 Technology peripherals
Technology peripherals
 It Industry
It Industry
 AMD announces 'Sinkclose' high-severity vulnerability, affecting millions of Ryzen and EPYC processors
AMD announces 'Sinkclose' high-severity vulnerability, affecting millions of Ryzen and EPYC processors
AMD announces 'Sinkclose' high-severity vulnerability, affecting millions of Ryzen and EPYC processors
According to news from this site on August 10, AMD officially confirmed that there is a new vulnerability called "Sinkclose" in some EPYC and Ryzen processors, with the code "CVE-2023-31315", which may involve millions of AMD users around the world.
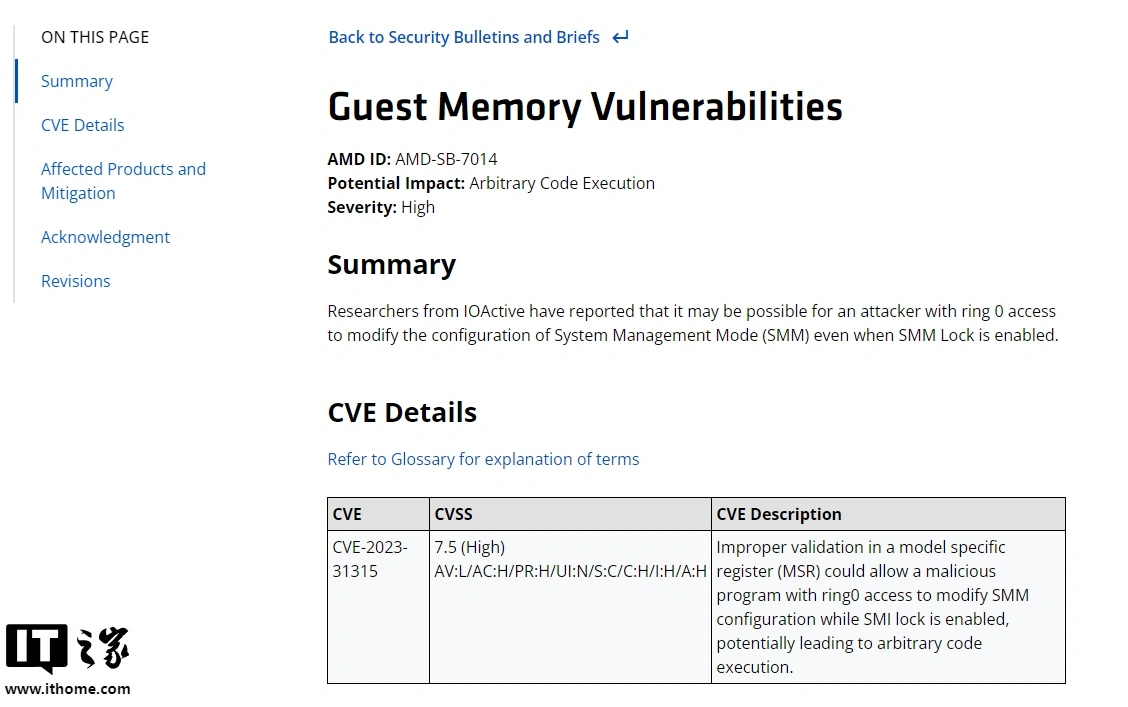
So, what is Sinkclose? According to a report by WIRED, the vulnerability allows intruders to run malicious code in "System Management Mode (SMM)." Intruders are said to be able to take control of each other's systems using a type of malware called a bootkit that cannot be detected by antivirus software.
Note from this site: System Management Mode (SMM) is a special CPU operating mode designed to achieve advanced power management and operating system independent functions. It can provide the same system management interrupt (SMI) handler in the traditional IA-32 architecture. The same execution environment can only be entered through the system management interrupt (SMI) and can only be exited by executing the RSM instruction.
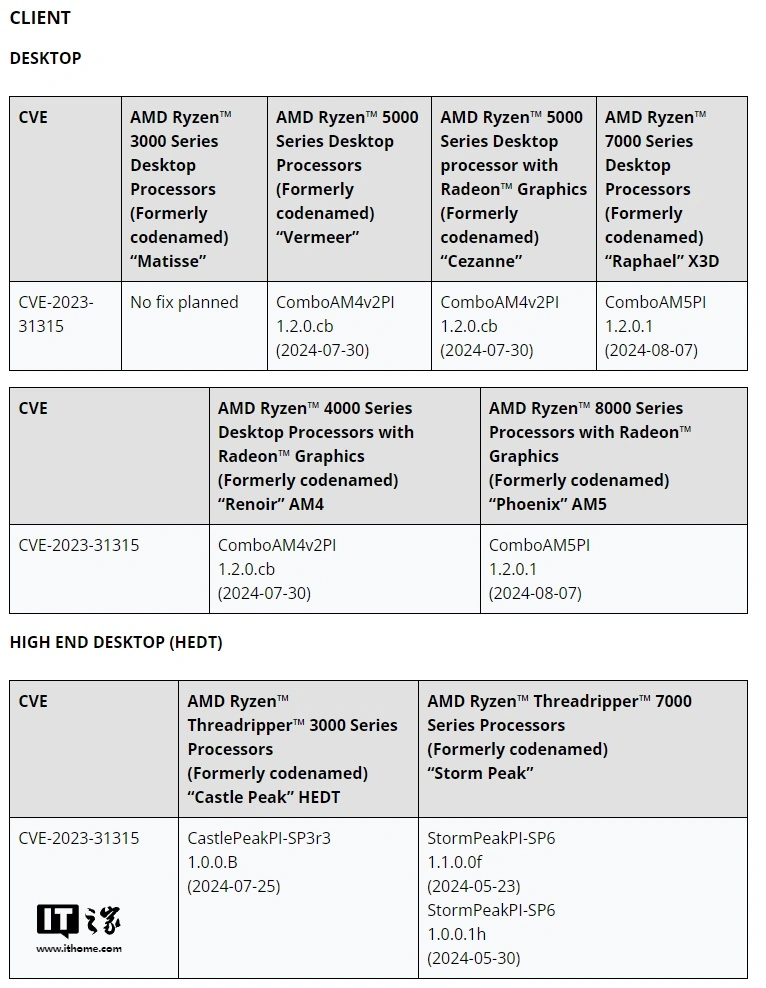
AMD security advisory shows that CPUs including Ryzen 3000 and first-generation EPYC and newer are affected. In this regard, AMD has provided a new version of firmware and microcode patches to alleviate the impact of "Sinkclose" on various generations of CPUs (but there is no repair plan for the Ryzen 3000 series desktop processors).
The above is the detailed content of AMD announces 'Sinkclose' high-severity vulnerability, affecting millions of Ryzen and EPYC processors. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 AMD Radeon RX 7800M in OneXGPU 2 outperforms Nvidia RTX 4070 Laptop GPU
Sep 09, 2024 am 06:35 AM
AMD Radeon RX 7800M in OneXGPU 2 outperforms Nvidia RTX 4070 Laptop GPU
Sep 09, 2024 am 06:35 AM
OneXGPU 2 is the first eGPUto feature the Radeon RX 7800M, a GPU that even AMD hasn't announced yet. As revealed by One-Netbook, the manufacturer of the external graphics card solution, the new AMD GPU is based on RDNA 3 architecture and has the Navi
 AMD Z2 Extreme chip for handheld consoles tipped for an early 2025 launch
Sep 07, 2024 am 06:38 AM
AMD Z2 Extreme chip for handheld consoles tipped for an early 2025 launch
Sep 07, 2024 am 06:38 AM
Even though AMD tailor-made the Ryzen Z1 Extreme (and its non-Extreme variant) for handheld consoles, the chip only ever found itself in two mainstream handhelds, the Asus ROG Ally (curr. $569 on Amazon) and Lenovo Legion Go (three if you count the R
 First Minisforum mini PC with Ryzen AI 9 HX 370 rumored to launch with high price tag
Sep 29, 2024 am 06:05 AM
First Minisforum mini PC with Ryzen AI 9 HX 370 rumored to launch with high price tag
Sep 29, 2024 am 06:05 AM
Aoostar was among the first to announce a Strix Point mini PC, and later, Beelink launched the SER9with a soaring starting price tag of $999. Minisforum joined the party by teasingthe EliteMini AI370, and as the name suggests, it will be the company'
 Deal | Lenovo ThinkPad P14s Gen 5 with 120Hz OLED, 64GB RAM and AMD Ryzen 7 Pro is 60% off right now
Sep 07, 2024 am 06:31 AM
Deal | Lenovo ThinkPad P14s Gen 5 with 120Hz OLED, 64GB RAM and AMD Ryzen 7 Pro is 60% off right now
Sep 07, 2024 am 06:31 AM
Many students are going back to school these days, and some may notice that their old laptop isn't up to the task anymore. Some college students might even be in the market for a high-end business notebook with a gorgeous OLED screen, in which case t
 Beelink SER9: Compact AMD Zen 5 mini-PC announced with Radeon 890M iGPU but limited eGPU options
Sep 12, 2024 pm 12:16 PM
Beelink SER9: Compact AMD Zen 5 mini-PC announced with Radeon 890M iGPU but limited eGPU options
Sep 12, 2024 pm 12:16 PM
Beelink continues to introduce new mini-PCs and accompanying accessories at a rate of knots. To recap, little over a month has passed since it released the EQi12, EQR6 and the EX eGPU dock. Now, the company has turned its attention to AMD's new Strix
 IFA 2024 | New Lenovo Yoga Pro 7 debuts with AMD Strix Point processor
Sep 06, 2024 am 06:42 AM
IFA 2024 | New Lenovo Yoga Pro 7 debuts with AMD Strix Point processor
Sep 06, 2024 am 06:42 AM
Asus had the first round of AMD Strix Point laptop launches, and now Lenovo has joined the party. Among the newly launched laptops is the Yoga Pro 7, which packs the Ryzen AI 9 365. Compared to the Hawk Point option launched earlier this year, the ne
 AMD AFMF 2 on Radeon 890M delivers up to 78% higher FPS
Sep 12, 2024 pm 12:16 PM
AMD AFMF 2 on Radeon 890M delivers up to 78% higher FPS
Sep 12, 2024 pm 12:16 PM
The technical preview of AMD Fluid Motion Frames 2 (AFMF 2) is now available for the latest Strix Point processors, and the company is promising up to 78% higher FPS with this frame-generation technology. It joins with Variable Graphics Memory (VGM),
 HP EliteBook X G1a: Powerful business laptop features Ryzen AI 300 with 40 W TDP & a big battery
Sep 25, 2024 am 06:18 AM
HP EliteBook X G1a: Powerful business laptop features Ryzen AI 300 with 40 W TDP & a big battery
Sep 25, 2024 am 06:18 AM
Of the two big American Windows PC manufacturers, HP has definitely been the one to embrace AMD more readily. Even so, the most expensive HP EliteBook, the EliteBook 1000, has always been exclusive to Intel. Until now, that is: The new HP EliteBook X





