Mastering User and Permission Management: Fortifying Your Linux Bastion

Linux system security: Detailed explanation of user account and permission management
Linux is known for its flexibility and security. The core of its powerful security model lies in the meticulous management of user accounts and permissions. This article explores the details of user account and permission management in Linux, clarifying how to protect the system from unauthorized access and potential misuse.
User and group understanding
The core of Linux security model is users and groups. Users are accounts with system access rights and their permission levels may vary. Groups are collections of users, which facilitate the management of public permissions of multiple users.
- User ID and Group ID (UID & GID): Each Linux user and group is identified by a unique user ID (UID) and group ID (GID) respectively. These identifiers are critical to system management permissions and resources.
Creation and management of user accounts
Creating, modifying and deleting user accounts is the daily work of a system administrator.
- Create a user account: Use the
useraddcommand to create a new user account. For example,useradd usernamecreates a new user named "username". - Modify user account: Use the
usermodcommand to modify an existing user account, such as changing the user's home directory. - Delete user account: Use the
userdelcommand to delete the user account. - Administrative password: The
passwdcommand is used to manage passwords, allowing passwords to be set, updated, and deleted. - Configure user properties: View
/etc/passwdand/etc/shadowfiles to understand and configure user properties.
Group creation and management
- Create a group: The
groupaddcommand is used to create a new group. - Modify Group: Use the
groupmodcommand to modify the details of an existing group. - Delete Group: The
groupdelcommand is used to delete groups from the system. - Edit group configuration: The
vigrcommand is used to edit group configuration, and the/etc/groupfile saves group information.
Understanding of file permissions and ownership
- File Permissions: Linux files have permissions that determine who can read, write, or execute them. Permissions are divided into three types: read, write and execute.
- Modify permissions: The
chmodcommand is used to modify file permissions. - Change ownership: Use
chownandchgrpcommands to change the file ownership and group respectively.
Advanced permission management
- Special permissions: Deeply understand special permissions such as setuid, setgid and sticky bits to enhance security management.
- Access Control Lists (ACLs): Understand how ACLs implement fine-grained permission control over Linux systems.
Automated account management
- Automation with Ansible: Explore how tools like Ansible can significantly simplify management of accounts and permissions.
- Demo: A basic demonstration of using Ansible for automated account and permission management tasks.
Monitor and audit user activities
- The importance of auditing: Understand the importance of monitoring and auditing in maintaining a secure and reliable Linux system.
- Audit tools: Explore tools such as auditd and syslog configurations to effectively audit user activities.
in conclusion
Mastering user account and permission management is the key to strengthening the security of Linux system. This article covers key points of managing user accounts, groups, file permissions, etc. By following recommended best practices and staying alert to management mechanisms, you can build a safer and more reliable Linux system.
The above is the detailed content of Mastering User and Permission Management: Fortifying Your Linux Bastion. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1380
1380
 52
52
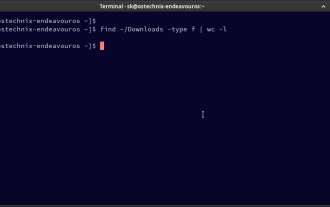 How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
Efficiently Counting Files and Folders in Linux: A Comprehensive Guide Knowing how to quickly count files and directories in Linux is crucial for system administrators and anyone managing large datasets. This guide demonstrates using simple command-l
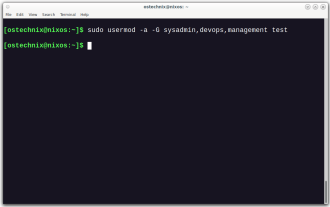 How To Add A User To Multiple Groups In Linux
Mar 18, 2025 am 11:44 AM
How To Add A User To Multiple Groups In Linux
Mar 18, 2025 am 11:44 AM
Efficiently managing user accounts and group memberships is crucial for Linux/Unix system administration. This ensures proper resource and data access control. This tutorial details how to add a user to multiple groups in Linux and Unix systems. We
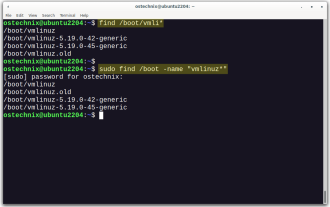 How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
Linux Kernel is the core component of a GNU/Linux operating system. Developed by Linus Torvalds in 1991, it is a free, open-source, monolithic, modular, and multitasking Unix-like kernel. In Linux, it is possible to install multiple kernels on a sing
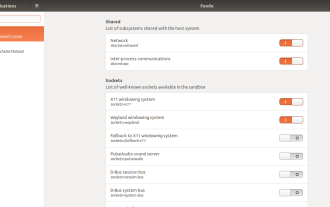 How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
Flatpak application permission management tool: Flatseal User Guide Flatpak is a tool designed to simplify Linux software distribution and use. It safely encapsulates applications in a virtual sandbox, allowing users to run applications without root permissions without affecting system security. Because Flatpak applications are located in this sandbox environment, they must request permissions to access other parts of the operating system, hardware devices (such as Bluetooth, network, etc.) and sockets (such as pulseaudio, ssh-auth, cups, etc.). This guide will guide you on how to easily configure Flatpak with Flatseal on Linux
 How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
This brief guide explains how to type Indian Rupee symbol in Linux operating systems. The other day, I wanted to type "Indian Rupee Symbol (₹)" in a word document. My keyboard has a rupee symbol on it, but I don't know how to type it. After
 What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
Linux is best used as server management, embedded systems and desktop environments. 1) In server management, Linux is used to host websites, databases, and applications, providing stability and reliability. 2) In embedded systems, Linux is widely used in smart home and automotive electronic systems because of its flexibility and stability. 3) In the desktop environment, Linux provides rich applications and efficient performance.
 Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linus Torvalds has released Linux Kernel 6.14 Release Candidate 6 (RC6), reporting no significant issues and keeping the release on track. The most notable change in this update addresses an AMD microcode signing issue, while the rest of the updates
 LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
If you're familiar with AirDrop, you know it's a popular feature developed by Apple Inc. that enables seamless file transfer between supported Macintosh computers and iOS devices using Wi-Fi and Bluetooth. However, if you're using Linux and missing o




