 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Is mysql_real_escape_string a Reliable Defense Against SQL Injection?
Is mysql_real_escape_string a Reliable Defense Against SQL Injection?
Is mysql_real_escape_string a Reliable Defense Against SQL Injection?

Limitations of MySQLi's mysql_real_escape_string
mysql_real_escape_string is a function used in the MySQLi extension of PHP to prevent SQL injection attacks by escaping special characters in a string. While it can be an effective tool when used properly, there are several shortcomings that can lead to vulnerabilities in web applications:
Narrow Use Case:
The primary limitation of mysql_real_escape_string is its narrow use case. It is designed solely for escaping strings that are used as values within single-quoted strings in an SQL statement. Any other usage, such as escaping strings used in identifiers, functions, or other contexts, can lead to incorrect escaping and potential injection vulnerabilities.
Incorrect Usage:
mysql_real_escape_string should only be used to escape values that are enclosed in single quotes in an SQL statement. Common mistakes include using it to escape values used in numeric contexts (e.g., numeric column values or conditions), using it to escape identifiers or function names, or using it in concatenated queries. Incorrect usage can lead to unescaped values being inserted into the SQL statement, making the application vulnerable to injection attacks.
Limited Protection Against Numeric Values:
mysql_real_escape_string is designed to escape special characters in strings, but it does not provide protection against numeric values. If numeric values are user-supplied and not properly validated, they can be exploited to bypass the escaping mechanism and inject arbitrary SQL code. This can be particularly dangerous when numeric values are used in conditions or comparisons in the SQL statement.
Multibyte Character Encoding Issues:
Another limitation of mysql_real_escape_string is that it can be susceptible to multibyte character encoding issues. If the database connection encoding is set incorrectly, mysql_real_escape_string will use the wrong encoding for escaping strings, which can lead to improper escaping and injection vulnerabilities.
Alternatives to mysql_real_escape_string:
While mysql_real_escape_string can be a useful tool for escaping strings in certain scenarios, it is generally recommended to use prepared statements or parameterized queries instead. Prepared statements use placeholders to represent user-supplied values, which are then bound to the statement before execution. This approach eliminates the possibility of SQL injection by preventing unescaped values from being inserted into the SQL statement.
The above is the detailed content of Is mysql_real_escape_string a Reliable Defense Against SQL Injection?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
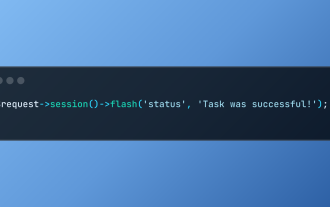 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP...
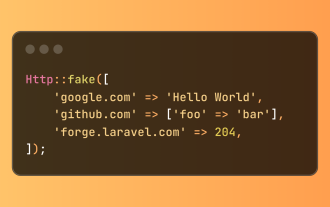 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
The article discusses adding custom functionality to frameworks, focusing on understanding architecture, identifying extension points, and best practices for integration and debugging.
 How to send a POST request containing JSON data using PHP's cURL library?
Apr 01, 2025 pm 03:12 PM
How to send a POST request containing JSON data using PHP's cURL library?
Apr 01, 2025 pm 03:12 PM
Sending JSON data using PHP's cURL library In PHP development, it is often necessary to interact with external APIs. One of the common ways is to use cURL library to send POST�...



