mount.nfs:access denied by server while mounting问题解决
出现了如下的提示:mount.nfs: access denied by server while mounting localhost:/root/nfs_root 花了我3天的时间,检测。 发现在公司的电脑配置没有问题。就家里的台式机会出问题。 网上search找不到任何原因。 郁闷了。 后来,我尝试了重新配置/home/med
出现了如下的提示:mount.nfs: access denied by server while mounting localhost:/root/nfs_root
花了我3天的时间,检测。 发现在公司的电脑配置没有问题。就家里的台式机会出问题。
网上search找不到任何原因。 郁闷了。
后来,我尝试了重新配置/home/medea作为挂载点,发现居然通过了。
我就到根目录下, ls -al。总算发现问题了。原来我的/root的权限是 drwx------
我就想到了, 本地mount上后,会是另一种用户登录。 原来是root访问权限出问题了。
于是:
#chmod 755 /root
在尝试
#mount -t nfs localhost:/root/nfs_root /root/book
OK! 成功。 ^_^

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
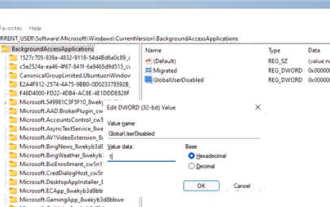 How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
How to disable background applications in Windows 11_Windows 11 tutorial to disable background applications
May 07, 2024 pm 04:20 PM
1. Open settings in Windows 11. You can use Win+I shortcut or any other method. 2. Go to the Apps section and click Apps & Features. 3. Find the application you want to prevent from running in the background. Click the three-dot button and select Advanced Options. 4. Find the [Background Application Permissions] section and select the desired value. By default, Windows 11 sets power optimization mode. It allows Windows to manage how applications work in the background. For example, once you enable battery saver mode to preserve battery, the system will automatically close all apps. 5. Select [Never] to prevent the application from running in the background. Please note that if you notice that the program is not sending you notifications, failing to update data, etc., you can
 How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
How to convert deepseek pdf
Feb 19, 2025 pm 05:24 PM
DeepSeek cannot convert files directly to PDF. Depending on the file type, you can use different methods: Common documents (Word, Excel, PowerPoint): Use Microsoft Office, LibreOffice and other software to export as PDF. Image: Save as PDF using image viewer or image processing software. Web pages: Use the browser's "Print into PDF" function or the dedicated web page to PDF tool. Uncommon formats: Find the right converter and convert it to PDF. It is crucial to choose the right tools and develop a plan based on the actual situation.
 How to read dbf file in oracle
May 10, 2024 am 01:27 AM
How to read dbf file in oracle
May 10, 2024 am 01:27 AM
Oracle can read dbf files through the following steps: create an external table and reference the dbf file; query the external table to retrieve data; import the data into the Oracle table.
 How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
How does the Java reflection mechanism modify the behavior of a class?
May 03, 2024 pm 06:15 PM
The Java reflection mechanism allows programs to dynamically modify the behavior of classes without modifying the source code. By operating the Class object, you can create instances through newInstance(), modify private field values, call private methods, etc. Reflection should be used with caution, however, as it can cause unexpected behavior and security issues, and has a performance overhead.
 Interpretation of Botanix: decentralized BTC L2 for network asset management (with interactive tutorial)
May 08, 2024 pm 06:40 PM
Interpretation of Botanix: decentralized BTC L2 for network asset management (with interactive tutorial)
May 08, 2024 pm 06:40 PM
Yesterday, BotanixLabs announced that it has completed a total of US$11.5 million in financing, with participation from Polychain Capital, Placeholder Capital and others. Financing will be used to build the decentralized EVM equivalent of BTCL2Botanix. Spiderchain combines the ease of use of EVM with the security of Bitcoin. Since the testnet went live in November 2023, there have been more than 200,000 active addresses. Odaily will analyze Botanix’s characteristic mechanism and testnet interaction process in this article. Botanix According to the official definition, Botanix is a decentralized Turing-complete L2EVM built on Bitcoin and consists of two core components: Ethereum Virtual Machine
 How does the Java reflection mechanism implement dynamic loading of classes?
May 04, 2024 pm 03:42 PM
How does the Java reflection mechanism implement dynamic loading of classes?
May 04, 2024 pm 03:42 PM
The Java reflection mechanism allows classes to be dynamically loaded and instantiated at runtime, and class metadata can be manipulated through classes in the java.lang.reflect package, including Class, Method, and Field. Through practical cases of loading the Example class, instantiating objects, obtaining and calling methods, you can demonstrate its application in dynamically loaded classes, thereby solving programming problems and improving flexibility.
 How to solve access violation error
May 07, 2024 pm 05:18 PM
How to solve access violation error
May 07, 2024 pm 05:18 PM
Access Violation error is a run-time error that occurs when a program accesses a memory location beyond its memory allocation, causing the program to crash or terminate abnormally. Solutions include: checking array boundaries; using pointers correctly; using appropriate memory allocation functions; freeing freed memory; checking for memory overflows; updating drivers and systems; checking third-party libraries; using a debugger to trace execution; contacting the software vendor for support.
 Record once and use strace to diagnose the problem of PHP occupying too much system resources.
May 03, 2024 pm 04:31 PM
Record once and use strace to diagnose the problem of PHP occupying too much system resources.
May 03, 2024 pm 04:31 PM
Local environment: redhat6.7 system. nginx1.12.1, php7.1.0, the code uses the yii2 framework problem: the local web site needs to use the elasticsearch service. When PHP uses elasticsearch built on a local server, the local load is normal. When I use AWS's elasticsearch service, the load on the local server is often too high. Check the nginx and php logs and find no exceptions. The number of concurrent connections in the system is also not high. At this time, I thought of a strace diagnostic tool that our boss told me. Debugging process: Find a php sub-process idstrace-




