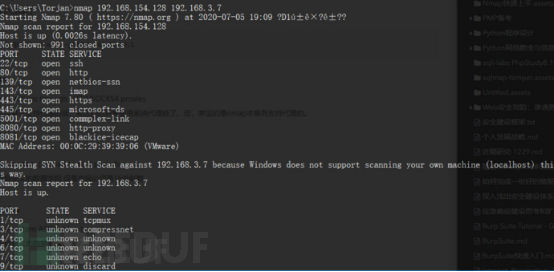
nmap 192.168.3.1-10 192.168.154.100-130
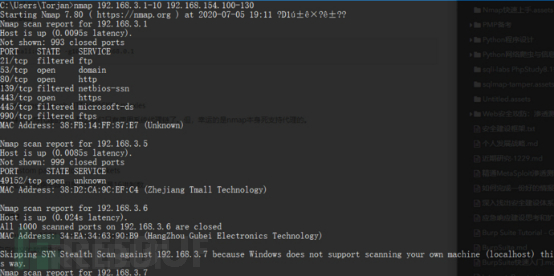
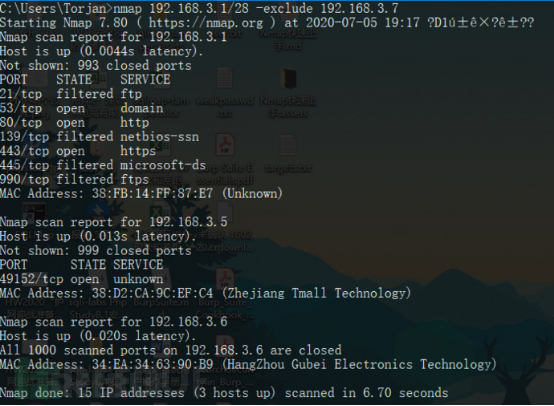
4.3 Ziele scannen, außer einem bestimmten Ziel
targets.txt:
192.168 .3.1
192.168.3.5
192.168.3.7
192.168.154.128
Verwendung:
nmap 192.168.3.1/28 -exclude 192.168.3.7
nmap 192.168.154.128 -excludefile targets.txt
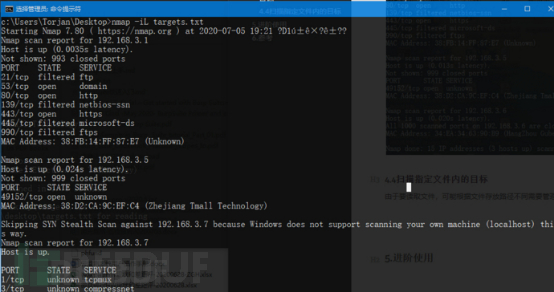
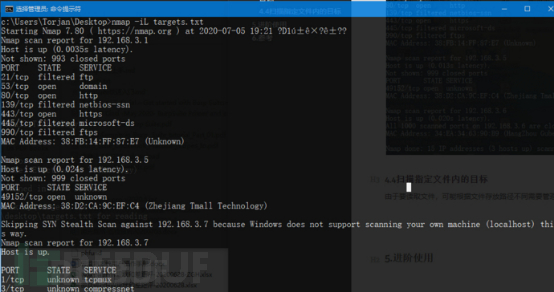
4.4 Scannen Sie das Ziel in der angegebenen Datei
Aufgrund des Lesens der Datei, die je nach Datei unterschiedlich sein kann Speicherpfad Es sind Administratorrechte erforderlich.
nmap -iL targets.txt
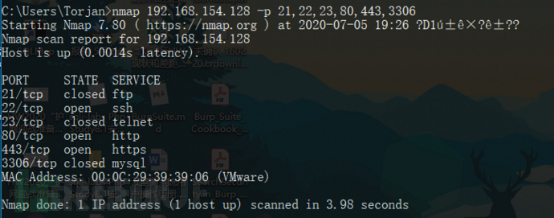
4.5 Angegebene Ports scannen.
nmap 192.168.154.128 -p 21,22,23,80,443,3306
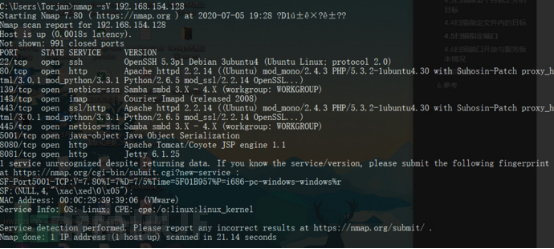
 4.8 Überlebenssituation des Wirts
4.8 Überlebenssituation des Wirts
nmap -sV 192.168.154.128
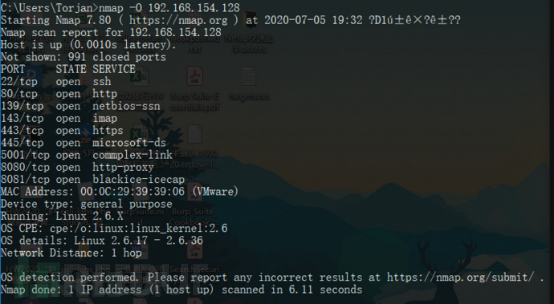
 4.9OS-Versionserkennung
4.9OS-Versionserkennung
nmap --traceroute 192.168.154.128
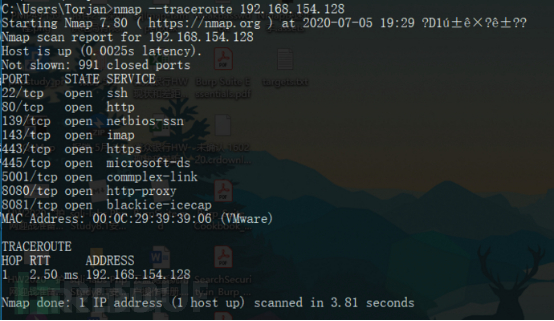 4.10 Firewall-Status
4.10 Firewall-Status
nmap -sP 192.168.3.0/24 192.168.154.0/24 -T5
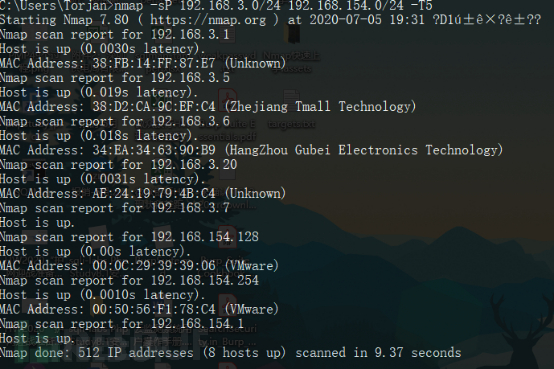 Statusidentifikation
Statusidentifikation
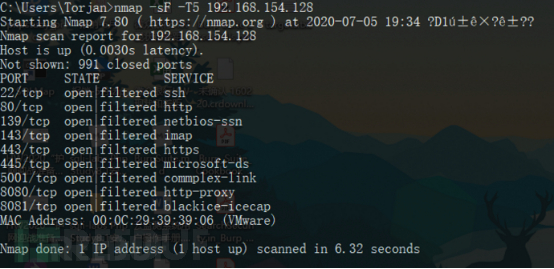 Bedeutung
Bedeutung
| Der Hafen ist offen. Der Status zeigt an, dass die Anwendung auf Verbindungen an diesem Port lauscht und von außen auf sie zugegriffen werden kann kann nicht zugegriffen werden. und es ist eine weitere Erkennung erforderlich |
Das obige ist der detaillierte Inhalt vonSo starten Sie schnell mit Nmap. Für weitere Informationen folgen Sie bitte anderen verwandten Artikeln auf der PHP chinesischen Website!

Heiße KI -Werkzeuge

Undresser.AI Undress
KI-gestützte App zum Erstellen realistischer Aktfotos

AI Clothes Remover
Online-KI-Tool zum Entfernen von Kleidung aus Fotos.

Undress AI Tool
Ausziehbilder kostenlos

Clothoff.io
KI-Kleiderentferner

AI Hentai Generator
Erstellen Sie kostenlos Ai Hentai.

Heißer Artikel

Heiße Werkzeuge

Notepad++7.3.1
Einfach zu bedienender und kostenloser Code-Editor

SublimeText3 chinesische Version
Chinesische Version, sehr einfach zu bedienen

Senden Sie Studio 13.0.1
Leistungsstarke integrierte PHP-Entwicklungsumgebung

Dreamweaver CS6
Visuelle Webentwicklungstools

SublimeText3 Mac-Version
Codebearbeitungssoftware auf Gottesniveau (SublimeText3)

Heiße Themen
 1377
1377
 52
52