Zero-time Technology Security Team Analysis: Four.meme platform Memecoin was attacked and lost about US$15,000
Binance Academy's incubated memecoin launch platform Four.meme encountered a security incident, and its memecoin project Snowboard (contract address: 0x4abfd9a204344bd81a276c075ef89412c9fd2f64) was attacked and lost about $15,000. Attack transaction hash: 0x2902f93a0e0e32893b6d5c907ee7bb5dabc459093efa6dbc6e6ba49f85c27f61.
Platform mechanism and vulnerability analysis
Four.meme is similar to Pump.Fun. It is a memecoin launch platform running on BNB Smart Chain. Its operating process is roughly divided into three stages:
Attack method
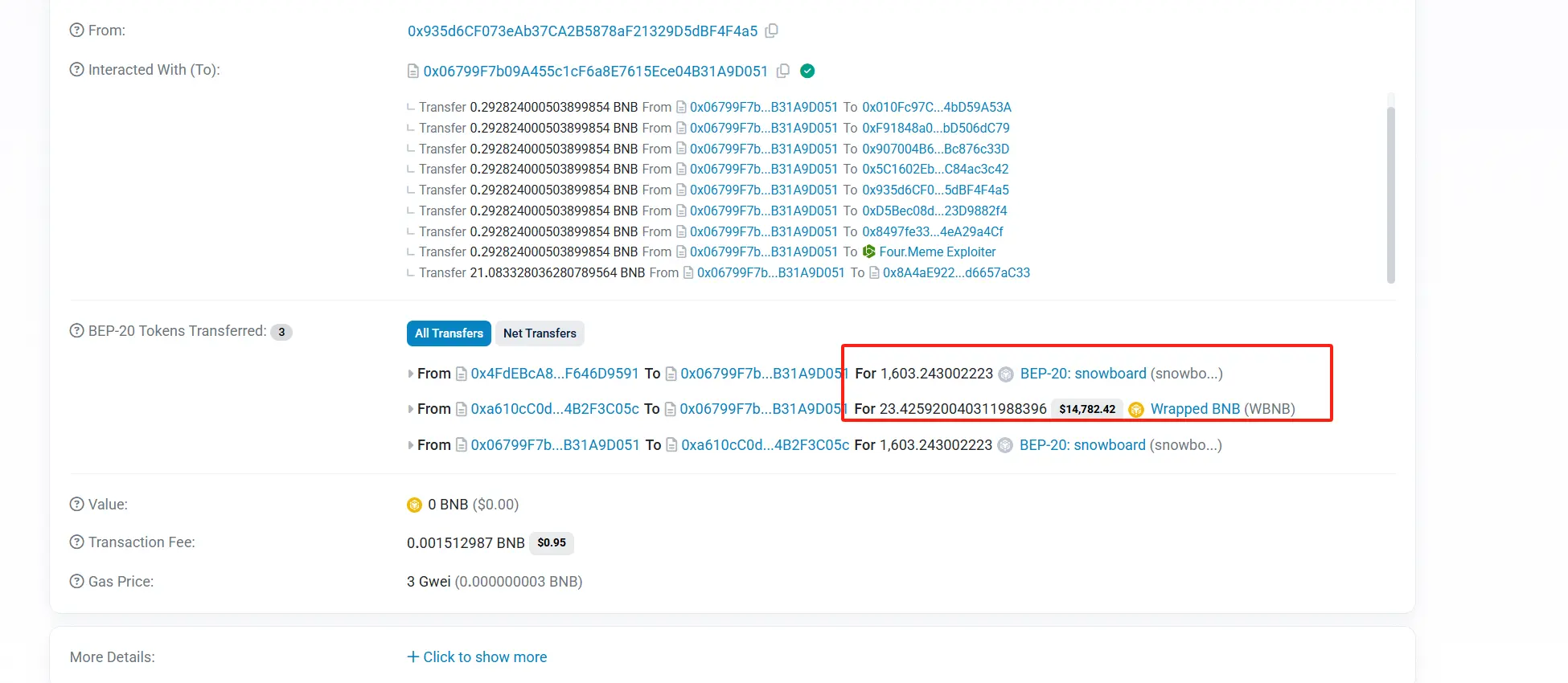
The attacker exploited the vulnerability of Four.meme when migrating memecoin to DEX. The attacker created and initialized a pair on PancakeSwap in advance as Snowboard, but set the sqrtPriceX96 parameter to an exceptionally high value (368058418256012 times higher than the normal value).
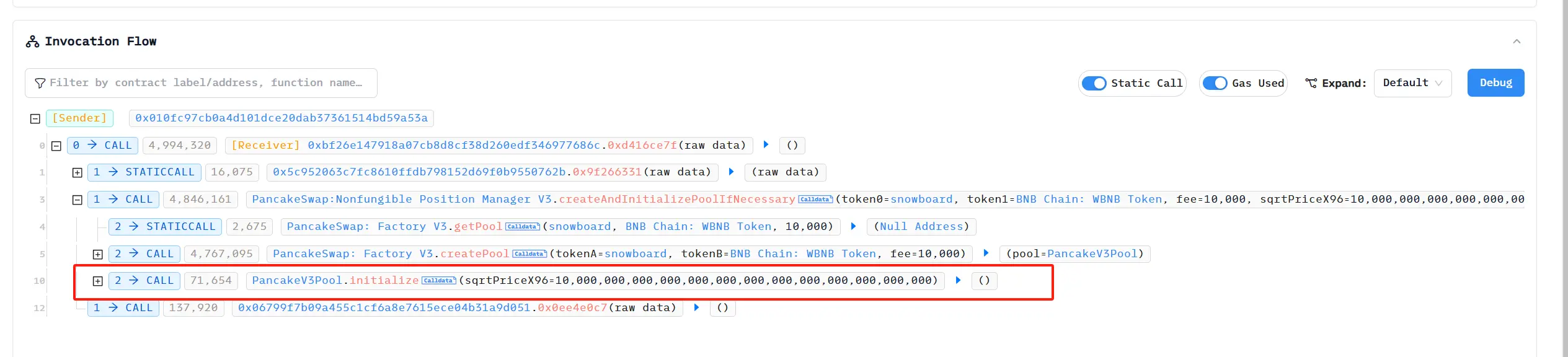
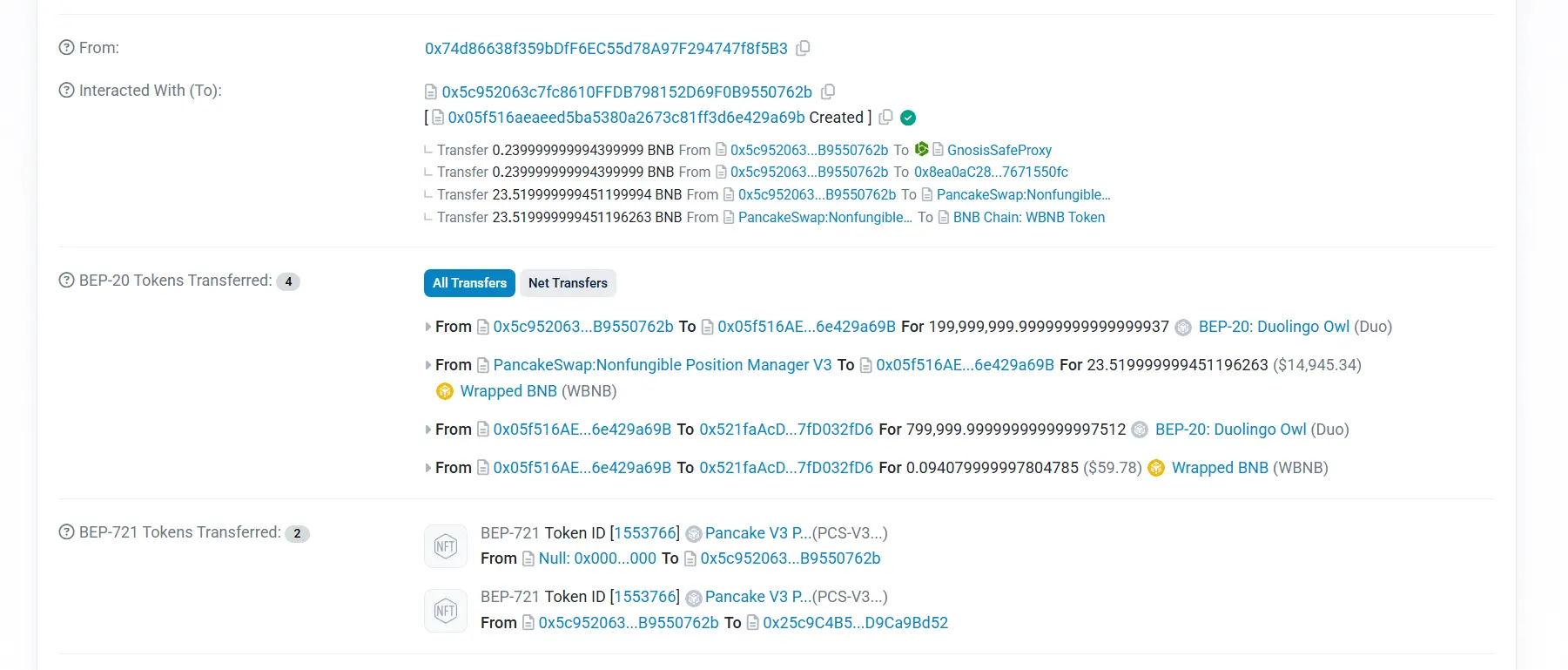
When the Four.meme contract calls the createAndInitializePoolIfNecessary function to create a trading pair, since the trading pair already exists, the contract adds liquidity using the attacker's preset exception price. This has resulted in the Snowboard price being artificially manipulated to extremely high levels. The attacker then redeems most of the BNBs in the pool using a small number of Snowboard tokens to complete the attack.
Safety advice
This attack exposed the logic of the Four.meme contract in handling DEX transaction pair creation. It is recommended that project parties conduct more rigorous testing and audits when designing economic models and contract codes, and consider a variety of abnormal situations to avoid the occurrence of similar vulnerabilities. Multiple rounds of audits, especially cross-audits by multiple audit companies, are crucial to ensuring the safety of the platform.
The above is the detailed content of Four.meme attack event analysis. For more information, please follow other related articles on the PHP Chinese website!




