SQLite入门之三常用命令
sqlite .mode csv sqlite SELECT * FROM Cars; 1,Audi,52642 2,Mercedes,57127 3,Skoda,9000 4,Volvo,29000 5,Bentley,350000 6,Citroen,21000 7,Hummer,41400 8,Volkswagen,21600 sqlite .mode tabs sqlite SELECT * FROM Cars; 1 Audi 52642 2 Mercedes 57
sqlite> .mode csv
sqlite> SELECT * FROM Cars;
1,Audi,52642
2,Mercedes,57127
3,Skoda,9000
4,Volvo,29000
5,Bentley,350000
6,Citroen,21000
7,Hummer,41400
8,Volkswagen,21600
sqlite> .mode tabs
sqlite> SELECT * FROM Cars;
1 Audi 52642
2 Mercedes 57127
3 Skoda 9000
4 Volvo 29000
5 Bentley 350000
6 Citroen 21000
7 Hummer 41400
8 Volkswagen 21600
,
Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
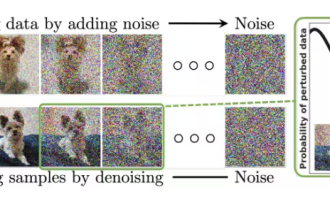 A Diffusion Model Tutorial Worth Your Time, from Purdue University
Apr 07, 2024 am 09:01 AM
A Diffusion Model Tutorial Worth Your Time, from Purdue University
Apr 07, 2024 am 09:01 AM
Diffusion can not only imitate better, but also "create". The diffusion model (DiffusionModel) is an image generation model. Compared with the well-known algorithms such as GAN and VAE in the field of AI, the diffusion model takes a different approach. Its main idea is a process of first adding noise to the image and then gradually denoising it. How to denoise and restore the original image is the core part of the algorithm. The final algorithm is able to generate an image from a random noisy image. In recent years, the phenomenal growth of generative AI has enabled many exciting applications in text-to-image generation, video generation, and more. The basic principle behind these generative tools is the concept of diffusion, a special sampling mechanism that overcomes the limitations of previous methods.
 How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
How to run SUDO commands in Windows 11/10
Mar 09, 2024 am 09:50 AM
The sudo command allows users to run commands in elevated privilege mode without switching to superuser mode. This article will introduce how to simulate functions similar to sudo commands in Windows systems. What is the Shudao Command? Sudo (short for "superuser do") is a command-line tool that allows users of Unix-based operating systems such as Linux and MacOS to execute commands with elevated privileges typically held by administrators. Running SUDO commands in Windows 11/10 However, with the launch of the latest Windows 11 Insider preview version, Windows users can now experience this feature. This new feature enables users to
 Generate PPT with one click! Kimi: Let the 'PPT migrant workers' become popular first
Aug 01, 2024 pm 03:28 PM
Generate PPT with one click! Kimi: Let the 'PPT migrant workers' become popular first
Aug 01, 2024 pm 03:28 PM
Kimi: In just one sentence, in just ten seconds, a PPT will be ready. PPT is so annoying! To hold a meeting, you need to have a PPT; to write a weekly report, you need to have a PPT; to make an investment, you need to show a PPT; even when you accuse someone of cheating, you have to send a PPT. College is more like studying a PPT major. You watch PPT in class and do PPT after class. Perhaps, when Dennis Austin invented PPT 37 years ago, he did not expect that one day PPT would become so widespread. Talking about our hard experience of making PPT brings tears to our eyes. "It took three months to make a PPT of more than 20 pages, and I revised it dozens of times. I felt like vomiting when I saw the PPT." "At my peak, I did five PPTs a day, and even my breathing was PPT." If you have an impromptu meeting, you should do it
 How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
How to check the MAC address of the network card in Win11? How to use the command to obtain the MAC address of the network card in Win11
Feb 29, 2024 pm 04:34 PM
This article will introduce readers to how to use the command prompt (CommandPrompt) to find the physical address (MAC address) of the network adapter in Win11 system. A MAC address is a unique identifier for a network interface card (NIC), which plays an important role in network communications. Through the command prompt, users can easily obtain the MAC address information of all network adapters on the current computer, which is very helpful for network troubleshooting, configuring network settings and other tasks. Method 1: Use "Command Prompt" 1. Press the [Win+X] key combination, or [right-click] click the [Windows logo] on the taskbar, and in the menu item that opens, select [Run]; 2. Run the window , enter the [cmd] command, and then
 Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
Where is hyperv enhanced session mode? Tips for enabling or disabling Hyper-V enhanced session mode using commands in Win11
Feb 29, 2024 pm 05:52 PM
In Win11 system, you can enable or disable Hyper-V enhanced session mode through commands. This article will introduce how to use commands to operate and help users better manage and control Hyper-V functions in the system. Hyper-V is a virtualization technology provided by Microsoft. It is built into Windows Server and Windows 10 and 11 (except Home Edition), allowing users to run virtual operating systems in Windows systems. Although virtual machines are isolated from the host operating system, they can still use the host's resources, such as sound cards and storage devices, through settings. One of the key settings is to enable Enhanced Session Mode. Enhanced session mode is Hyper
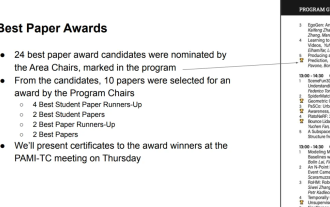 All CVPR 2024 awards announced! Nearly 10,000 people attended the conference offline, and a Chinese researcher from Google won the best paper award
Jun 20, 2024 pm 05:43 PM
All CVPR 2024 awards announced! Nearly 10,000 people attended the conference offline, and a Chinese researcher from Google won the best paper award
Jun 20, 2024 pm 05:43 PM
In the early morning of June 20th, Beijing time, CVPR2024, the top international computer vision conference held in Seattle, officially announced the best paper and other awards. This year, a total of 10 papers won awards, including 2 best papers and 2 best student papers. In addition, there were 2 best paper nominations and 4 best student paper nominations. The top conference in the field of computer vision (CV) is CVPR, which attracts a large number of research institutions and universities every year. According to statistics, a total of 11,532 papers were submitted this year, and 2,719 were accepted, with an acceptance rate of 23.6%. According to Georgia Institute of Technology’s statistical analysis of CVPR2024 data, from the perspective of research topics, the largest number of papers is image and video synthesis and generation (Imageandvideosyn
 Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
Super practical! Sar commands that will make you a Linux master
Mar 01, 2024 am 08:01 AM
1. Overview The sar command displays system usage reports through data collected from system activities. These reports are made up of different sections, each containing the type of data and when the data was collected. The default mode of the sar command displays the CPU usage at different time increments for various resources accessing the CPU (such as users, systems, I/O schedulers, etc.). Additionally, it displays the percentage of idle CPU for a given time period. The average value for each data point is listed at the bottom of the report. sar reports collected data every 10 minutes by default, but you can use various options to filter and adjust these reports. Similar to the uptime command, the sar command can also help you monitor the CPU load. Through sar, you can understand the occurrence of excessive load
 A must-read for technical beginners: Analysis of the difficulty levels of C language and Python
Mar 22, 2024 am 10:21 AM
A must-read for technical beginners: Analysis of the difficulty levels of C language and Python
Mar 22, 2024 am 10:21 AM
Title: A must-read for technical beginners: Difficulty analysis of C language and Python, requiring specific code examples In today's digital age, programming technology has become an increasingly important ability. Whether you want to work in fields such as software development, data analysis, artificial intelligence, or just learn programming out of interest, choosing a suitable programming language is the first step. Among many programming languages, C language and Python are two widely used programming languages, each with its own characteristics. This article will analyze the difficulty levels of C language and Python






