How to Stop Apps From Leaking Your Data
These days, smartphones can do it all. Unfortunately, they can also track it all. Smartphones have become a data mining gold mine, but you're not powerless—there are things you can do to make yours less accessible and valuable to those who seek profit from your activity.
The steps and screenshots shown below are from a Google Pixel phone. The exact location of these settings may be different on your device, but you can also search the settings app to find things more easily.
Keep Tabs on Your Phone's Permissions
There are certain parts of your phone that apps have to request permission to access. An app cannot open the camera unless you first give it permission. It cannot access the microphone. It cannot search through your files.
Some of the apps that your phone came with may have permissions that you wish to revoke, or you may have granted undesirable permissions to apps you installed without paying much attention. You can change this by opening Settings > Security & Privacy > Privacy > Permission Manager.

Check the Privacy Dashboard
Since Android 12, phones come with a feature known as the Privacy Dashboard. The Privacy Dashboard shows not only which apps have what permissions but also how often and how recently they've accessed them. You can click on an app that seems to be abusing its privileges and prevent it from having access in the future.
Go to Settings > Security & Privacy > Privacy > Privacy Dashboard. Here is how to access the privacy dashboard on a Samsung device.

Stop Google Collecting App Data
When you first set up an Android device, if you say yes to every question Google asks during setup, you will supply the search giant with a lot of information about you. Fortunately, you can tell Google not to collect this information. In some cases, such as your web browsing and YouTube viewing history or your location data, you can even tell Google to delete it. You can also set up an auto-delete schedule so that Google can only save recently generated data.
You can audit these options by going to Settings > Security & Privacy > Privacy > Activity Controls.

Revoke Permissions for Unused Apps
While it's helpful to check permissions every few months periodically, that's often not something we're going to remember to do. Thankfully, Android can automatically revoke permissions for apps that haven't been used in a while.
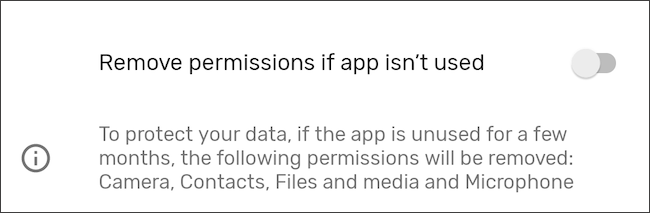
On newer phones, this feature may already be enabled. To be sure, go to Settings > Apps and select an app. Scroll down to "Pause App Activity if Unused" and activate the toggle. In addition to revoking permissions, this will also delete temporary files and stop notifications from said app.
On a Samsung device, the steps are the same, but the wording has been changed to "Remove Permissions if App is Unused."
Uninstall Unused Apps
Many apps that we want or need tend to collect a lot of data in the background. Some social networking, video streaming, shopping, image editing, and other such apps can track what we do with our phones even when not in use. We may accept this quietly when an app provides functionality that we are using often, but if we are no longer using an app, there's no reason to let it continue quietly sucking up this data.
Scroll through your app drawer and take note of which apps you no longer use—then remove them. You can do this by holding down an app icon and selecting "App Info." Then, hit the uninstall button. On some phones, you can just press down on an icon and select "Uninstall."
Check an App on Exodus Privacy Before Installing
Permissions tell you a lot, but they don't tell you the whole story. They tell you mechanisms that an app can use for tracking, but they don't tell you whether an app actually is. That's where Exodus comes in. This is an Android app auditing service that comes from a nonprofit based in Europe.
You can check whether an app contains known trackers by heading to the Exodus search tool and entering the app's name. Exodus also provides a free and open source app that can automatically scan the apps already on your device. The Exodus app is available in the Play Store and on F-Droid.
Only Install Apps From Verified Sources
Out of the box, you can only install apps from pre-certified app stores like the Play Store and the Galaxy Store. If you try to install an Android APK file directly from your web browser or from a third-party source like TapTap, your phone will try to block this install. That's because many malicious apps are distributed as APKs that would not be safely allowed in the certified app stores.
For most people, sticking to the default stores is a pretty good rule of thumb. Yet this is not to say that people, especially more technical users, should never install apps from alternative places (some third-party sources like the free and open-source F-Droid repositories are arguably safer sources of software than the Play Store). Rather, do your due diligence, and be sure to only install software from places you can trust.
Review an App's Permissions Before Installing
You can actually view which permissions an app will require directly inside the Play Store before you even install it. This way, a greedy program never even sets foot on your device.
Scroll down to "About This App" on the Play Store listing, then scroll again to "App Permissions" and tap "See More." Here, you can view the permissions that the app will request access to after installation.

Read App Privacy Policies
Many apps come with a privacy policy, especially if the app is an anchor to an online service. While it is tempting to check the necessary boxes during the initial launch and move on with your life, at least give the privacy policy a quick skim. You will sometimes see something that you really aren't comfortable with.
A smart home app, for example, might show that it not only collects your IP address and your physical location but that it may share this information with third parties for advertising purposes. That means you aren't just giving that information over to one company but sales companies, data brokers, or tech giants like Google and Facebook, who are known to buy up data from other sources. A privacy policy won't come right out and say that its service is shady, but it sure might imply it.
Performing all of these steps won't guarantee your privacy, but it will help. To take things further, you can use a VPN to mask your IP address. You can also use email aliases when signing up for new apps. And if you really want to be certain nothing is going on in the background, you can install a firewall like NetGuard.
The above is the detailed content of How to Stop Apps From Leaking Your Data. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1662
1662
 14
14
 1419
1419
 52
52
 1312
1312
 25
25
 1262
1262
 29
29
 1235
1235
 24
24
 6 Best Gemini Features to Try on Your Google Pixel 9
Apr 15, 2025 am 01:09 AM
6 Best Gemini Features to Try on Your Google Pixel 9
Apr 15, 2025 am 01:09 AM
Unlock the Power of AI on Your Google Pixel 9: A Guide to Essential Features Google Pixel 9 users enjoy a suite of powerful AI-driven features. This guide highlights several, from photo enhancements to real-time translation. Let's explore what your
 Pixel 9a vs. Samsung Galaxy A56: Which Is the Better Deal?
Apr 15, 2025 am 03:02 AM
Pixel 9a vs. Samsung Galaxy A56: Which Is the Better Deal?
Apr 15, 2025 am 03:02 AM
Google Pixel 9a vs. Samsung Galaxy A56: A Detailed Comparison Google's Pixel 9a and Samsung's Galaxy A56 are strong contenders in the mid-range smartphone market, both boasting impressive features at a $499 starting price. However, the ideal choice
 You Don't Have to Choose Between iPhone and Android With the New Chipolo Pop Tracker
Apr 17, 2025 am 03:01 AM
You Don't Have to Choose Between iPhone and Android With the New Chipolo Pop Tracker
Apr 17, 2025 am 03:01 AM
Chipolo Pop Bluetooth Tracker Review: Taking into account both Apple and Android Losing your keys or wallet is a headache. Chipolo has been committed to helping users find lost items, and their latest product Pop is designed to meet the needs of both iPhone and Android users. It combines some of the best features of previous trackers to become a multi-functional device. If you have used Chipolo’s tracker before, you will notice that Pop has a similar colorful look as the previous Chipolo tracker. The key difference, however, is that it can work with both Apple's Find My Devices networks and Google's Find My Devices networks. Previously, you had to make a choice: iPhone users use Chi
 Android 15 Says Goodbye to 16GB Phones
Apr 17, 2025 am 12:54 AM
Android 15 Says Goodbye to 16GB Phones
Apr 17, 2025 am 12:54 AM
Android devices with Google Play Store must now have at least 32GB of internal storage. This move aims to curb the issue of budget devices quickly running out of space. The updated Google Mobile Services (GMS) agreement mandates a minimum of 32GB int
 The Pixel 10 Camera Leak Has Me Excited (And Slightly Concerned)
Apr 15, 2025 am 12:56 AM
The Pixel 10 Camera Leak Has Me Excited (And Slightly Concerned)
Apr 15, 2025 am 12:56 AM
Pixel 10 Leaks: A Telephoto Lens, But at What Cost? The anticipation surrounding Pixel leaks is always exciting, especially given Google's knack for delivering impressive smartphone experiences—clean Android, seamless AI integration, and surprisingly
 Samsung's Big Android 15 Update Is Finally Rolling Out
Apr 09, 2025 am 01:04 AM
Samsung's Big Android 15 Update Is Finally Rolling Out
Apr 09, 2025 am 01:04 AM
Samsung One UI 7 update officially launches! The Galaxy S24 series was the first to try it out, with the Z Fold 6 and Flip 6 following behind. This update brings major interface revisions, new control experiences and more Galaxy AI features. Official update schedule shows that the Galaxy S23 series and Tab S10 will receive updates in April, and other device updates will last until June. After a long wait, Samsung finally began to officially push the One UI 7 update based on Android 15, and the Galaxy S24 series became the first batch of beneficiary models. While this is exciting and it starts pushing on April 7 as scheduled, not all news is satisfying. After several months
 Samsung's One UI 7 Has Changed How I Feel About Default Android Launchers
Apr 08, 2025 am 12:59 AM
Samsung's One UI 7 Has Changed How I Feel About Default Android Launchers
Apr 08, 2025 am 12:59 AM
I've always used alternative launchers on my Android phones. But Samsung's One UI 7, now rolling out to Galaxy devices, is the first I actually love. Android's customizable home screen has always been a key draw, but One UI 7's attention to detail
 Plex Updates, the Pixel 9a, and a Whole Lot of Tariffs: Weekly Roundup
Apr 15, 2025 am 12:54 AM
Plex Updates, the Pixel 9a, and a Whole Lot of Tariffs: Weekly Roundup
Apr 15, 2025 am 12:54 AM
This week's tech headlines are packed with exciting news! From new phone releases and app updates to price hikes and software support changes, there's plenty to unpack. Here's a summary of the biggest stories you might have missed: Major Announcement




