小弟我抱着试试看的心理问个facebook实际开发的有关问题
我抱着试试看的心理问个facebook实际开发的问题
要发送内容到facebook wall,
找了很多资料,都是老版本了。
新版本app id和app key合并了
然后按照网上的教程要得到临时令牌
Give permission (for application) to publish on your wall
地址是https://login.facebook.com/code_gen.php?api_key=YOUR_API_KEY&v=1.0
新版本key就是id,
然后我输入网址,
结果显示
谁做过类似的项目,来说说。。
------解决方案--------------------
请参阅文章如何将facebook关联到你的magento站点

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 what is facebook
Aug 17, 2023 pm 02:05 PM
what is facebook
Aug 17, 2023 pm 02:05 PM
Facebook is a globally renowned social media platform that provides users with a platform to connect and communicate. Founded in 2004, it was founded by Mark Zuckerberg and others. It is an online social network where users can share information, photos and videos with and interact with friends, family and colleagues. Its influence is not limited to individual users, but also extends to businesses and news fields.
 What does the identity attribute in SQL mean?
Feb 19, 2024 am 11:24 AM
What does the identity attribute in SQL mean?
Feb 19, 2024 am 11:24 AM
What is Identity in SQL? Specific code examples are needed. In SQL, Identity is a special data type used to generate auto-incrementing numbers. It is often used to uniquely identify each row of data in a table. The Identity column is often used in conjunction with the primary key column to ensure that each record has a unique identifier. This article will detail how to use Identity and some practical code examples. The basic way to use Identity is to use Identit when creating a table.
 what does facebook mean
Jul 25, 2022 am 11:06 AM
what does facebook mean
Jul 25, 2022 am 11:06 AM
Facebook means an American Internet company, and also refers to the social network service website developed by the company; Facebook was founded on February 4, 2004. It is a world-famous social communication application that users can use Communicate with people around the world.
 How SpringBoot monitors redis Key change events
May 26, 2023 pm 01:55 PM
How SpringBoot monitors redis Key change events
May 26, 2023 pm 01:55 PM
1. Function Overview Keyspace notification allows clients to receive events that modify Rediskey changes in some way by subscribing to channels or patterns. All commands that modify key keys. All keys that received the LPUSHkeyvalue[value…] command. All expired keys in the db database. Events are distributed through Redis's subscription and publishing functions (pub/sub), so all clients that support subscription and publishing functions can directly use the keyspace notification function without any modifications. Because the current subscription and publishing functions of Redis adopt a fireandforget strategy, if your program
 Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
An unpatchable Yubico two-factor authentication key vulnerability has broken the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. The Feitian A22 JavaCard and other devices using Infineon SLB96xx series TPMs are also vulnerable.All
 What is the principle of python WSGI Application?
May 19, 2023 pm 01:25 PM
What is the principle of python WSGI Application?
May 19, 2023 pm 01:25 PM
The python environment this article relies on is: What is WSGI? WSGI is also called the web server universal gateway interface, and its full name is webservergatewayinterface. It defines a standard for how web servers and web applications should communicate and handle http requests and responses in Python. Note that it is just a protocol, or a specification or standard. You don’t have to follow this standard. Just like the web server we wrote in the previous article. WSGI is also divided into applications and server gateways. Among them, the well-known Flask belongs to applications, and uWSGI and wsgiref belong to server gateways. Personal feeling, WSG
 How to solve the problem of batch deletion of key values in redis
May 31, 2023 am 08:59 AM
How to solve the problem of batch deletion of key values in redis
May 31, 2023 am 08:59 AM
Problems encountered: During the development process, you will encounter keys that need to be deleted in batches according to certain rules, such as login_logID (ID is a variable). Now you need to delete data such as "login_log*", but redis itself only has batch query. Command keys for class key values, but there is no command for batch deletion of a certain class. Solution: Query first, then delete, use xargs to pass parameters (xargs can convert pipe or standard input (stdin) data into command line parameters), execute the query statement first, and then remove the queried key value and the original del parameters. delete. redis-cliKEYSkey* (search condition)|xargsr
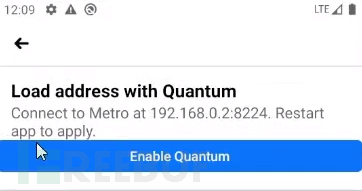 How to use deep linking to backdoor Facebook APP
May 19, 2023 pm 02:49 PM
How to use deep linking to backdoor Facebook APP
May 19, 2023 pm 02:49 PM
Recently, the author discovered a deep link vulnerability in the Facebook Android APP. Using this vulnerability, the Facebook Android APP installed on the user's mobile phone can be converted into a backdoor program (Backdoor) to achieve backdooring. In addition, this vulnerability can also be used to repackage the Facebook APP and send it to specific target victims for installation and use. Let’s take a look at the author’s discovery process of this vulnerability, and how to construct it through Payload and finally transform it into a security risk in the actual production environment of Facebook APP. When I usually do public testing when discovering vulnerabilities, I will first carefully understand the application mechanism of the target system. In my last blog, I have shared how to parse Face






