Access入门教程 18.1 何时使用导入或联接
在Access中,可以很方便地从外部数据库中获取数据,这些数据库包括现在所有的各种主流数据库,像Dbase、 Sybase、Oracle、Foxpro等。这样你就不用去一个一个地重新输入原来的数据了。在Access中,可以用获取外部数据命令来获取外部数据库的数据,这个命令包
在Access中,可以很方便地从外部数据库中获取数据,这些数据库包括现在所有的各种主流数据库,像Dbase、 Sybase、Oracle、Foxpro等。这样你就不用去一个一个地重新输入原来的数据了。在Access中,可以用"获取外部数据"命令来获取外部数据库的数据,这个命令包括两种方式"导入"和"链接表".对于不同的外部数据库可以用不同的获取方式。而且在Access中,不光可以获取外部数据,还可以导出别的数据库,就是将用Access建立的数据库保存为别的数据库形式,像 FOXPRO,DBASE数据库等。
单击"文件"菜单中的"获取外部数据"项,弹出一个子菜单,上面有"导入"和"链接表"两个选项。我们单击其中的一个选项就可以实现导入或联接一个外部的数据库。虽然这两个命令的功用都是打开外部的一个数据库,并从中获取需要的数据,但在使用上,还是有差别的。
在我们使用"导入"这个方法来获取外部数据时需要注意几个条件。
一、需要我们打开的数据库文件相对来说比较小,而且不会被其他数据库应用程序的用 户频繁更改。
二、不需要与其他数据库应用程序的用户共享数据。
三、你正在替换以前的数据库应用程序,而且不再需要以前的数据格式。
四、在使用其他数据库中的数据时,需要最佳性能。
使用"链接表"方法来获取外部数据时也需要注意几个条件:
一、需要打开的文件比较大,甚至比本地Access数据库的最大容量(1GB)还要大。
二、这个文件经常被其他数据库应用程序的用户更改。
三、必须在网络上与其他数据库应用程序的用户共享这个文件。
四、需要把应用程序分布到几个单独的用户那里,而且,你可能要不断更新开发的应用程序接口,将"应用程序"与数据分开可以更容易地更新应用程序,而不会干扰用户积累的数据。
这就是为什么要在"获取外部数据"这个过程当中设置两种方法。如果要用的数据库并不大,但每天都可能要修改,而且由几个人来修改不同的部分,对于这种情况,最重要的是每天都有新的数据要处理,而单纯的将表导入进来,由于在Access中开发新的系统需要一定的时间,在这段时间内就有可能有新的数据输入进来。开始导入的数据就有很多可能已经更新了。所以这时使用"链接表"就不会出现这种问题,干扰到别的用户积累的数据。当然在Access中执行现在这台机器上的数据库文件是最快的,使用链接常常会因为很多原因使你的工作变得很慢,这点是你必须考虑的。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1371
1371
 52
52
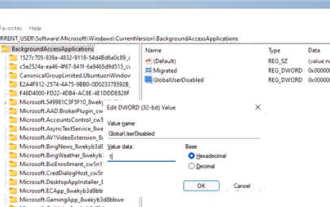 How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
1. Open settings in Windows 11. You can use Win+I shortcut or any other method. 2. Go to the Apps section and click Apps & Features. 3. Find the application you want to prevent from running in the background. Click the three-dot button and select Advanced Options. 4. Find the [Background Application Permissions] section and select the desired value. By default, Windows 11 sets power optimization mode. It allows Windows to manage how applications work in the background. For example, once you enable battery saver mode to preserve battery, the system will automatically close all apps. 5. Select [Never] to prevent the application from running in the background. Please note that if you notice that the program is not sending you notifications, failing to update data, etc., you can
 BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
MetaMask (also called Little Fox Wallet in Chinese) is a free and well-received encryption wallet software. Currently, BTCC supports binding to the MetaMask wallet. After binding, you can use the MetaMask wallet to quickly log in, store value, buy coins, etc., and you can also get 20 USDT trial bonus for the first time binding. In the BTCCMetaMask wallet tutorial, we will introduce in detail how to register and use MetaMask, and how to bind and use the Little Fox wallet in BTCC. What is MetaMask wallet? With over 30 million users, MetaMask Little Fox Wallet is one of the most popular cryptocurrency wallets today. It is free to use and can be installed on the network as an extension
 How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
DeepSeek cannot convert files directly to PDF. Depending on the file type, you can use different methods: Common documents (Word, Excel, PowerPoint): Use Microsoft Office, LibreOffice and other software to export as PDF. Image: Save as PDF using image viewer or image processing software. Web pages: Use the browser's "Print into PDF" function or the dedicated web page to PDF tool. Uncommon formats: Find the right converter and convert it to PDF. It is crucial to choose the right tools and develop a plan based on the actual situation.
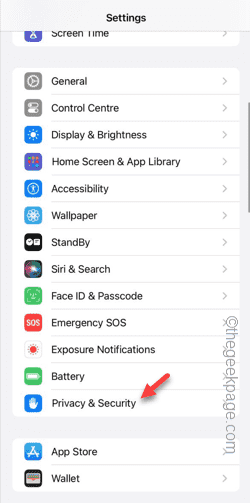 Can't allow access to camera and microphone in iPhone
Apr 23, 2024 am 11:13 AM
Can't allow access to camera and microphone in iPhone
Apr 23, 2024 am 11:13 AM
Are you getting "Unable to allow access to camera and microphone" when trying to use the app? Typically, you grant camera and microphone permissions to specific people on a need-to-provide basis. However, if you deny permission, the camera and microphone will not work and will display this error message instead. Solving this problem is very basic and you can do it in a minute or two. Fix 1 – Provide Camera, Microphone Permissions You can provide the necessary camera and microphone permissions directly in settings. Step 1 – Go to the Settings tab. Step 2 – Open the Privacy & Security panel. Step 3 – Turn on the “Camera” permission there. Step 4 – Inside, you will find a list of apps that have requested permission for your phone’s camera. Step 5 – Open the “Camera” of the specified app
 What does field mean in java
Apr 25, 2024 pm 10:18 PM
What does field mean in java
Apr 25, 2024 pm 10:18 PM
In Java, a "field" is a data member in a class or interface that is used to store data or state. The properties of field include: type (can be any Java data type), access rights, static (belongs to a class rather than an instance), final (immutable) and transient (not serialized). Field is used to store state information of a class or interface, such as storing object data and maintaining object state.
 How to read dbf file in oracle
May 10, 2024 am 01:27 AM
How to read dbf file in oracle
May 10, 2024 am 01:27 AM
Oracle can read dbf files through the following steps: create an external table and reference the dbf file; query the external table to retrieve data; import the data into the Oracle table.
 How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
The Java reflection mechanism allows programs to dynamically modify the behavior of classes without modifying the source code. By operating the Class object, you can create instances through newInstance(), modify private field values, call private methods, etc. Reflection should be used with caution, however, as it can cause unexpected behavior and security issues, and has a performance overhead.
 Common exception types and their repair measures in Java function development
May 03, 2024 pm 02:09 PM
Common exception types and their repair measures in Java function development
May 03, 2024 pm 02:09 PM
Common exception types and their repair measures in Java function development During the development of Java functions, various exceptions may be encountered, which affect the correct execution of the function. The following are common exception types and their repair measures: 1. NullPointerException Description: Thrown when accessing an object that has not been initialized. Fix: Make sure you check the object for non-null before using it. Sample code: try{Stringname=null;System.out.println(name.length());}catch(NullPointerExceptione){




