 Technology peripherals
Technology peripherals
 AI
AI
 How to use artificial intelligence to enhance cloud security for APIs and microservices
How to use artificial intelligence to enhance cloud security for APIs and microservices
How to use artificial intelligence to enhance cloud security for APIs and microservices
Translator| Li Rui
##Reviewer| Chonglou
Overview
API is a set of guidelines and protocols for Facilitates communication between software applications. It outlines the methods by which software components interact, simplifying the process of developing and integrating systems.
#Microservices architecture represents a software development approach that divides large applications into multiple services. Each service focuses on a business function. They can be developed, deployed and scaled autonomously.
Cloud security is very important for APIs and microservices, and here’s why:
Data protection: APIs and microservices often process information. Maintaining security is critical to protecting this data from access, leakage, or destruction.
User Authentication and Authorization: Implementing security protocols in a cloud computing environment helps authenticate the identities of users and services that interact with APIs and microservices. This ensures that authorized entities can use the service.
# (3) Compliance with regulations: Many industries have regulations regarding data privacy and security. Adhering to cloud security practices ensures compliance with these requirements.
# Ensure secure communication: APIs and microservices rely on network communication. These channels are protected with encryption and other safeguards to prevent data interception or tampering. These channels are critical to preventing data interception, interception or tampering.
(5) Mitigating DDoS attacks: An effective cloud security strategy can help minimize the impact of distributed denial of service (DDoS) attacks, which There is the potential to disrupt the availability of the Service. By defending against attacks, the reliability of APIs and microservices is maintained.
(6) Protect infrastructure: APIs and microservices running in a cloud computing environment are integral parts of the infrastructure. Security measures play an important role in protecting cloud computing infrastructure from vulnerabilities that could be exploited.
For APIs and microservices, prioritizing cloud security is critical to protecting data, ensuring compliance, maintaining service availability, and protecting systems from cyber threats. It's important.
Challenges faced by cloud security without the help of artificial intelligence
Without the help of artificial intelligence Addressing cloud security challenges without the help of intelligence can be quite complex. Here are some typical obstacles:
(1) Timely identification and response to evolving cyber threats is critical to maintaining security. Without the help of AI-powered threat detection capabilities, organizations may find it difficult to detect threats that can evade security measures.
# (2) Manual implementation of security procedures is time-consuming and error-prone. AI technology provides the ability to automate security tasks such as vulnerability scanning, patch management, and incident response, allowing security teams to focus on strategic work.
# (3) Identifying anomalies in user behavior or network traffic patterns is critical to identifying security vulnerabilities. AI can sift through large amounts of data, spot behavioral deviations, and raise alerts for further review.
# (4) Given the ever-changing nature of cloud computing setups, keeping a close eye on all assets and operations can present challenges. Without the support of AI-enhanced monitoring tools, quickly detecting and resolving security incidents becomes a rather daunting task.
# (5) Cloud computing environments scale as needed, which makes ensuring security controls across all instances tricky. Artificial intelligence can help automate the enforcement of security policies and ensure that security measures are scalable along with the infrastructure.
Artificial intelligence enhances the security of APIs and microservices

AI-enhanced cloud security solutions play a role in protecting APIs and microservices from emerging cyber threats and vulnerabilities. Here are some basic ways AI can enhance API and microservice cloud security:
(1) Detect and respond to threats: Security tools enhanced by AI can Analyze data to identify security threat patterns, respond to incidents promptly, and prevent data leaks and unauthorized system access.
# (2) Detect anomalies: Artificial intelligence algorithms can identify behaviors in API requests and microservice activities, identifying activities, potential attacks, or unauthorized access Try raising an alert.
(3) Behavioral analysis: Artificial intelligence analyzes users and applications interacting with APIs and microservices, identifying normal behavior patterns and possible indicators of security Risk bias.
(4) Monitor API traffic: Artificial intelligence tools monitor API traffic, analyze request patterns, and detect anomalies to pinpoint security issues such as DDoS attacks, data leaks, or malicious activities.
(5) Automatic execution of security policies: The artificial intelligence system automatically executes the security policies of APIs and microservices to ensure the application of security measures while maximizing Reduce the risk of errors.
# (6) Vulnerability management: AI-enhanced systems can scan APIs and microservices to identify vulnerabilities and prioritize patching based on risk assessment. They provide recommendations for strengthening security in response to threats and risks.
# (7) Integrated threat intelligence: Security platforms enhanced by artificial intelligence can integrate threat intelligence to keep up with emerging threats, patterns and attack methods. This integration facilitates API and microservice defense strategies.
Organizations aiming to strengthen cybersecurity defenses, protect information, and secure cloud-based applications must implement AI-driven security for APIs and microservices measure. By leveraging AI technology, organizations can improve their ability to detect threats, reduce incident response times, and strengthen security in a rapidly evolving digital environment.
1. Detect and respond to threats
Ensure that cloud computing-based APIs and microservices A service's threat detection and response mechanisms are critical to maintaining the security and reliability of the infrastructure. Here’s how AI can be leveraged for threat detection and response in situations like this:
- Real-time network traffic scanning: AI tools can continuously Observe network traffic, API requests, and interactions between microservices to promptly pinpoint any violations, suspicious activity, or unauthorized access attempts.
- Machine Learning Models: Machine learning models enhanced with artificial intelligence can identify cyber threats, proactively, by scrutinizing data sets to detect patterns that recommend actions. Identify and respond to threats.
- Automated Incident Response: The ability to respond to security events by triggering predefined actions, such as isolating a compromised service, blocking traffic, or isolating an affected system. Automate incident response processes.
- Forensic analysis: Artificial intelligence tools can help analyze events after they occur, reconstructing the sequence of events and pinpointing security risks by reviewing logs, audit trails and network activity. The cause of the vulnerability and guide remediation efforts.
- Adaptive security measures: AI has the ability to adjust security controls and settings in response to changing threats, enabling cloud-based APIs and microservices to Adapt to changing risks and vulnerabilities.
2. Detect anomalies
Anomaly detection in artificial intelligence driven APIs and microservices play a role in enabling systems to identify deviations from patterns or behaviors. This functionality is critical to ensuring the reliability, security and efficiency of the service.
In the world of AI-enhanced APIs and microservices, algorithms that detect violations can be used to monitor request/response times, traffic, error rates, and resource utilization rate and other indicators. By checking these indicators in a timely manner, any anomalies can be identified promptly, facilitating intervention and solving potential problems.
Incorporating anomaly detection into AI-enhanced APIs and microservices requires leveraging machine learning models and algorithms to establish behavioral patterns. Any deviation from these patterns may trigger alerts or automated responses to address risks or performance issues.
By integrating irregularity detection into AI-enhanced APIs and microservices, organizations can improve the reliability, security, and effectiveness of their systems, ultimately Improve user experience and operational efficiency.
3. Behavioral Analysis
When it comes to AI-driven APIs and micro When providing the Services, analyzing user behavior includes monitoring and evaluating behaviors, trends and preferences. By observing how users interact with these services, organizations can discover different patterns, anomalies, and areas for improvement.
#The analysis covers aspects such as user engagement, response times, error frequency, and usage trends. With the help of AI tools, organizations can collect information about user behavior to tailor their services effectively.
# By analyzing AI-enhanced APIs and microservices, organizations can identify roadblocks, security risks, or areas that require performance upgrades. By understanding user behavior, businesses can improve the availability and responsiveness of their services.
Holistic integration of AI-enhanced APIs and microservices analytics can increase user satisfaction, increase system efficiency, and make informed decisions based on data-driven insights decision making.
Here are some popular tools commonly used to analyze behavior in AI-enhanced APIs and microservices:
- Google Analytics: In addition to being used for web analytics, Google Analytics can also track user behavior in APIs and microservices, providing insights into user engagement, interaction, and conversion rates.
- Mixpanel: An analytics platform specializing in event tracking, Mixpanel allows organizations to monitor user behavior such as feature usage, retention and users across APIs and microservices path.
- Amplitude: Another tool focused on product analysis and behavior analysis, Amplitude Help organizations understand user behavior through cohort analysis and tracking user journeys for applications and services.
- Hotjar: Providing heatmaps, session recordings, and user feedback tools for analytics purposes, Hotjar visually demonstrates how users consume APIs and microservices.
- Kibana: Part of the Elastic Stack, Kibana is a data visualization tool for analyzing log data to identify user behavior patterns in APIs and microservices , anomalies and trends.
4. Monitor API traffic
Monitoring API traffic is essential to ensure manual The efficiency, security, and reliability of smart APIs and microservices are critical. By monitoring API traffic, organizations can monitor, analyze, and enhance data flows and requests within their systems. This monitoring helps pinpoint issues, anomalies, and patterns that may affect the normal operation of APIs and microservices.
# In an AI-enhanced environment, a variety of tools and methods can be used to monitor API traffic.
- Monitor API gateways: These gateways serve as entry points to APIs and provide insights into incoming and outgoing traffic. Tools like Kong, APIgee, or AWS API Gateway can monitor metrics such as request rate, response time, and error rate.
- Logging and tracing: Incorporating logging and tracing mechanisms in APIs and microservices can capture detailed information about API traffic.
- API Monitoring Tools: Because tools like Elasticsearch, Logstash and Kibana (ELK stack) are moving in the system, They are able to analyze logs and track requests. For monitoring APIs, you can use tools like Postman, Insomnia, or Paw to observe API endpoints, send trial requests, and measure response times. These tools have proven valuable for gaining insight into API behavior from a user's perspective.
- Real-time monitoring solutions: To enable real-time monitoring of APIs and microservices, solutions such as Prometheus, Grafana or Datadog provide features that enable organizations to Instantly visualize metrics, create alerts, and analyze performance in real-time.
- Traffic analysis tools: When it comes to analyzing network traffic and inspecting payloads in API communications, tools like Wireshark, Fiddler, or Charles Proxy can provide useful opinion.
- Security Monitoring Solutions: To enhance security measures around API traffic, security solutions such as OWASP ZAP, Burp Suite, or AWS WAF can be leveraged to effectively monitor security threats, anomalies, and vulnerabilities.
5. Automatic execution of security policies
Ensure the security of AI-driven APIs and microservices Security and confidentiality require automated enforcement of security policies. By automating this process, organizations can apply , monitor and enforce security measures consistently across their systems. Here are some specific strategies and tools that can be used to automate security policies in AI-driven APIs and microservices:
- 基於令牌的身份驗證:採用基於令牌的身份驗證機制,例如OAuth 2.0或JSON Web令牌(JWT)來驗證和授權存取API和微服務;用於發布命令牌和驗證令牌的自動化流程。撤銷它們有助於增強安全性。
- 安全策略即程式碼:使用開放式策略代理程式(OPA)或HashiCorp Sentinel等工具將安全性原則定義為程式碼。透過將安全性策略轉換為程式碼格式,組織可以在整個軟體開發生命週期中自動化其實現。
- 行為分析工具:利用Splunk、Elastic Security或IBM QRadar等分析工具,可以監控和評估使用者行為,以識別違規行為,並維護API和微服務內活動的安全協定。
- 存取控制清單(ACL):實現存取控制清單有助於根據既定法規限制對API端點和微服務的訪問,並透過自動化管理確保只有授權使用者或服務才能存取資源。
- 運行時應用程式自我保護(RASP):採用運行時(Runtime)應用程式自我保護(RASP)解決方案,例如Contrast Security或Veracode,涉及將安全性策略嵌入到API執行時間環境中,以強制執行針對注入攻擊和資料暴露等常見威脅的措施。
6.漏洞管理
#有效的漏洞管理透過辨識、評估、緩解和監控漏洞來保護系統免受潛在的安全風險和破壞,在保護人工智慧驅動的API和微服務方面發揮重要作用。
以下是一些重要的策略和工具,用於管理人工智慧驅動的API和微服務中的漏洞:
- 定期漏洞掃描:利用Nessus、Qualys或OpenVAS等掃描工具檢查API和微服務是否有已知漏洞。一致的掃描有助於找出攻擊者可能利用的弱點。
- 安全性修補程式:建立一個管理修補程式的流程,以確保軟體元件和相依性與安全性修補程式保持更新。及時打補丁可以解決已知的漏洞,降低攻擊的風險。
- 安全程式碼審查:定期檢視程式碼的安全性問題,以解決不安全的做法和漏洞。像SonarQube、Checkmarx或Fortify這樣的工具可以自動進行程式碼分析,以偵測程式碼庫中的安全缺陷。
- API安全實踐:遵循API開發實踐,包括身分驗證、授權、加密、輸入驗證和錯誤處理。堅持這些實踐可以減少攻擊面,增強API和微服務的安全性。
- 整合威脅情報:整合威脅情報,及時更新與人工智慧驅動的API和微服務相關的新出現的安全威脅和漏洞。像ThreatConnect或Recorded Future這樣的工具可以幫助偵測和回應威脅。
- 事件回應計畫:制定回應涉及API和微服務漏洞事件處理過程的計畫。該計劃應該概述處理安全事件的過程,包括修補漏洞的步驟、通訊策略和復原過程。
7.整合威脅情報
將威脅情報整合到人工在智慧驅動的API和微服務中,以加強安全措施,識別威脅並有效管理風險,這一點至關重要。透過利用威脅情報資源,組織可以隨時了解可能對其API和微服務構成風險的威脅、漏洞和惡意活動。
以下是一些在人工智慧驅動的環境中整合威脅情報的重要策略和工具:
- 威脅情報反 饋送來源:透過訂閱CERT、ISAC和商業提供者等可信任來源的威脅情報來維持最新資訊。這些提要提供了對已知威脅、入侵指標(IOC)以及與API和微服務相關的攻擊模式的即時洞察。
- 整合安全資訊與事件管理(SIEM):將威脅情報饋送整合到SIEM解決方案中,例如Splunk, ArcSight或logrhym。這種整合有助於關聯安全事件,分析日誌,並根據威脅情報提供的指標識別威脅。
- 監控入侵#指標(IOC):在API和微服務流量資料和系統活動的日誌中,監視來自威脅情報饋送的監控入侵#指標(IOC)匹配。像MISP(惡意軟體資訊共享平台)或OpenCTI這樣的工具對於管理和關聯監控入侵指標(IOC)很有價值。
- 實現安全編排、自動化和回應(SOAR):部署SOAR平台,例如Demisto、Phantom或Swimlane,以自動執行與管理威脅情報相關的任務。這些平台簡化了專為API和微服務設計的事件回應流程和修復工作流程。利用機器學習演算法分析來自威脅情報的數據,識別模式,並預測人工智慧驅動的API和微服務中的安全事件。機器學習模型可以增強偵測威脅和有效地自動回應措施的能力。
結論
#透過整合基於人工智慧的技術來偵測並回應基於雲端運算的API和微服務環境中的威脅,組織可以加強其網路安全防禦,提高事件回應能力,並保護其資產免受網路威脅。
原文標題:#Leveraging AI to Bolster Cloud Security for APIs and Microservices,作者:Nilesh Charankar
The above is the detailed content of How to use artificial intelligence to enhance cloud security for APIs and microservices. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1381
1381
 52
52
 Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
Bytedance Cutting launches SVIP super membership: 499 yuan for continuous annual subscription, providing a variety of AI functions
Jun 28, 2024 am 03:51 AM
This site reported on June 27 that Jianying is a video editing software developed by FaceMeng Technology, a subsidiary of ByteDance. It relies on the Douyin platform and basically produces short video content for users of the platform. It is compatible with iOS, Android, and Windows. , MacOS and other operating systems. Jianying officially announced the upgrade of its membership system and launched a new SVIP, which includes a variety of AI black technologies, such as intelligent translation, intelligent highlighting, intelligent packaging, digital human synthesis, etc. In terms of price, the monthly fee for clipping SVIP is 79 yuan, the annual fee is 599 yuan (note on this site: equivalent to 49.9 yuan per month), the continuous monthly subscription is 59 yuan per month, and the continuous annual subscription is 499 yuan per year (equivalent to 41.6 yuan per month) . In addition, the cut official also stated that in order to improve the user experience, those who have subscribed to the original VIP
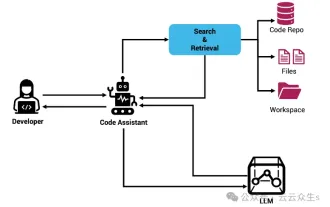 Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Context-augmented AI coding assistant using Rag and Sem-Rag
Jun 10, 2024 am 11:08 AM
Improve developer productivity, efficiency, and accuracy by incorporating retrieval-enhanced generation and semantic memory into AI coding assistants. Translated from EnhancingAICodingAssistantswithContextUsingRAGandSEM-RAG, author JanakiramMSV. While basic AI programming assistants are naturally helpful, they often fail to provide the most relevant and correct code suggestions because they rely on a general understanding of the software language and the most common patterns of writing software. The code generated by these coding assistants is suitable for solving the problems they are responsible for solving, but often does not conform to the coding standards, conventions and styles of the individual teams. This often results in suggestions that need to be modified or refined in order for the code to be accepted into the application
 Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Can fine-tuning really allow LLM to learn new things: introducing new knowledge may make the model produce more hallucinations
Jun 11, 2024 pm 03:57 PM
Large Language Models (LLMs) are trained on huge text databases, where they acquire large amounts of real-world knowledge. This knowledge is embedded into their parameters and can then be used when needed. The knowledge of these models is "reified" at the end of training. At the end of pre-training, the model actually stops learning. Align or fine-tune the model to learn how to leverage this knowledge and respond more naturally to user questions. But sometimes model knowledge is not enough, and although the model can access external content through RAG, it is considered beneficial to adapt the model to new domains through fine-tuning. This fine-tuning is performed using input from human annotators or other LLM creations, where the model encounters additional real-world knowledge and integrates it
 Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
Seven Cool GenAI & LLM Technical Interview Questions
Jun 07, 2024 am 10:06 AM
To learn more about AIGC, please visit: 51CTOAI.x Community https://www.51cto.com/aigc/Translator|Jingyan Reviewer|Chonglou is different from the traditional question bank that can be seen everywhere on the Internet. These questions It requires thinking outside the box. Large Language Models (LLMs) are increasingly important in the fields of data science, generative artificial intelligence (GenAI), and artificial intelligence. These complex algorithms enhance human skills and drive efficiency and innovation in many industries, becoming the key for companies to remain competitive. LLM has a wide range of applications. It can be used in fields such as natural language processing, text generation, speech recognition and recommendation systems. By learning from large amounts of data, LLM is able to generate text
 Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Five schools of machine learning you don't know about
Jun 05, 2024 pm 08:51 PM
Machine learning is an important branch of artificial intelligence that gives computers the ability to learn from data and improve their capabilities without being explicitly programmed. Machine learning has a wide range of applications in various fields, from image recognition and natural language processing to recommendation systems and fraud detection, and it is changing the way we live. There are many different methods and theories in the field of machine learning, among which the five most influential methods are called the "Five Schools of Machine Learning". The five major schools are the symbolic school, the connectionist school, the evolutionary school, the Bayesian school and the analogy school. 1. Symbolism, also known as symbolism, emphasizes the use of symbols for logical reasoning and expression of knowledge. This school of thought believes that learning is a process of reverse deduction, through existing
 To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
To provide a new scientific and complex question answering benchmark and evaluation system for large models, UNSW, Argonne, University of Chicago and other institutions jointly launched the SciQAG framework
Jul 25, 2024 am 06:42 AM
Editor |ScienceAI Question Answering (QA) data set plays a vital role in promoting natural language processing (NLP) research. High-quality QA data sets can not only be used to fine-tune models, but also effectively evaluate the capabilities of large language models (LLM), especially the ability to understand and reason about scientific knowledge. Although there are currently many scientific QA data sets covering medicine, chemistry, biology and other fields, these data sets still have some shortcomings. First, the data form is relatively simple, most of which are multiple-choice questions. They are easy to evaluate, but limit the model's answer selection range and cannot fully test the model's ability to answer scientific questions. In contrast, open-ended Q&A
 SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
SOTA performance, Xiamen multi-modal protein-ligand affinity prediction AI method, combines molecular surface information for the first time
Jul 17, 2024 pm 06:37 PM
Editor | KX In the field of drug research and development, accurately and effectively predicting the binding affinity of proteins and ligands is crucial for drug screening and optimization. However, current studies do not take into account the important role of molecular surface information in protein-ligand interactions. Based on this, researchers from Xiamen University proposed a novel multi-modal feature extraction (MFE) framework, which for the first time combines information on protein surface, 3D structure and sequence, and uses a cross-attention mechanism to compare different modalities. feature alignment. Experimental results demonstrate that this method achieves state-of-the-art performance in predicting protein-ligand binding affinities. Furthermore, ablation studies demonstrate the effectiveness and necessity of protein surface information and multimodal feature alignment within this framework. Related research begins with "S
 SK Hynix will display new AI-related products on August 6: 12-layer HBM3E, 321-high NAND, etc.
Aug 01, 2024 pm 09:40 PM
SK Hynix will display new AI-related products on August 6: 12-layer HBM3E, 321-high NAND, etc.
Aug 01, 2024 pm 09:40 PM
According to news from this site on August 1, SK Hynix released a blog post today (August 1), announcing that it will attend the Global Semiconductor Memory Summit FMS2024 to be held in Santa Clara, California, USA from August 6 to 8, showcasing many new technologies. generation product. Introduction to the Future Memory and Storage Summit (FutureMemoryandStorage), formerly the Flash Memory Summit (FlashMemorySummit) mainly for NAND suppliers, in the context of increasing attention to artificial intelligence technology, this year was renamed the Future Memory and Storage Summit (FutureMemoryandStorage) to invite DRAM and storage vendors and many more players. New product SK hynix launched last year



