AWS Transfer Family with Golang for File Transfers
In the world of modern technology, secure and efficient file transfer is a critical necessity for many organizations. AWS Transfer Family, a managed secure file transfer solution offered by Amazon Web Services, allows file transfers using standard protocols such as SFTP, FTPS, FTP and AS2. When combined with Golang, a programming language known for its efficiency and ease of use, a powerful combination is created to manage and automate file transfers effectively.
In this article, we will explore how to integrate AWS Transfer Family with Golang to optimize your file transfer processes. From configuring AWS Transfer Family to implementing an SFTP client with Golang, I will guide you step by step so you can make the most of these technologies.
What is AWS Transfer Family?
AWS Transfer Family is a secure, fully managed service that allows for the transfer of files into and out of AWS storage services such as Amazon S3 and Amazon EFS using protocols like SFTP, AS2, FTPS, and FTP.
Key Features
- Protocols Supported: SFTP, FTPS, FTP, AS2
- AWS Storage Integrations: Amazon S3, Amazon EFS
- Use Cases: Data lakes, internal transfers, data distribution, compliance workflows, supply chain logistics, B2B transactions.
Benefits
- Real-time scalability.
- No need for infrastructure management.
- Leverage native AWS services for data processing and analytics.
- Fully managed, serverless workflow service.
- Pay-as-you-go pricing.
Prerequisites
- AWS Account: An active Amazon Web Services account. If you don’t have one yet, you can sign up on the AWS website.
- Golang: Knowledge of the Go (Golang) programming language.
- Administrative Privileges in AWS.
- AWS Transfer Family: Administrative read and write permissions to configure and manage AWS Transfer Family. This includes the ability to create and manage transfer servers. Note that this service has an associated cost.
- Amazon S3: Administrative permissions to read and write to Amazon S3 buckets.
- AWS IAM: Permissions to manage IAM roles and policies necessary for the integration and security of transfers.
Architectural Design
The proposed architectural design for integrating AWS Transfer Family with Golang consists of the following components, as illustrated in the diagram below:
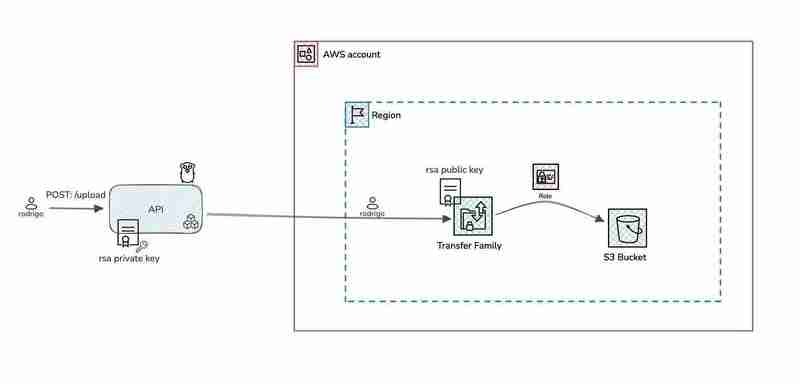
The API proposed in this article serves as a basic example to demonstrate its fundamental functionality. In a real-world scenario, the API can be more complex and include additional features. Its primary function is to upload files to the AWS Transfer Family SFTP server and store them in an S3 bucket, whether for backup purposes or integration with other systems. Use cases vary and depend on the needs of each organization. Here are some additional use case examples: AWS Transfer Family Customers.
Furthermore, the API proposed in this article can be deployed to the AWS cloud using services such as AWS Elastic Beanstalk or AWS Fargate to achieve greater scalability and availability, depending on the specific requirements of each organization.
Let’s get started!
Implementation
Generate public and private key
Generate a public and private key pair for connecting to the AWS Transfer Family SFTP server. This can be done locally on our machine using the following command.
$ ssh-keygen -t rsa -b 4096 -f
- aws_example_ssh_key: Key name
- PATH: Directory where the key will be saved
- rsa: Encryption algorithm
- 4096: Key size
- f: Output file name
ssh-keygen -t rsa -b 4096 -f <PATH>/aws_example_ssh_key Generating public/private rsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in <PATH>/aws_example_ssh_key Your public key has been saved in <PATH>/aws_example_ssh_key.pub The key fingerprint is: SHA256:P80TXbp10tjdzJLc3KAhtWP9YWQe+A181WvqUQyaTFc rodrigoquispe@0WJMD6M The key's randomart image is: +---[RSA 4096]----+ | ..oE+| | o ** +| | + O **+| | * *.^*| | S o % #| | . o + =.| | o = o | | . o | | | +----[SHA256]-----+
- Enter passphrase (empty for no passphrase): Password for the key.
- Enter same passphrase again: Confirm password for the key.
- Your identification has been saved in
/aws_example_ssh_key: The private key will be saved in the aws_example_ssh_key file in the specified path. - Your public key has been saved in
/aws_example_ssh_key.pub: The public key will be saved in the aws_example_ssh_key.pub file in the specified path.

Create Transfer Family Service
Log in to the AWS Management Console and select the AWS Transfer Family service and create server.

Select the SFTP (SSH File Transfer Protocol) for secure file transfer and click Next.

Choose an identity provider and select "Service managed."

In the endpoint configuration, select "Publicly accessible" and click Next.

We select "Amazon S3" as the storage option and click Next.

In the "Configure additional details" section, leave the settings at their default values.




Review, click Next and create.
Once the creation is complete, we will have something similar to this. We can see that we do not have any users yet and that it will be starting shortly through a public endpoint and using S3 as storage.

Create a role
Create a new role for the AWS transfer family to s3 service. To do this, go to the IAM service and create new role of the AWS service type and in the use case select transfer and next.

Permission policy, AmazonS3FullAccess to have full access to S3 bucket. But this policy is very permissible and it is not recommended to use it in production. And next.

We proceed to assign the name of the role "role-example-transfer-to-s3", we review and click "Create role".

Create S3 bucket
We proceed to create the s3 bucket, to do this we go to the s3 service and create a new bucket.

We set the name of the bucket, leaving the default configuration and create bucket.
Bucket name: "bucket-example-transfer".


At the end of the creación we will have something like this:

Configure SFTP users for Transfer Family with S3
Go to the AWS Transfer Family service and select the server you created earlier.
- Select the "Users" tab and click on "Add user".
- Enter the username.
- Assign the IAM role you created earlier.
- Set "Policy" none
- In the "Home directory" field, enter bucket-example-transfer, which is the name of the S3 bucket you created previously.
- Click on "Add user".

To follow this article, you will need to provide the public key that was generated at the start aws_example_ssh_key.pub.
To view the content of the public key, use the following command:
$ cat aws_example_ssh_key.pub
The public key looks like this:
ssh-keygen -t rsa -b 4096 -f <PATH>/aws_example_ssh_key Generating public/private rsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in <PATH>/aws_example_ssh_key Your public key has been saved in <PATH>/aws_example_ssh_key.pub The key fingerprint is: SHA256:P80TXbp10tjdzJLc3KAhtWP9YWQe+A181WvqUQyaTFc rodrigoquispe@0WJMD6M The key's randomart image is: +---[RSA 4096]----+ | ..oE+| | o ** +| | + O **+| | * *.^*| | S o % #| | . o + =.| | o = o | | . o | | | +----[SHA256]-----+
This is the key that we need to include in the "SSH Public Keys" field. Ensure that you copy and paste the entire key accurately into this field to enable secure access to the server.

After creating the user, you should see a confirmation screen similar to the one below. This indicates that the user has been successfully set up and is ready to use the SFTP service.

Project structure
Below, we provide a detailed overview of the Golang project structure and include a link to the GitHub repository for reference. This overview will help you understand the organization of the project and how various components are structured and interconnected.
ssh-rsa AAAAB3NzaC1yc2EBBAADAQABAAACAQC/qNMJaCz8+I3G71bTFf8Cpe+AAAA0BBBBBBBA6C+/a8fyl9Dw4wjj0huc4ItlX2auKG3skxTYP1ZgO5/7M7xmp2Hf+AAAA0BBBBBBBA6CynWwfwkS5XEIfNtoNWCSeB6ra4anljFdLJH4ZReOM18xxBZCyz2gGA7ePprM0nfpgoQKjp8eDoz6HFcvH4Qynea06W72D+tUWjCRH6bgPBsw/cCfj+VrcqsQXif/X8nViS679+V+AAAA0BBBBBBBA6C+t/5dD3uFPyc8yJn2fNEHB4kfIB9JR5fPIo4dVqPebloPg9vKT2M+AAAA0BBBBBBBA6C/AAAA0BBBBBBBA6C+XLTJSAljgq9JQ4l3vnT4RSsKuK+DX2um5DsN/Zwk9Qwf8JRJey/AAAA0BBBBBBBA6C+/AAAA0BBBBBBBA6CNkVaeDOYSIeGkMBUmmMaeVNeaR967SBLoHNzBfodKKaIpsmW2yHvIitg/YKu2YXKe/DnYU3G8om13uL8qIOB85CugVQ== rodrigoquispe@AAAA0BBBBBBBA6C
The dependencies we will be using are Gin and SFTP.
├── cmd
│ └── main.go
├── go.mod
├── go.sum
└── internal
├── app
│ └── service.go
├── domain
│ └── models.go
├── handler
│ └── sftp_handler.go
└── infra
├── config.go
└── sftp_client.go
Set the following credentials in the config.go file, where the private key and Transfer Family user credentials are located, to connect to the SFTP server.
$ go get -u github.com/gin-gonic/gin $ go get -u github.com/pkg/sftp
- Host: The connection endpoint we obtained earlier.
- Port: 22
- User: The username we created earlier.
- PrivateKeyPath: The path to the private key we created earlier.
Also, consider setting the path where the files uploaded to the SFTP server will be saved. In my case, it’s /bucket-example-transfer/rodrigo.
// config.go
func LoadConfig() *Config {
return &Config{
Host: "<HOST>.server.transfer.us-east-1.amazonaws.com",
Port: "<PORT>",
User: "<USER>",
PrivateKeyPath: "<PATH>/aws_example_ssh_key",
}
}
Function to create a new SFTP client with the given configuration:
// service.go
func (u *Service) Upload(file *domain.File) error {
return u.sftpClient.UploadFile(file, "/bucket-example-transfer/rodrigo/")
}
Method to upload a file to the SFTP server.
ssh-keygen -t rsa -b 4096 -f <PATH>/aws_example_ssh_key Generating public/private rsa key pair. Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in <PATH>/aws_example_ssh_key Your public key has been saved in <PATH>/aws_example_ssh_key.pub The key fingerprint is: SHA256:P80TXbp10tjdzJLc3KAhtWP9YWQe+A181WvqUQyaTFc rodrigoquispe@0WJMD6M The key's randomart image is: +---[RSA 4096]----+ | ..oE+| | o ** +| | + O **+| | * *.^*| | S o % #| | . o + =.| | o = o | | . o | | | +----[SHA256]-----+
Run the project using the following command:
$ go run cmd/main.go

Now, we upload a file to the SFTP server using Postman. Then, we navigate to S3 to verify that the file has been uploaded correctly.


The files were successfully uploaded without any issues.
Thank you for reading.
The above is the detailed content of AWS Transfer Family with Golang for File Transfers. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1317
1317
 25
25
 1268
1268
 29
29
 1246
1246
 24
24
 Golang vs. Python: Performance and Scalability
Apr 19, 2025 am 12:18 AM
Golang vs. Python: Performance and Scalability
Apr 19, 2025 am 12:18 AM
Golang is better than Python in terms of performance and scalability. 1) Golang's compilation-type characteristics and efficient concurrency model make it perform well in high concurrency scenarios. 2) Python, as an interpreted language, executes slowly, but can optimize performance through tools such as Cython.
 Golang and C : Concurrency vs. Raw Speed
Apr 21, 2025 am 12:16 AM
Golang and C : Concurrency vs. Raw Speed
Apr 21, 2025 am 12:16 AM
Golang is better than C in concurrency, while C is better than Golang in raw speed. 1) Golang achieves efficient concurrency through goroutine and channel, which is suitable for handling a large number of concurrent tasks. 2)C Through compiler optimization and standard library, it provides high performance close to hardware, suitable for applications that require extreme optimization.
 Golang's Impact: Speed, Efficiency, and Simplicity
Apr 14, 2025 am 12:11 AM
Golang's Impact: Speed, Efficiency, and Simplicity
Apr 14, 2025 am 12:11 AM
Goimpactsdevelopmentpositivelythroughspeed,efficiency,andsimplicity.1)Speed:Gocompilesquicklyandrunsefficiently,idealforlargeprojects.2)Efficiency:Itscomprehensivestandardlibraryreducesexternaldependencies,enhancingdevelopmentefficiency.3)Simplicity:
 Golang vs. Python: Key Differences and Similarities
Apr 17, 2025 am 12:15 AM
Golang vs. Python: Key Differences and Similarities
Apr 17, 2025 am 12:15 AM
Golang and Python each have their own advantages: Golang is suitable for high performance and concurrent programming, while Python is suitable for data science and web development. Golang is known for its concurrency model and efficient performance, while Python is known for its concise syntax and rich library ecosystem.
 Golang vs. C : Performance and Speed Comparison
Apr 21, 2025 am 12:13 AM
Golang vs. C : Performance and Speed Comparison
Apr 21, 2025 am 12:13 AM
Golang is suitable for rapid development and concurrent scenarios, and C is suitable for scenarios where extreme performance and low-level control are required. 1) Golang improves performance through garbage collection and concurrency mechanisms, and is suitable for high-concurrency Web service development. 2) C achieves the ultimate performance through manual memory management and compiler optimization, and is suitable for embedded system development.
 Golang and C : The Trade-offs in Performance
Apr 17, 2025 am 12:18 AM
Golang and C : The Trade-offs in Performance
Apr 17, 2025 am 12:18 AM
The performance differences between Golang and C are mainly reflected in memory management, compilation optimization and runtime efficiency. 1) Golang's garbage collection mechanism is convenient but may affect performance, 2) C's manual memory management and compiler optimization are more efficient in recursive computing.
 C and Golang: When Performance is Crucial
Apr 13, 2025 am 12:11 AM
C and Golang: When Performance is Crucial
Apr 13, 2025 am 12:11 AM
C is more suitable for scenarios where direct control of hardware resources and high performance optimization is required, while Golang is more suitable for scenarios where rapid development and high concurrency processing are required. 1.C's advantage lies in its close to hardware characteristics and high optimization capabilities, which are suitable for high-performance needs such as game development. 2.Golang's advantage lies in its concise syntax and natural concurrency support, which is suitable for high concurrency service development.
 The Performance Race: Golang vs. C
Apr 16, 2025 am 12:07 AM
The Performance Race: Golang vs. C
Apr 16, 2025 am 12:07 AM
Golang and C each have their own advantages in performance competitions: 1) Golang is suitable for high concurrency and rapid development, and 2) C provides higher performance and fine-grained control. The selection should be based on project requirements and team technology stack.




