关注于使用常用对象来加快Access 2007数据库
很多时候我们需要 加快 Access 数据库 。这篇文章讲述了 使用 数据可以怎样使得这个需求更加受到 关注 。这篇文章还探究了Access 2007 ACCDB一个叫做TempVars的特性。但是首先让我们讨论一些用户场景。 情景一:一个经验丰富的Excel技术人员建立了一个具有众
很多时候我们需要加快Access数据库。这篇文章讲述了使用数据可以怎样使得这个需求更加受到关注。这篇文章还探究了Access 2007 ACCDB一个叫做TempVars的特性。但是首先让我们讨论一些用户场景。
情景一:一个经验丰富的Excel技术人员建立了一个具有众多关联数据表的数据库。他坚信他需要升级到SQL server来加快这个数据库。这个数据库只有20MB大小,但是一些表单非常慢,在许多子表单里有许多标签控件和成百上千的离散字段。此外,使用这个数据库的用户需要每次都翻找记录来找到他们所要找的记录。只要添加一个找到记录框就可以使查找数据快得多。
情景二:一个复杂的数据库开发了六年了,而现在开发人员离开了这家公司。在最近的三年他们除了压缩和修复数据库之外没有做任何事,但是数据库的性能很糟糕。在这个数据库中,一些表格在按压关闭按钮之后需要两分钟才能关闭。而且,一些报表的运行需要一个小时。
情景三:一个大型数据库已经转变为使用SQL Server作为后台;它有250个表格和80个表。在高峰期它的性能是非常缓慢的。
好。那么你可以做些什么?首先我们可以假定慢数据库是一个复杂数据库。因此,如果你想加快每个对象,那么它需要很长时间。这意味着你只可以使用数据库的一部分,而确认数据库中有哪些对象是值得使用的最好方法就像下面讲述的。
访问主要用户来找出哪些表单和报表是缓慢的,并制作一个列表。从这个列表中找出最常用的五个缓慢对象并使用这些。这将告诉你可以做到多大的不同以及它将花费多长时间。
那么让我们看看我们可以怎样找出一个表单或一个报表被使用的频率,然后你可以关注于怎样使这些常用对象来变得快些。
提示:记住,这个数据库可能需要重新设计,所以不要为了加快真需要重新设计的数据库而过多的投入和改变很多有限的细节。
1 2 3 4 下一页

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
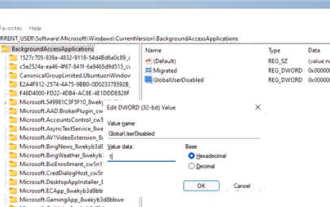
1. Open settings in Windows 11. You can use Win+I shortcut or any other method. 2. Go to the Apps section and click Apps & Features. 3. Find the application you want to prevent from running in the background. Click the three-dot button and select Advanced Options. 4. Find the [Background Application Permissions] section and select the desired value. By default, Windows 11 sets power optimization mode. It allows Windows to manage how applications work in the background. For example, once you enable battery saver mode to preserve battery, the system will automatically close all apps. 5. Select [Never] to prevent the application from running in the background. Please note that if you notice that the program is not sending you notifications, failing to update data, etc., you can
 How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
DeepSeek cannot convert files directly to PDF. Depending on the file type, you can use different methods: Common documents (Word, Excel, PowerPoint): Use Microsoft Office, LibreOffice and other software to export as PDF. Image: Save as PDF using image viewer or image processing software. Web pages: Use the browser's "Print into PDF" function or the dedicated web page to PDF tool. Uncommon formats: Find the right converter and convert it to PDF. It is crucial to choose the right tools and develop a plan based on the actual situation.
 BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
MetaMask (also called Little Fox Wallet in Chinese) is a free and well-received encryption wallet software. Currently, BTCC supports binding to the MetaMask wallet. After binding, you can use the MetaMask wallet to quickly log in, store value, buy coins, etc., and you can also get 20 USDT trial bonus for the first time binding. In the BTCCMetaMask wallet tutorial, we will introduce in detail how to register and use MetaMask, and how to bind and use the Little Fox wallet in BTCC. What is MetaMask wallet? With over 30 million users, MetaMask Little Fox Wallet is one of the most popular cryptocurrency wallets today. It is free to use and can be installed on the network as an extension
 Can't allow access to camera and microphone in iPhone
Apr 23, 2024 am 11:13 AM
Can't allow access to camera and microphone in iPhone
Apr 23, 2024 am 11:13 AM
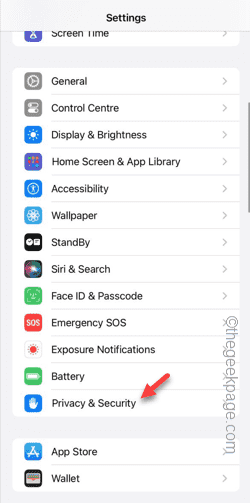
Are you getting "Unable to allow access to camera and microphone" when trying to use the app? Typically, you grant camera and microphone permissions to specific people on a need-to-provide basis. However, if you deny permission, the camera and microphone will not work and will display this error message instead. Solving this problem is very basic and you can do it in a minute or two. Fix 1 – Provide Camera, Microphone Permissions You can provide the necessary camera and microphone permissions directly in settings. Step 1 – Go to the Settings tab. Step 2 – Open the Privacy & Security panel. Step 3 – Turn on the “Camera” permission there. Step 4 – Inside, you will find a list of apps that have requested permission for your phone’s camera. Step 5 – Open the “Camera” of the specified app
 What does field mean in java
Apr 25, 2024 pm 10:18 PM
What does field mean in java
Apr 25, 2024 pm 10:18 PM
In Java, a "field" is a data member in a class or interface that is used to store data or state. The properties of field include: type (can be any Java data type), access rights, static (belongs to a class rather than an instance), final (immutable) and transient (not serialized). Field is used to store state information of a class or interface, such as storing object data and maintaining object state.
 How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
The Java reflection mechanism allows programs to dynamically modify the behavior of classes without modifying the source code. By operating the Class object, you can create instances through newInstance(), modify private field values, call private methods, etc. Reflection should be used with caution, however, as it can cause unexpected behavior and security issues, and has a performance overhead.
 How to convert MySQL query result array to object?
Apr 29, 2024 pm 01:09 PM
How to convert MySQL query result array to object?
Apr 29, 2024 pm 01:09 PM
Here's how to convert a MySQL query result array into an object: Create an empty object array. Loop through the resulting array and create a new object for each row. Use a foreach loop to assign the key-value pairs of each row to the corresponding properties of the new object. Adds a new object to the object array. Close the database connection.
 How to read dbf file in oracle
May 10, 2024 am 01:27 AM
How to read dbf file in oracle
May 10, 2024 am 01:27 AM
Oracle can read dbf files through the following steps: create an external table and reference the dbf file; query the external table to retrieve data; import the data into the Oracle table.






