Setting up a Multi-Server Security Engine Installation
This guide demonstrates how to configure a multi-server CrowdSec Security Engine, enhancing your network's collective security. One server acts as the parent (server-1), receiving alerts from child Log Processors (server-2 and server-3). This architecture allows for distributed threat detection and remediation.

Server-1, the parent, hosts the HTTP REST API (LAPI) and manages signal storage and distribution. Server-2 and server-3, the children, are internet-facing, forwarding alerts to server-1. Remediation, managed by Remediation Components, is independent of detection and relies on server-1's LAPI. Child Log Processors have their LAPI disabled to conserve resources.
Key Considerations:
- A PostgreSQL backend is recommended for server-1's LAPI for enhanced stability (though SQLite with WAL is a viable alternative).
- Requires three Ubuntu 22.04 servers: one parent and two children, connected via a local network.
Setup Steps:
1. Parent LAPI Server (server-1):
-
Install CrowdSec: Follow the installation guide and use the provided commands:
curl -s https:/packagecloud.io/install/repositories/crowdsec/crowdsec/script.deb.sh | sudo bash sudo apt install crowdsec
Copy after login -
(Optional) PostgreSQL Setup: If using PostgreSQL, install it (
sudo apt install postgresql), create thecrowdsecdatabase and user, grant privileges, and update/etc/crowdsec/config.yaml'sdb_configsection accordingly. Regenerate credentials and restart CrowdSec.sudo -i -u postgres psql # ... PostgreSQL commands ... sudo cscli machines add -a –force sudo systemctl restart crowdsec
Copy after login -
Expose LAPI Port: Modify
/etc/crowdsec/config.yamlto expose the LAPI port (e.g.,10.0.0.1:8080).api: server: listen_uri: 10.0.0.1:8080Copy after login
2. Child Log Processors (server-2 & server-3):
-
Install CrowdSec: Use the same installation commands as server-1.
-
Register with LAPI: Register each child with server-1's LAPI:
sudo cscli lapi register -u http://10.0.0.1:8080
Copy after login -
Disable Child LAPI: Disable the local API in
/etc/crowdsec/config.yaml:api: server: enable: falseCopy after login -
Validate Registration: On server-1, validate each child using
cscli machines listandcscli machines validate <machine_id></machine_id>. -
Restart CrowdSec: Restart CrowdSec on each child.
3. Remediation (server-2 & server-3):
-
Generate API Key: On server-1, generate an API key for each child using
cscli bouncers add <bouncer_name></bouncer_name>. -
Install Remediation Component: Install the
cs-firewall-bouncer-iptablescomponent. -
Configure Remediation Component: Configure
/etc/crowdsec/bouncers/crowdsec-firewall-bouncer.yamlwith the API URL and key. -
Restart Remediation Component: Restart the
crowdsec-firewall-bouncerservice.
Important Notes:
- Communication between servers is currently unencrypted HTTP (consider HTTPS for production).
- This setup lacks monitoring and alerting (refer to CrowdSec documentation for details).
- Server-1 is a single point of failure.
This enhanced setup provides a more robust and scalable security posture. Future articles will cover high-availability configurations. Engage with the CrowdSec community for support and feedback.
The above is the detailed content of Setting up a Multi-Server Security Engine Installation. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1382
1382
 52
52
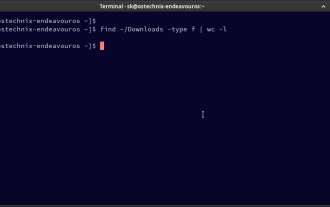 How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
Efficiently Counting Files and Folders in Linux: A Comprehensive Guide Knowing how to quickly count files and directories in Linux is crucial for system administrators and anyone managing large datasets. This guide demonstrates using simple command-l
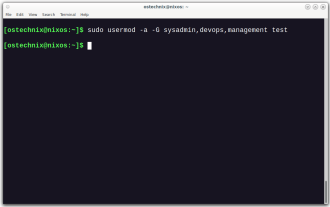 How To Add A User To Multiple Groups In Linux
Mar 18, 2025 am 11:44 AM
How To Add A User To Multiple Groups In Linux
Mar 18, 2025 am 11:44 AM
Efficiently managing user accounts and group memberships is crucial for Linux/Unix system administration. This ensures proper resource and data access control. This tutorial details how to add a user to multiple groups in Linux and Unix systems. We
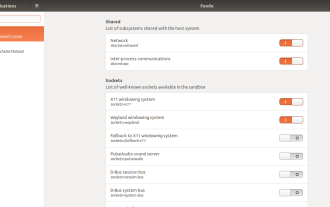 How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
Flatpak application permission management tool: Flatseal User Guide Flatpak is a tool designed to simplify Linux software distribution and use. It safely encapsulates applications in a virtual sandbox, allowing users to run applications without root permissions without affecting system security. Because Flatpak applications are located in this sandbox environment, they must request permissions to access other parts of the operating system, hardware devices (such as Bluetooth, network, etc.) and sockets (such as pulseaudio, ssh-auth, cups, etc.). This guide will guide you on how to easily configure Flatpak with Flatseal on Linux
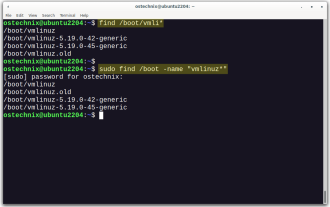 How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
Linux Kernel is the core component of a GNU/Linux operating system. Developed by Linus Torvalds in 1991, it is a free, open-source, monolithic, modular, and multitasking Unix-like kernel. In Linux, it is possible to install multiple kernels on a sing
 How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
This brief guide explains how to type Indian Rupee symbol in Linux operating systems. The other day, I wanted to type "Indian Rupee Symbol (₹)" in a word document. My keyboard has a rupee symbol on it, but I don't know how to type it. After
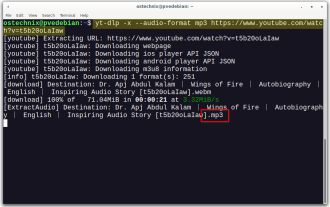 Yt-dlp Commands: The Complete Tutorial For Beginners (2025)
Mar 21, 2025 am 11:00 AM
Yt-dlp Commands: The Complete Tutorial For Beginners (2025)
Mar 21, 2025 am 11:00 AM
Have you ever wanted to save your favorite videos from the internet? Whether it's a funny cat video or a tutorial you want to watch later, Yt-dlp is here to help! In this comprehensive yt-dlp tutorial, we will explain what yt-dlp is, how to install i
 What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
Linux is best used as server management, embedded systems and desktop environments. 1) In server management, Linux is used to host websites, databases, and applications, providing stability and reliability. 2) In embedded systems, Linux is widely used in smart home and automotive electronic systems because of its flexibility and stability. 3) In the desktop environment, Linux provides rich applications and efficient performance.
 LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
If you're familiar with AirDrop, you know it's a popular feature developed by Apple Inc. that enables seamless file transfer between supported Macintosh computers and iOS devices using Wi-Fi and Bluetooth. However, if you're using Linux and missing o




