SQL Server数据访问程序优化指南
经过紧张的调查,你发现问题出在数据库上,当应用程序尝试访问/更新数据时,数据库执行得相当慢,再次深入调查数据库后,你发现数据库表增长得很大,有些表甚至有上千万行数据,测试团队开始在生产数据库上测试,发现订单提交过程需要花5分钟时间,但在网站
经过紧张的调查,你发现问题出在上,当应用程序尝试访问/更新数据时,执行得相当慢,再次深入调查数据库后,你发现数据库表增长得很大,有些表甚至有上千万行数据,测试团队开始在生产数据库上测试,发现订单提交过程需要花5分钟时间,但在网站上线前的测试中,提交一次订单只需要2/3秒。
类似这种故事在世界各个角落每天都会上演,几乎每个开发人员在其开发生涯中都会遇到这种事情,我也曾多次遇到这种情况,因此我希望将我解决这种问题的经验和大家分享。
如果你正身处这种项目,逃避不是办法,只有勇敢地去面对现实。首先,我认为你的应用程序中一定没有写数据访问程序,我将在这个系列的文章中介绍如何编写最佳的数据访问程序,以及如何优化现有的数据访问程序。
范围
在正式开始之前,有必要澄清一下本系列文章的写作边界,我想谈的是“事务性(OLTP)SQL Server数据库中的数据访问性能优化”,但文中介绍的这些技巧也可以用于其它数据库平台。
同时,我介绍的这些技巧主要是面向程序开发人员的,虽然DBA也是优化数据库的一支主要力量,但DBA使用的优化方法不在我的讨论范围之内。
当一个基于数据库的应用程序运行起来很慢时,90%的可能都是由于数据访问程序的问题,要么是没有优化,要么是没有按最佳方法编写代码,因此你需要审查和优化你的数据访问/处理程序。
我将会谈到10个步骤来优化数据访问程序,先从最基本的索引说起吧!
第一步:应用正确的索引
我之所以先从索引谈起是因为采用正确的索引会使生产系统的性能得到质的提升,另一个原因是创建或修改索引是在数据库上进行的,不会涉及到修改程序,并可以立即见到成效。
我们还是温习一下索引的基础知识吧,我相信你已经知道什么是索引了,但我见到很多人都还不是很明白,我先给大家将一个故事吧。
很久以前,在一个古城的的大图书馆中珍藏有成千上万本书籍,但书架上的书没有按任何顺序摆放,因此每当有人询问某本书时,图书管理员只有挨个寻找,每一次都要花费大量的时间。
[这就好比数据表没有主键一样,搜索表中的数据时,数据库引擎必须进行全表扫描,效率极其低下。]
更糟的是图书馆的图书越来越多,图书管理员的工作变得异常痛苦,有一天来了一个聪明的小伙子,他看到图书管理员的痛苦工作后,想出了一个办法,他建议将每本书都编上号,然后按编号放到书架上,如果有人指定了图书编号,那么图书管理员很快就可以找到它的位置了。
[给图书编号就象给表创建主键一样,创建主键时,会创建聚集索引树,表中的所有行会在文件系统上根据主键值进行物理排序,当查询表中任一行时,数据库首先使用聚集索引树找到对应的数据页(就象首先找到书架一样),然后在数据页中根据主键键值找到目标行(就象找到书架上的书一样)。]
于是图书管理员开始给图书编号,然后根据编号将书放到书架上,为此他花了整整一天时间,但最后经过测试,他发现找书的效率大大提高了。
[在一个表上只能创建一个聚集索引,就象书只能按一种规则摆放一样。]
但问题并未完全解决,因为很多人记不住书的编号,只记得书的名字,图书管理员无赖又只有扫描所有的图书编号挨个寻找,但这次他只花了20分钟,以前未给图书编号时要花2-3小时,但与根据图书编号查找图书相比,时间还是太长了,因此他向那个聪明的小伙子求助。
[这就好像你给Product表增加了主键ProductID,但除此之外没有建立其它索引,当使用Product Name进行检索时,数据库引擎又只要进行全表扫描,逐个寻找了。]
聪明的小伙告诉图书管理员,之前已经创建好了图书编号,现在只需要再创建一个索引或目录,将图书名称和对应的编号一起存储起来,但这一次是按图书名称进行排序,如果有人想找“Database Management System”一书,你只需要跳到“D”开头的目录,然后按照编号就可以找到图书了。
于是图书管理员兴奋地花了几个小时创建了一个“图书名称”目录,经过测试,现在找一本书的时间缩短到1分钟了(其中30秒用于从“图书名称”目录中查找编号,另外根据编号查找图书用了30秒)。
图书管理员开始了新的思考,读者可能还会根据图书的其它属性来找书,如作者,于是他用同样的办法为作者也创建了目录,现在可以根据图书编号,书名和作者在1分钟内查找任何图书了,图书管理员的工作变得轻松了,故事也到此结束。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 What does dao mean in java
Apr 21, 2024 am 02:08 AM
What does dao mean in java
Apr 21, 2024 am 02:08 AM
DAO (Data Access Object) in Java is used to separate application code and persistence layer, its advantages include: Separation: Independent from application logic, making it easier to modify it. Encapsulation: Hide database access details and simplify interaction with the database. Scalability: Easily expandable to support new databases or persistence technologies. With DAOs, applications can call methods to perform database operations such as create, read, update, and delete entities without directly dealing with database details.
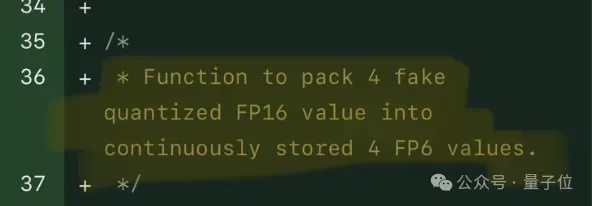 Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
Single card running Llama 70B is faster than dual card, Microsoft forced FP6 into A100 | Open source
Apr 29, 2024 pm 04:55 PM
FP8 and lower floating point quantification precision are no longer the "patent" of H100! Lao Huang wanted everyone to use INT8/INT4, and the Microsoft DeepSpeed team started running FP6 on A100 without official support from NVIDIA. Test results show that the new method TC-FPx's FP6 quantization on A100 is close to or occasionally faster than INT4, and has higher accuracy than the latter. On top of this, there is also end-to-end large model support, which has been open sourced and integrated into deep learning inference frameworks such as DeepSpeed. This result also has an immediate effect on accelerating large models - under this framework, using a single card to run Llama, the throughput is 2.65 times higher than that of dual cards. one
 How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
How to remove the write protection of a USB flash drive? Several simple and effective methods can help you do it
May 02, 2024 am 09:04 AM
U disk is one of the commonly used storage devices in our daily work and life, but sometimes we encounter situations where the U disk is write-protected and cannot write data. This article will introduce several simple and effective methods to help you quickly remove the write protection of the USB flash drive and restore the normal use of the USB flash drive. Tool materials: System version: Windows1020H2, macOS BigSur11.2.3 Brand model: SanDisk UltraFlair USB3.0 flash drive, Kingston DataTraveler100G3USB3.0 flash drive Software version: DiskGenius5.4.2.1239, ChipGenius4.19.1225 1. Check the physical write protection switch of the USB flash drive on some USB flash drives Designed with
 What does schema mean in mysql
May 01, 2024 pm 08:33 PM
What does schema mean in mysql
May 01, 2024 pm 08:33 PM
Schema in MySQL is a logical structure used to organize and manage database objects (such as tables, views) to ensure data consistency, data access control and simplify database design. The functions of Schema include: 1. Data organization; 2. Data consistency; 3. Data access control; 4. Database design.
 What is the API interface for?
Apr 23, 2024 pm 01:51 PM
What is the API interface for?
Apr 23, 2024 pm 01:51 PM
An API interface is a specification for interaction between software components and is used to implement communication and data exchange between different applications or systems. The API interface acts as a "translator", converting the developer's instructions into computer language so that the applications can work together. Its advantages include convenient data sharing, simplified development, improved performance, enhanced security, improved productivity and interoperability.
 What does mysql database do?
Apr 22, 2024 pm 06:12 PM
What does mysql database do?
Apr 22, 2024 pm 06:12 PM
MySQL is a relational database management system that provides the following main functions: Data storage and management: Create and organize data, supporting various data types, primary keys, foreign keys, and indexes. Data query and retrieval: Use SQL language to query, filter and retrieve data, and optimize execution plans to improve efficiency. Data updates and modifications: Add, modify or delete data through INSERT, UPDATE, DELETE commands, supporting transactions to ensure consistency and rollback mechanisms to undo changes. Database management: Create and modify databases and tables, back up and restore data, and provide user management and permission control.
 Redis cache implementation principle
Apr 19, 2024 pm 10:36 PM
Redis cache implementation principle
Apr 19, 2024 pm 10:36 PM
The Redis caching mechanism is implemented through key-value storage, memory storage, expiration policies, data structures, replication, and persistence. It follows the steps of obtaining data, cache hit, cache miss, writing to cache, and updating cache to provide fast data access and high-performance caching services.
 Data Security in Artificial Intelligence: How to Unleash the Power of Artificial Intelligence
Apr 24, 2024 pm 06:20 PM
Data Security in Artificial Intelligence: How to Unleash the Power of Artificial Intelligence
Apr 24, 2024 pm 06:20 PM
In the digital age, data is often viewed as the battery that powers the innovation machine and drives business decisions. With the rise of modern solutions like artificial intelligence (AI) and machine learning (ML), organizations have access to vast amounts of data, enough to gain valuable insights and make informed decisions. However, this comes at the cost of subsequent data loss and confidentiality challenges. As organizations continue to grasp the potential of artificial intelligence, they must strike a balance between achieving business advancements while avoiding potential risks. This article focuses on the importance of data security in artificial intelligence and what security measures organizations can take to avoid risks while taking advantage of the viable solutions provided by artificial intelligence. In artificial intelligence, data security is crucial. Organizations need to ensure data used is legal






