How Can You Secure Logins Without HTTPS?
Nov 04, 2024 pm 10:05 PM
Securing Logins Without HTTPS
Overview
Implementing HTTPS is crucial for securing web applications by encrypting communication between the client and server. However, in scenarios where HTTPS is unavailable, there may be a need to explore alternative methods for enhancing login security.
Tokenization and Password Encryption
Tokenization: Storing user credentials in hashed form using a unique token can provide some level of protection against replay attacks, where an attacker intercepts and reuses valid login sessions. However, this method has limitations as it does not prevent the interception of plaintext username and password during login.
Password Encryption: Encrypting passwords sent from HTML password fields can prevent simple sniffing attacks. However, this approach becomes vulnerable if an attacker gains access to the encrypted passwords, as they can potentially be decrypted and used to hijack user accounts.
Additional Considerations
Beyond these direct measures, there are several general best practices that contribute to login security:
- Enforcing strong password policies (e.g., minimum length, character complexity)
- Implementing session timeouts to prevent prolonged access in case of session compromise
- Using Captcha verification to mitigate brute-force attacks
- Regularly monitoring login activity for suspicious patterns
Limitations and Drawbacks
It is important to acknowledge that these methods alone cannot fully compensate for the absence of HTTPS. HTTPS provides comprehensive encryption, preventing attackers from eavesdropping on and manipulating login traffic. The aforementioned measures offer only partial protection and have their own limitations.
Conclusion
While tokenization, password encryption, and other practices can improve login security, they are no substitute for HTTPS. It is strongly recommended to prioritize HTTPS implementation for optimal protection against cyber threats.
The above is the detailed content of How Can You Secure Logins Without HTTPS?. For more information, please follow other related articles on the PHP Chinese website!

Hot Article

Hot tools Tags

Hot Article

Hot Article Tags

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)
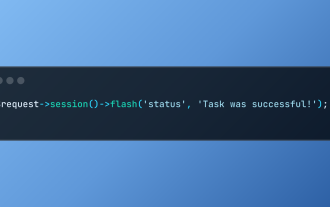 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
 Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, React
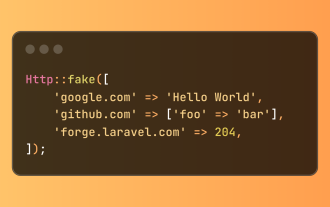 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
 Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation Survey








