
"You should program defensively, assuming that your class's clients will do their best to destroy its invariants"
Java as a safe language:
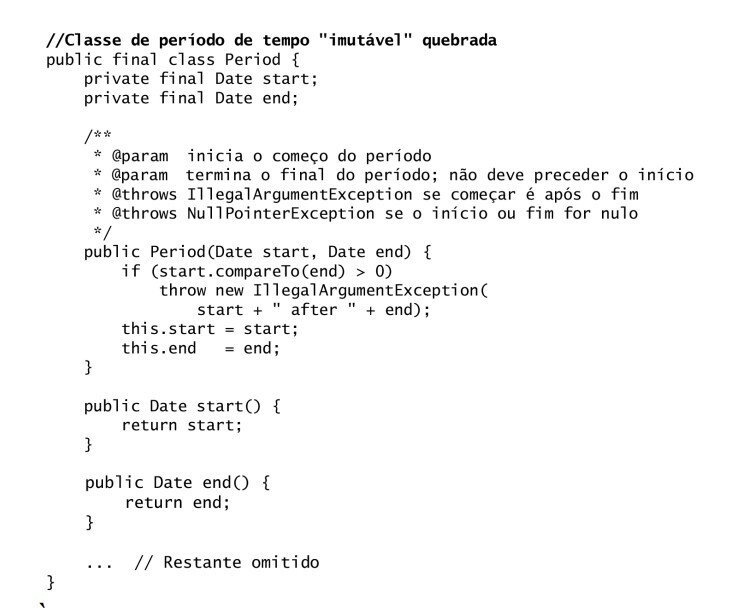
Immutable classes and security:
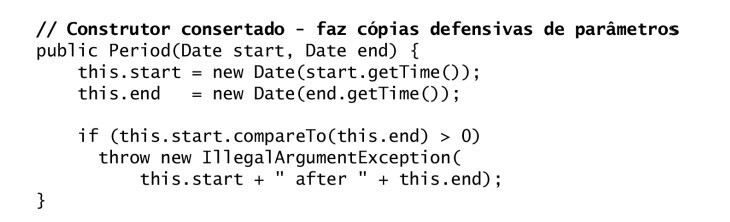
public Period(Date start, Date end) {
this.start = new Date(start.getTime()); // Cópia defensiva
this.end = new Date(end.getTime());
if (this.start.compareTo(this.end) > 0)
throw new IllegalArgumentException(start + " after " + end);
}
Defensive copies in builders:
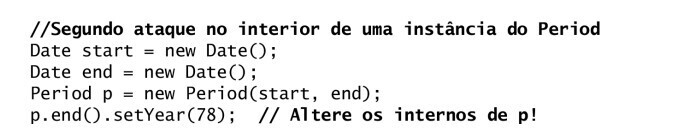
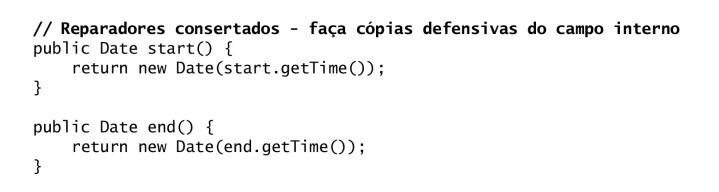
Getters and mutability:
public Date getStart() {
return new Date(start.getTime()); // Cópia defensiva
}
Application to mutable classes:
Return of internal components:
Use of immutable objects:
Costs and alternatives:
Conclusion:
Examples from the book:

The above is the detailed content of Item Make defensive copies when necessary. For more information, please follow other related articles on the PHP Chinese website!
 How to set both ends to be aligned in css
How to set both ends to be aligned in css
 How to create a blog
How to create a blog
 What versions of linux system are there?
What versions of linux system are there?
 Usage of console.log
Usage of console.log
 How to check dead links on your website
How to check dead links on your website
 vista key activation code
vista key activation code
 How to solve error1
How to solve error1
 special symbol point
special symbol point
 What is the difference between JD International self-operated and JD self-operated
What is the difference between JD International self-operated and JD self-operated




