ZOJ Access System
Time Limit: 2 Seconds Memory Limit: 65536 KB For security issues, Marjar University has an access control system for each dormitory building.The system requires the students to use their personal identification cards to open the gate if th
For security issues, Marjar University has an access control system for each dormitory building.The system requires the students to use their personal identification cards to open the gate if they want to enter the building.
The gate will then remain unlocked for L seconds. For example L = 15, if a student came to the dormitory at 17:00:00 (in the format of HH:MM:SS) and used his card to open the gate. Any other students who come to the dormitory between [17:00:00, 17:00:15) can enter the building without authentication. If there is another student comes to the dorm at 17:00:15 or later, he must take out his card to unlock the gate again.
There are N students need to enter the dormitory. You are given the time they come to the gate. These lazy students will not use their cards unless necessary. Please find out the students who need to do so.
Input
There are multiple test cases. The first line of input contains an integer T indicating the number of test cases. For each test case:
The first line contains two integers N (1 N L (1 L N lines, each line is a unique time between [00:00:00, 24:00:00) on the same day.
Output
For each test case, output two lines. The first line is the number of students who need to use the card to open the gate. The second line the the index (1-based) of these students in ascending order, separated by a space.
Sample Input
3 2 1 12:30:00 12:30:01 5 15 17:00:00 17:00:15 17:00:06 17:01:00 17:00:14 <span>3 5 12:00:09 12:00:05 12:00:00</span>
Sample Output
2 1 2 3 1 2 4 <span>2 2 3 </span>
<pre class="brush:php;toolbar:false">#include<stdio.h>
#include<iostream>
#include<algorithm>
using namespace std;
typedef struct nnn
{
int s,i;
}Time;
int cmp(Time a,Time b)
{
return a.s<b.s int main time student t scanf while sum="0;" for i="0;i<n;i++)" sort if loc node.s="student[0].s+L;" printf><br><br></b.s></algorithm></iostream></stdio.h>
Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
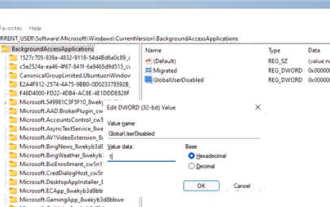 How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
1. Open settings in Windows 11. You can use Win+I shortcut or any other method. 2. Go to the Apps section and click Apps & Features. 3. Find the application you want to prevent from running in the background. Click the three-dot button and select Advanced Options. 4. Find the [Background Application Permissions] section and select the desired value. By default, Windows 11 sets power optimization mode. It allows Windows to manage how applications work in the background. For example, once you enable battery saver mode to preserve battery, the system will automatically close all apps. 5. Select [Never] to prevent the application from running in the background. Please note that if you notice that the program is not sending you notifications, failing to update data, etc., you can
 How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
DeepSeek cannot convert files directly to PDF. Depending on the file type, you can use different methods: Common documents (Word, Excel, PowerPoint): Use Microsoft Office, LibreOffice and other software to export as PDF. Image: Save as PDF using image viewer or image processing software. Web pages: Use the browser's "Print into PDF" function or the dedicated web page to PDF tool. Uncommon formats: Find the right converter and convert it to PDF. It is crucial to choose the right tools and develop a plan based on the actual situation.
 What does dao mean in java
Apr 21, 2024 am 02:08 AM
What does dao mean in java
Apr 21, 2024 am 02:08 AM
DAO (Data Access Object) in Java is used to separate application code and persistence layer, its advantages include: Separation: Independent from application logic, making it easier to modify it. Encapsulation: Hide database access details and simplify interaction with the database. Scalability: Easily expandable to support new databases or persistence technologies. With DAOs, applications can call methods to perform database operations such as create, read, update, and delete entities without directly dealing with database details.
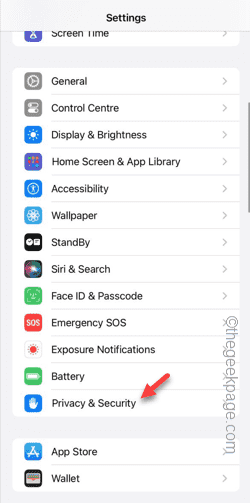 Can't allow access to camera and microphone in iPhone
Apr 23, 2024 am 11:13 AM
Can't allow access to camera and microphone in iPhone
Apr 23, 2024 am 11:13 AM
Are you getting "Unable to allow access to camera and microphone" when trying to use the app? Typically, you grant camera and microphone permissions to specific people on a need-to-provide basis. However, if you deny permission, the camera and microphone will not work and will display this error message instead. Solving this problem is very basic and you can do it in a minute or two. Fix 1 – Provide Camera, Microphone Permissions You can provide the necessary camera and microphone permissions directly in settings. Step 1 – Go to the Settings tab. Step 2 – Open the Privacy & Security panel. Step 3 – Turn on the “Camera” permission there. Step 4 – Inside, you will find a list of apps that have requested permission for your phone’s camera. Step 5 – Open the “Camera” of the specified app
 What does field mean in java
Apr 25, 2024 pm 10:18 PM
What does field mean in java
Apr 25, 2024 pm 10:18 PM
In Java, a "field" is a data member in a class or interface that is used to store data or state. The properties of field include: type (can be any Java data type), access rights, static (belongs to a class rather than an instance), final (immutable) and transient (not serialized). Field is used to store state information of a class or interface, such as storing object data and maintaining object state.
 How to read the Oracle stored procedure execution plan
Apr 18, 2024 pm 10:18 PM
How to read the Oracle stored procedure execution plan
Apr 18, 2024 pm 10:18 PM
Oracle stored procedure execution plans provide execution information, including access paths, estimated number of rows, join order, and costs. To view the execution plan, execute the EXPLAIN PLAN command and look for the "Execution Plan" section. The execution plan contains a header and body, showing in detail the ID, operation type, number of rows, cost, access path, filter conditions, involved tables and indexes, and the connection sequence if there is a connection.
 How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
The Java reflection mechanism allows programs to dynamically modify the behavior of classes without modifying the source code. By operating the Class object, you can create instances through newInstance(), modify private field values, call private methods, etc. Reflection should be used with caution, however, as it can cause unexpected behavior and security issues, and has a performance overhead.
 How to cross-domain iframe in vue
May 02, 2024 pm 10:48 PM
How to cross-domain iframe in vue
May 02, 2024 pm 10:48 PM
Ways to solve iframe cross-domain issues in Vue: CORS: Enable CORS support in the backend server and use XMLHttpRequest or fetch API to send CORS requests in Vue. JSONP: Dynamically load JSONP scripts in Vue using the JSONP endpoint in the backend server. Proxy server: Set up a proxy server to forward requests, use a third-party library (such as axios) in Vue to send requests and set the proxy server URL.






