 Hardware Tutorial
Hardware Tutorial
 Hardware News
Hardware News
 Exposure of encryption keys causes secure boot to fail, affecting nearly 500 models of devices from Dell, Acer, Lenovo, etc.
Exposure of encryption keys causes secure boot to fail, affecting nearly 500 models of devices from Dell, Acer, Lenovo, etc.
Exposure of encryption keys causes secure boot to fail, affecting nearly 500 models of devices from Dell, Acer, Lenovo, etc.
According to news from this site on July 26, the technology media arstechnica published a blog post today (July 26) stating that more than 200 models of the five major equipment manufacturers Acer, Dell, Gigabyte, Intel and Supermicro have safe boot issues. (Secure Boot) problem.
It is reported that the encryption key that supports the secure boot of the above-mentioned devices has been leaked in 2022.

In December 2022, someone working for multiple US device manufacturers published the platform key, which forms a root-of-trust anchor between hardware devices and their firmware, in a GitHub public repository encryption key.
The repository is located at https://github.com/raywu-aaeon/Ryzen2000_4000.git. As of the publication of this website, the link has been deleted.
Binarly researchers discovered the key in January 2023 while investigating a supply chain incident, scanning firmware images for certificate serial numbers 55:fb:ef:87:81:23:00:84:47:17 :0b:b3:cd:87:3a:f4 Identification, a total of 215 devices using leaked keys were found.
Researchers quickly discovered that the leak of this key was just the beginning of a larger supply chain failure, with serious issues with Secure Boot integrity on nearly 300 additional device models from nearly every major device manufacturer. In addition to the five manufacturers mentioned earlier, they also include Aopen, Foremlife, Fujitsu, HP, Lenovo, etc.
These keys were created by AMI, one of the three major providers of software developer toolkits used by device manufacturers to customize UEFI firmware to run on specific hardware configurations.



The above is the detailed content of Exposure of encryption keys causes secure boot to fail, affecting nearly 500 models of devices from Dell, Acer, Lenovo, etc.. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1421
1421
 52
52
 1316
1316
 25
25
 1266
1266
 29
29
 1239
1239
 24
24
 What is Dell's 24-hour after-sales customer service phone number?
Jan 05, 2024 am 11:11 AM
What is Dell's 24-hour after-sales customer service phone number?
Jan 05, 2024 am 11:11 AM
Dell's national after-sales service hotline is 400-818-8484 24 hours a day. Some specific series of Dell products have dedicated after-sales service telephone numbers, for example: 1. Dell lnspirom series after-sales phone: 800-858-296, mobile phone: 400-886-8611; 2. Dell XPS & Alinware series after-sales phone: 800=858=0540 , Mobile phone: 400-886-8611; 3. Dell PremiumSupport service series after-sales landline phones, etc.
 Exposure of encryption keys causes secure boot to fail, affecting nearly 500 models of devices from Dell, Acer, Lenovo, etc.
Jul 26, 2024 pm 01:41 PM
Exposure of encryption keys causes secure boot to fail, affecting nearly 500 models of devices from Dell, Acer, Lenovo, etc.
Jul 26, 2024 pm 01:41 PM
According to news from this website on July 26, the technology media arstechnica published a blog post today (July 26) stating that more than 200 models of the five major equipment manufacturers Acer, Dell, Gigabyte, Intel and Supermicro have safe boot ( SecureBoot) problem. According to reports, the encryption key that supports the secure boot of the above-mentioned devices has been leaked in 2022. Someone working for multiple U.S. device manufacturers published the platform key, the encryption key that forms the root-of-trustanchor between a hardware device and its firmware, in a GitHub public repository in December 2022. The repository is located at https://github.com/ra
 Acer Shadow Knight RX7800 XT OC graphics card is now available: dual fan cooling, 3899 yuan
Apr 07, 2024 pm 09:25 PM
Acer Shadow Knight RX7800 XT OC graphics card is now available: dual fan cooling, 3899 yuan
Apr 07, 2024 pm 09:25 PM
According to news from this site on April 7, the Acer Shadow Knight (Nitro) RX7800XTOC graphics card made its debut at CES2024 and is now on the official Acer China website, priced at 3,899 yuan. The Acer Shadow Knight RadeonRX7800XTOC graphics card uses a 2.5-slot dual fan configuration, has a maximum acceleration frequency of 2565MHz, 16GBGDDR6 video memory, dual 8Pin power supply, and the graphics card TGP is set to 281W. Acer claims that the FrostBlade fast-cooling fan used in this graphics card uses a dragon-wing blade design and double ball bearings. Compared with ordinary axial flow fans, the air flow increases by 9.7% and the noise decreases by 2.4dBA. Additionally, the graphics card measures 279x129.62x50.42
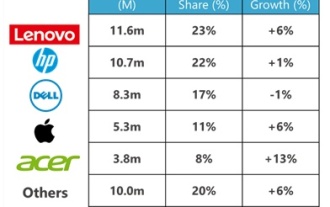 Dell reorganizes sales team, lays off employees and establishes new AI department
Aug 07, 2024 pm 07:05 PM
Dell reorganizes sales team, lays off employees and establishes new AI department
Aug 07, 2024 pm 07:05 PM
According to news from this site on August 6, according to a report by Bloomberg today, Dell Technologies is laying off employees as part of a reorganization of its sales team. The restructuring measures also include establishing a new team focused on AI products and services. "We are becoming leaner," sales team executives Bill Scannell and John Byrne wrote in a memo to Dell employees on Monday. "We are streamlining management and reprioritizing investments." In addition to the team focused on artificial intelligence, Executives also said the company will change the way data center sales work. A spokesman declined to comment on how many jobs would be affected. "Through a reorganization of our market-facing teams and a series of actions, we are becoming a leaner company," the spokesperson said.
 How to solve the problem that Dell cannot upgrade to Win11
Jan 03, 2024 pm 03:37 PM
How to solve the problem that Dell cannot upgrade to Win11
Jan 03, 2024 pm 03:37 PM
There are many friends using Dell now, so system problems often occur, including the problem that Dell cannot upgrade to win11. In fact, not all Dell computers are compatible with win11, and it needs to be judged according to the model. Dell cannot upgrade win11 solution: 1. First, we can check which Dell computers support win11. 2. The models in the list can be directly upgraded to win11 system in the "Update and Security" of win10. 3. If we find that our aircraft model is not listed here, it means that helicopter flight is not possible. 4. Then you can download the one-click installation of win11 from this site. 5. After downloading, right-click the file and click "Load" 6. Then open the folder and run "One-click installation system.exe" to install
 The new Dell P-Series and S-Series monitors are launched to meet the all-in-one experience for work, entertainment and daily life
Mar 14, 2024 am 10:13 AM
The new Dell P-Series and S-Series monitors are launched to meet the all-in-one experience for work, entertainment and daily life
Mar 14, 2024 am 10:13 AM
On March 12, 2024, Dell Technology Group held the "Dell China 2024 Monitor New Product Launch Conference" with the theme of "Expanding Vision and Initiating a New Chapter". It is aimed at business people who pursue high work efficiency, as well as those who pursue entertainment enjoyment and lasting comfort. For families, students and ordinary consumers, a variety of new P series and S series monitors have been launched. Mr. Wu Hailiang, global vice president of Dell Technologies Group and general manager of commercial channels in Greater China, and Mr. Seijoong Oh, senior director of display products of Dell Technologies Group, attended the press conference and discussed topics such as modern office models and product innovation, and insights into global and Chinese display market trends. Share ideas. Mr. Wu Hailiang, global vice president of Dell Technologies Group and general manager of commercial channels in Greater China, said: "At the beginning of the new fiscal year, Dell
 Acer Shadow Knight Qing 6 laptop's new configuration first sold: i5-14450HX + 16G + 1T for 7,499 yuan
Jun 05, 2024 pm 02:34 PM
Acer Shadow Knight Qing 6 laptop's new configuration first sold: i5-14450HX + 16G + 1T for 7,499 yuan
Jun 05, 2024 pm 02:34 PM
This website reported on May 31 that Acer’s 2024 Shadow Knight Q6 notebook “i5-14450HX + 16GB RAM + 1TB storage space” version is now on sale on JD.com, with an initial price of 7,499 yuan. According to reports, this notebook is equipped with a 10-core 16-thread Intel Core i5-14450HX processor, equipped with an RTX4060 graphics card, built-in 16GB DDR5-5600MHz RAM and 1TB PCIe4.0 SSD, and adopts a "dual fans + five heat pipes + four air outlets" heat dissipation design. In addition, this website noticed that this notebook is equipped with a 2560x1600 resolution 165Hz panel, covering 100% sRGB color gamut, but the official brightness information of the notebook has not been announced. catch
 Acer releases new Predator Z57 monitor priced at about 18,000 yuan at CES: curved screen + MiniLED backlight unveiled
Jan 12, 2024 pm 11:45 PM
Acer releases new Predator Z57 monitor priced at about 18,000 yuan at CES: curved screen + MiniLED backlight unveiled
Jan 12, 2024 pm 11:45 PM
Acer released four new Predator series monitors at the CES show, including three models of different sizes and an eye-catching new product, the Predator Z57. The Predator Z57 monitor stands out with its unique curved screen design and excellent display performance. It uses a DUHDVA panel and combines it with MiniLED backlight technology, which contains up to 2304 partitions to provide users with an extraordinary visual experience. The monitor's screen resolution reaches an astonishing 7620x2160 and the refresh rate is as high as 120Hz, which can compete with Samsung's 57-inch Odyssey NeoG9 monitor on the market. This monitor will provide users with incredible visual effects and



