Is Using `extract()` on Submission Data a Security Risk?
Nov 27, 2024 pm 08:20 PM
Potential Risks of Using extract() on Submission Data
The extract() function is commonly used in PHP to assign variables from an array to the current scope. However, when used on submission data (such as $_GET or $_POST) it can pose certain risks.
One significant issue with using extract() is its potential to introduce a confusing and harder-to-maintain codebase. By extracting variables from an array, it effectively pollutes the current scope, creating many variables that may not be immediately recognizable to other maintainers or future contributors. This can lead to difficulties in understanding the origins of these variables and their interactions with other parts of the code.
Furthermore, extracting variables from submission data without proper sanitation or validation can open doors to security vulnerabilities. If malicious input is passed into these variables, it can result in code execution or data manipulation vulnerabilities. To avoid such risks, the best practice is to manually iterate over the array and validate and sanitize each variable before using it. This provides more control over the data and reduces the chances of malicious code injection.
While extract() can be tempting for its convenience in handling arrays, it's important to weigh its risks against the alternatives. Manually iterating over arrays, while slightly more verbose, offers greater clarity and security, making it a more reliable approach.
The above is the detailed content of Is Using `extract()` on Submission Data a Security Risk?. For more information, please follow other related articles on the PHP Chinese website!

Hot Article

Hot tools Tags

Hot Article

Hot Article Tags

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)
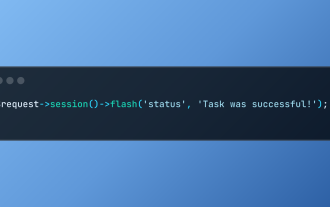 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
 Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, React
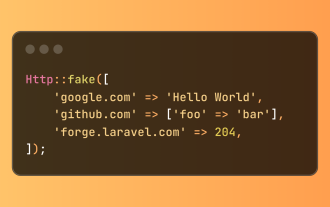 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
 Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation Survey








