 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 How Can We Securely Store and Retrieve User Passwords Using Two-Way Encryption?
How Can We Securely Store and Retrieve User Passwords Using Two-Way Encryption?
How Can We Securely Store and Retrieve User Passwords Using Two-Way Encryption?

Mitigating Risks in Two-Way Encryption: Storing Retrievable Passwords
Introduction
In this article, we explore the challenges of securely storing passwords that can be retrieved by users. We will discuss encryption algorithms, key management practices, and strategies to protect against data breaches.
Safeguarding Passwords with Encryption
Encryption plays a pivotal role in securing passwords. Selecting a robust encryption algorithm is crucial. While various ciphers exist, we recommend using either MCRYPT_BLOWFISH or MCRYPT_RIJNDAEL_128 for their exceptional strength and efficiency.
Implementing Strong Encryption
To ensure comprehensive encryption, we employ a customizable class that incorporates key stretching and conceals the initialization vector (IV). Additionally, it verifies the integrity and authenticity of encrypted data using HMAC.
Encryption Process
The user-supplied key is not directly utilized. Instead, it undergoes key stretching using PBKDF2. We strongly advise increasing the number of rounds when using passwords or non-random keys.
Data Integrity through MAC
We adopt the ENCRYPT-THEN-MAC (EtM) approach to assure the trustworthiness of encrypted data. The HMAC validation process guarantees that the integrity of the encrypted data has not been compromised.
Key Management Considerations
- Multiple Key Usage: Utilize three keys: one user-supplied, one application-specific, and one user-specific salt. Storing these keys separately minimizes the impact of any single key compromise.
- Trusted Users: If users can be trusted, consider requiring the user-supplied key every time a password needs to be decrypted.
Mitigating Data Theft
To protect against password theft, implement the following measures:
- Use SSL: Enforce SSL connections to protect data in transit.
- Protect Servers: Ensure servers are free from vulnerabilities such as SQL injection and CSRF.
- Beware of Attacks: Be vigilant against replay and MITM attacks, as they can grant access to encryption keys.
Conclusion
By combining strong encryption algorithms, prudent key management strategies, and robust security practices, we can effectively store passwords that users can retrieve while safeguarding them from potential threats.
The above is the detailed content of How Can We Securely Store and Retrieve User Passwords Using Two-Way Encryption?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
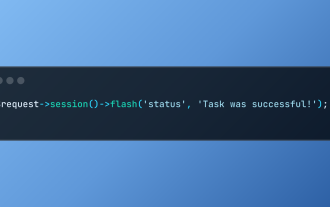 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP...
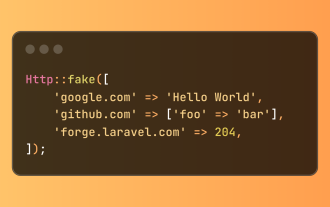 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 Framework Security Features: Protecting against vulnerabilities.
Mar 28, 2025 pm 05:11 PM
Framework Security Features: Protecting against vulnerabilities.
Mar 28, 2025 pm 05:11 PM
Article discusses essential security features in frameworks to protect against vulnerabilities, including input validation, authentication, and regular updates.
 Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
JWT is an open standard based on JSON, used to securely transmit information between parties, mainly for identity authentication and information exchange. 1. JWT consists of three parts: Header, Payload and Signature. 2. The working principle of JWT includes three steps: generating JWT, verifying JWT and parsing Payload. 3. When using JWT for authentication in PHP, JWT can be generated and verified, and user role and permission information can be included in advanced usage. 4. Common errors include signature verification failure, token expiration, and payload oversized. Debugging skills include using debugging tools and logging. 5. Performance optimization and best practices include using appropriate signature algorithms, setting validity periods reasonably,



