The regreSSHion (CVE-2024-6387) Bug Is Patched In OpenSSH 9.8

Recently, security researchers uncovered a critical vulnerability, dubbed "regreSSHion" (CVE-2024-6387), within the widely-used OpenSSH secure communication tool. This flaw poses a significant risk, potentially enabling remote attackers to execute malicious code on affected systems. This article details the vulnerability and provides essential mitigation steps.
Table of Contents
- Affected OpenSSH Versions
- OpenSSH 9.8: The Solution
- Race Condition in sshd(8)
- Logic Error in ssh(1) ObscureKeystrokeTiming
- Securing Your System
- Key Findings
- Summary
Understanding the regreSSHion (CVE-2024-6387) Vulnerability
The Qualys Threat Research Unit (TRU) discovered regreSSHion, an unauthenticated Remote Code Execution (RCE) vulnerability in the OpenSSH server (sshd) component. This critical flaw, impacting Linux systems utilizing glibc, allows attackers to achieve root privileges without any user interaction. Remarkably, this is the first major OpenSSH vulnerability in nearly two decades.
Affected OpenSSH Versions
Versions prior to 4.4p1 and versions ranging from 8.5p1 to 9.7p1 (exclusive of 9.8p1) are susceptible to this vulnerability.
OpenSSH 9.8: The Solution
Released on July 1, 2024, OpenSSH 9.8 directly addresses the regreSSHion vulnerability and another security issue:
1. Race Condition in sshd(8)
The regreSSHion vulnerability in sshd(8) (versions 8.5p1 through 9.7p1) allows for arbitrary code execution with root privileges. Successful exploitation has been demonstrated on 32-bit Linux/glibc systems with ASLR enabled. While 64-bit exploitation is considered feasible, it remains unconfirmed. Importantly, OpenBSD systems are unaffected. This vulnerability was reported by the Qualys Security Advisory Team.
2. Logic Error in ssh(1) ObscureKeystrokeTiming
OpenSSH versions 9.5 through 9.7 contained a logic error in the ssh(1) ObscureKeystrokeTiming feature, rendering it ineffective. This allowed passive observation of network packets to reveal keystroke timing information, compromising a long-standing security measure against timing attacks. This flaw was independently discovered by Philippos Giavridis and researchers from the University of Cambridge Computer Lab.
Securing Your System
Immediate updating to OpenSSH 9.8 or a later version is crucial. This update resolves both vulnerabilities. Many Linux distributions already include the patched version in their default repositories. Use the following commands to update (adapt commands to your specific distribution):
# Alpine Linux sudo apk update && sudo apk upgrade openssh # Arch Linux sudo pacman -Syu openssh # Debian-based (Debian, Ubuntu) sudo apt update && sudo apt upgrade openssh-server # Red Hat-based (RHEL, CentOS, Fedora) sudo dnf check-update && sudo dnf update openssh-server # Older RHEL/CentOS sudo yum check-update && sudo yum update openssh-server # SUSE-based (openSUSE, SLES) sudo zypper refresh && sudo zypper update openssh
Verify the update by running: ssh -V
Key Findings
OpenSSH 9.8, released July 1, 2024, patches two critical vulnerabilities:
- Critical sshd Vulnerability: Affects versions 8.5p1 to 9.7p1, potentially granting unauthorized root access. Successfully exploited on 32-bit Linux/glibc systems with ASLR. OpenBSD is not vulnerable. (Discovered by Qualys)
- Timing Attack Vulnerability: Affects versions 9.5 to 9.7, potentially exposing keystroke timing information. (Discovered by Philippos Giavridis and University of Cambridge researchers)
Summary
The regreSSHion vulnerability marks the first major OpenSSH flaw in approximately 20 years, highlighting the continuous need for security updates. Immediate upgrading to OpenSSH 9.8 is strongly recommended.
Resource:
- OpenSSH 9.8 Release Notes
The above is the detailed content of The regreSSHion (CVE-2024-6387) Bug Is Patched In OpenSSH 9.8. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
How To Count Files And Directories In Linux: A Beginner's Guide
Mar 19, 2025 am 10:48 AM
Efficiently Counting Files and Folders in Linux: A Comprehensive Guide Knowing how to quickly count files and directories in Linux is crucial for system administrators and anyone managing large datasets. This guide demonstrates using simple command-l
 How To Add A User To Multiple Groups In Linux
Mar 18, 2025 am 11:44 AM
How To Add A User To Multiple Groups In Linux
Mar 18, 2025 am 11:44 AM
Efficiently managing user accounts and group memberships is crucial for Linux/Unix system administration. This ensures proper resource and data access control. This tutorial details how to add a user to multiple groups in Linux and Unix systems. We
 How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
How To List Or Check All Installed Linux Kernels From Commandline
Mar 23, 2025 am 10:43 AM
Linux Kernel is the core component of a GNU/Linux operating system. Developed by Linus Torvalds in 1991, it is a free, open-source, monolithic, modular, and multitasking Unix-like kernel. In Linux, it is possible to install multiple kernels on a sing
 How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
How To Type Indian Rupee Symbol In Ubuntu Linux
Mar 22, 2025 am 10:39 AM
This brief guide explains how to type Indian Rupee symbol in Linux operating systems. The other day, I wanted to type "Indian Rupee Symbol (₹)" in a word document. My keyboard has a rupee symbol on it, but I don't know how to type it. After
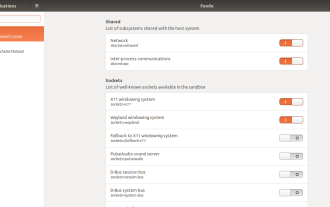 How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
How To Easily Configure Flatpak Apps Permissions With Flatseal
Mar 22, 2025 am 09:21 AM
Flatpak application permission management tool: Flatseal User Guide Flatpak is a tool designed to simplify Linux software distribution and use. It safely encapsulates applications in a virtual sandbox, allowing users to run applications without root permissions without affecting system security. Because Flatpak applications are located in this sandbox environment, they must request permissions to access other parts of the operating system, hardware devices (such as Bluetooth, network, etc.) and sockets (such as pulseaudio, ssh-auth, cups, etc.). This guide will guide you on how to easily configure Flatpak with Flatseal on Linux
 What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
What is the Linux best used for?
Apr 03, 2025 am 12:11 AM
Linux is best used as server management, embedded systems and desktop environments. 1) In server management, Linux is used to host websites, databases, and applications, providing stability and reliability. 2) In embedded systems, Linux is widely used in smart home and automotive electronic systems because of its flexibility and stability. 3) In the desktop environment, Linux provides rich applications and efficient performance.
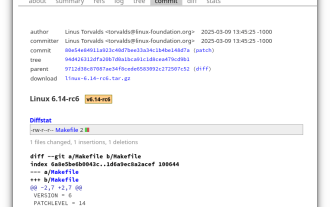 Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linux Kernel 6.14 RC6 Released
Mar 24, 2025 am 10:21 AM
Linus Torvalds has released Linux Kernel 6.14 Release Candidate 6 (RC6), reporting no significant issues and keeping the release on track. The most notable change in this update addresses an AMD microcode signing issue, while the rest of the updates
 LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
LocalSend - The Open-Source Airdrop Alternative For Secure File Sharing
Mar 24, 2025 am 09:20 AM
If you're familiar with AirDrop, you know it's a popular feature developed by Apple Inc. that enables seamless file transfer between supported Macintosh computers and iOS devices using Wi-Fi and Bluetooth. However, if you're using Linux and missing o




