浅析PHP中cookie与session技术
浅析PHP中cookie与session技术
1.cookie是什么?
cookie指某些网站为了辨别用户身份、进行session跟踪而储存在用户本地终端上的数据(通常经过加密)。
通俗来理解就是,你去一个专卖店或者超市买东西,然后店里给你办一张会员卡,以后你的身份和购买信息都存在这个卡里,而这个卡放你身上。之后每次去买东西的时候只需要刷卡就可以了,不用再登记或者记录其他的信息。
然后将这段话映射了web上,超市结账台就是服务器端,而你自己就是客户端,你身上所带的卡也就是存在客户端中的cookie文件,里面记录了你的帐号密码等信息。
不过要注意的一点,cookie在第二次使用的时候才能够生效,也就是说你在超市第一次买东西,人家会给你办卡,你以后来买就可以刷卡了,但是第一次买之前,超市并没有你的任何信息,所以你第一次根本就没有卡。网站也一样,第一次登录某网站,当然要输入帐号密码等信息,然后才能生成cookie存在本地,以便下一次使用。
同时,cookie也有自己的有效期,过了期以后就失效了,本地的cookie文件会被自动删除。需要再次登录,输入帐号密码,然后生成新的cookie。这样做的主要目的还是为了安全考虑。
2.cookie机制图解。
3.cookie使用方法。
(1)设置cookie
bool setcookie ( string $name,$value,$expire,$path,$domain,$secure,$httponly
setcookie("username","user",0,"/");
setcookie("username","user",time()+60*60,"/");
每个参数的用法就不作说明了。这里重点解析一下上面两中设置cookie方式中的时间和路径。
第一个当中的时间放了个0进去,难道代表生存时间为0.明显不可能,它有着特殊的意义,表示cookie的有效期随着浏览器的关闭而结束。他们的路径中都放了个"/"。这个就代表在这个域名下的所有contentpath都可以访问cookie,也就是说这个网站下的所有页面都可以追踪这个cookie。
(2)删除cookie
setcookie("username","",time()-3600,"/");(3)查看cookie
print_r($_COOKIE);
----------------------------------------------------------------------------------
-----------------------------我是分割线-------------------------------------------
----------------------------------------------------------------------------------
1.session是什么?
Session是指一个终端用户与交互系统进行通信的时间间隔,通常指从注册进入系统到注销退出系统之间所经过的时间。
session的工作原理(摘于百度) (1)当一个session第一次被启用时,一个唯一的标识被存储于本地的cookie中。 (2)首先使用session_start()函数,PHP从session仓库中加载已经存储的session变量。 (3)当执行PHP脚本时,通过使用session_register()函数注册session变量。 (4)当PHP脚本执行结束时,未被销毁的session变量会被自动保存在本地一定路径下的session库中,这个路径可以通过php.ini文件中的session.save_path指定,下次浏览网页时可以加载使用。
其实通俗来讲的话,就是你去超市买东西,办的会员卡记录了你的信息,但是会员卡并不是保存在你这里,而是已数据的方式存在超市的系统中,一旦注册之后可以直接使用。你需要的时候,直接可以使用。但是你一旦离开超市,那个会员卡也就失去了效用直到你的下一次购买。同时,这个会员卡的唯一标识也就是你自己,其他任何人都没有办法使用你的会员卡。直接对号入座就很好理解了。
session和cookie的一大不同点就是,session注册之后直接使用,也就是第一次购买就可以使用,而cookie是经过第一次购买之后才将信息存入会员卡,然后第二次开始使用。
2.session机制图解。
3.session使用方法。
(1)设置session
session_start();
$_SESSION['username']="user";
每一次在使用session之前都需要进行开启session,就当是通常进门都先需要开门一样。而在设置session时和对变量进行赋值没有多大的区别,其实$_SESSION本身就是一个变量。
(2)删除session
这个相对步骤就多了点,而不是cookie里面一句话搞定。
//开启session session_start(); //注销session session_unset(); //销毁session session_destroy(); //同时销毁本地cookie中的sessionid setcookie(session_name(),"",time()-3600,"/");
print_r($_SESSION);
1.cookie与session优缺点。
cookie本身是存放在客户端中,仅占用几kb的内存大小。每次登录网站的时候都会带上本地的cookie进行验证,省去了麻烦的重复输入。但是安全性不是很高,毕竟是存放在本地的文件,虽然都是进行加密了的,一旦电脑数据被盗取,cookie就很有可能会被获取。
session存放在服务器中,占中内存虽小,但是用户基数够大的情况下,会对服务器造成很大的负荷。但是,数据放在服务器上,总归风险降低了许多。虽说没有不透风的墙,不过风也是可以很小很小的,这比喻。。。有同学可能疑问,session使用时,会有sessionid存在本地,一旦获取能否登录。答案当然是否定的,因为每次的id都是不一样的。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1375
1375
 52
52
 The Stable Diffusion 3 paper is finally released, and the architectural details are revealed. Will it help to reproduce Sora?
Mar 06, 2024 pm 05:34 PM
The Stable Diffusion 3 paper is finally released, and the architectural details are revealed. Will it help to reproduce Sora?
Mar 06, 2024 pm 05:34 PM
StableDiffusion3’s paper is finally here! This model was released two weeks ago and uses the same DiT (DiffusionTransformer) architecture as Sora. It caused quite a stir once it was released. Compared with the previous version, the quality of the images generated by StableDiffusion3 has been significantly improved. It now supports multi-theme prompts, and the text writing effect has also been improved, and garbled characters no longer appear. StabilityAI pointed out that StableDiffusion3 is a series of models with parameter sizes ranging from 800M to 8B. This parameter range means that the model can be run directly on many portable devices, significantly reducing the use of AI
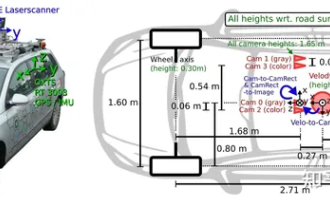 Have you really mastered coordinate system conversion? Multi-sensor issues that are inseparable from autonomous driving
Oct 12, 2023 am 11:21 AM
Have you really mastered coordinate system conversion? Multi-sensor issues that are inseparable from autonomous driving
Oct 12, 2023 am 11:21 AM
The first pilot and key article mainly introduces several commonly used coordinate systems in autonomous driving technology, and how to complete the correlation and conversion between them, and finally build a unified environment model. The focus here is to understand the conversion from vehicle to camera rigid body (external parameters), camera to image conversion (internal parameters), and image to pixel unit conversion. The conversion from 3D to 2D will have corresponding distortion, translation, etc. Key points: The vehicle coordinate system and the camera body coordinate system need to be rewritten: the plane coordinate system and the pixel coordinate system. Difficulty: image distortion must be considered. Both de-distortion and distortion addition are compensated on the image plane. 2. Introduction There are four vision systems in total. Coordinate system: pixel plane coordinate system (u, v), image coordinate system (x, y), camera coordinate system () and world coordinate system (). There is a relationship between each coordinate system,
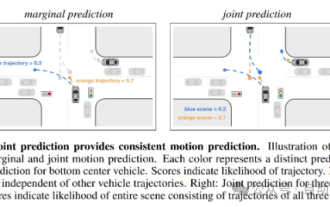 This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
This article is enough for you to read about autonomous driving and trajectory prediction!
Feb 28, 2024 pm 07:20 PM
Trajectory prediction plays an important role in autonomous driving. Autonomous driving trajectory prediction refers to predicting the future driving trajectory of the vehicle by analyzing various data during the vehicle's driving process. As the core module of autonomous driving, the quality of trajectory prediction is crucial to downstream planning control. The trajectory prediction task has a rich technology stack and requires familiarity with autonomous driving dynamic/static perception, high-precision maps, lane lines, neural network architecture (CNN&GNN&Transformer) skills, etc. It is very difficult to get started! Many fans hope to get started with trajectory prediction as soon as possible and avoid pitfalls. Today I will take stock of some common problems and introductory learning methods for trajectory prediction! Introductory related knowledge 1. Are the preview papers in order? A: Look at the survey first, p
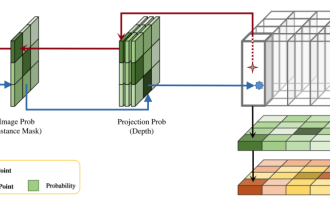 DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
This paper explores the problem of accurately detecting objects from different viewing angles (such as perspective and bird's-eye view) in autonomous driving, especially how to effectively transform features from perspective (PV) to bird's-eye view (BEV) space. Transformation is implemented via the Visual Transformation (VT) module. Existing methods are broadly divided into two strategies: 2D to 3D and 3D to 2D conversion. 2D-to-3D methods improve dense 2D features by predicting depth probabilities, but the inherent uncertainty of depth predictions, especially in distant regions, may introduce inaccuracies. While 3D to 2D methods usually use 3D queries to sample 2D features and learn the attention weights of the correspondence between 3D and 2D features through a Transformer, which increases the computational and deployment time.
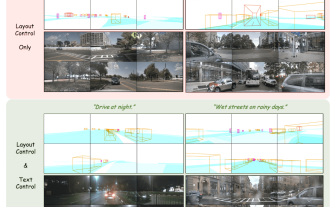 The first multi-view autonomous driving scene video generation world model | DrivingDiffusion: New ideas for BEV data and simulation
Oct 23, 2023 am 11:13 AM
The first multi-view autonomous driving scene video generation world model | DrivingDiffusion: New ideas for BEV data and simulation
Oct 23, 2023 am 11:13 AM
Some of the author’s personal thoughts In the field of autonomous driving, with the development of BEV-based sub-tasks/end-to-end solutions, high-quality multi-view training data and corresponding simulation scene construction have become increasingly important. In response to the pain points of current tasks, "high quality" can be decoupled into three aspects: long-tail scenarios in different dimensions: such as close-range vehicles in obstacle data and precise heading angles during car cutting, as well as lane line data. Scenes such as curves with different curvatures or ramps/mergings/mergings that are difficult to capture. These often rely on large amounts of data collection and complex data mining strategies, which are costly. 3D true value - highly consistent image: Current BEV data acquisition is often affected by errors in sensor installation/calibration, high-precision maps and the reconstruction algorithm itself. this led me to
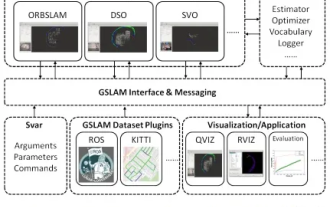 GSLAM | A general SLAM architecture and benchmark
Oct 20, 2023 am 11:37 AM
GSLAM | A general SLAM architecture and benchmark
Oct 20, 2023 am 11:37 AM
Suddenly discovered a 19-year-old paper GSLAM: A General SLAM Framework and Benchmark open source code: https://github.com/zdzhaoyong/GSLAM Go directly to the full text and feel the quality of this work ~ 1 Abstract SLAM technology has achieved many successes recently and attracted many attracted the attention of high-tech companies. However, how to effectively perform benchmarks on speed, robustness, and portability with interfaces to existing or emerging algorithms remains a problem. In this paper, a new SLAM platform called GSLAM is proposed, which not only provides evaluation capabilities but also provides researchers with a useful way to quickly develop their own SLAM systems.
 'Minecraft' turns into an AI town, and NPC residents role-play like real people
Jan 02, 2024 pm 06:25 PM
'Minecraft' turns into an AI town, and NPC residents role-play like real people
Jan 02, 2024 pm 06:25 PM
Please note that this square man is frowning, thinking about the identities of the "uninvited guests" in front of him. It turned out that she was in a dangerous situation, and once she realized this, she quickly began a mental search to find a strategy to solve the problem. Ultimately, she decided to flee the scene and then seek help as quickly as possible and take immediate action. At the same time, the person on the opposite side was thinking the same thing as her... There was such a scene in "Minecraft" where all the characters were controlled by artificial intelligence. Each of them has a unique identity setting. For example, the girl mentioned before is a 17-year-old but smart and brave courier. They have the ability to remember and think, and live like humans in this small town set in Minecraft. What drives them is a brand new,
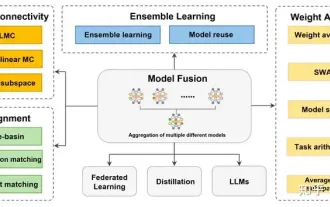 Review! Deep model fusion (LLM/basic model/federated learning/fine-tuning, etc.)
Apr 18, 2024 pm 09:43 PM
Review! Deep model fusion (LLM/basic model/federated learning/fine-tuning, etc.)
Apr 18, 2024 pm 09:43 PM
In September 23, the paper "DeepModelFusion:ASurvey" was published by the National University of Defense Technology, JD.com and Beijing Institute of Technology. Deep model fusion/merging is an emerging technology that combines the parameters or predictions of multiple deep learning models into a single model. It combines the capabilities of different models to compensate for the biases and errors of individual models for better performance. Deep model fusion on large-scale deep learning models (such as LLM and basic models) faces some challenges, including high computational cost, high-dimensional parameter space, interference between different heterogeneous models, etc. This article divides existing deep model fusion methods into four categories: (1) "Pattern connection", which connects solutions in the weight space through a loss-reducing path to obtain a better initial model fusion




