 System Tutorial
System Tutorial
 Windows Series
Windows Series
 Creating an Encrypted Backup Drive That Works on Windows, Mac, and Linux
Creating an Encrypted Backup Drive That Works on Windows, Mac, and Linux
Creating an Encrypted Backup Drive That Works on Windows, Mac, and Linux
Protecting Your Digital Life: Creating Encrypted Backups with VeraCrypt
Our digital lives are brimming with irreplaceable memories, crucial documents, and essential work files. The loss of these due to device failure, theft, or ransomware attacks could be devastating. This is why creating secure, encrypted backups is paramount. This guide shows you how to create an encrypted backup drive compatible with any PC using VeraCrypt.
Why Encrypt Your Backups?
The sensitive nature of the data stored on backup drives necessitates encryption. Even with trusted storage, loss or theft exposes your personal information to risks like identity theft, financial fraud, and extortion. Encrypted backups, secured by a strong password, are the only way to ensure your data remains safe.
VeraCrypt: The Cross-Platform Encryption Solution
While Windows (BitLocker) and macOS (FileVault) offer built-in encryption, their cross-platform compatibility is limited. VeraCrypt, however, is a free, open-source disk encryption tool compatible with Windows, macOS, and Linux. This ensures you can access your backups from virtually any computer.

Creating an Encrypted VeraCrypt Backup Container
VeraCrypt offers a user-friendly interface for creating encrypted containers—files acting as virtual drives. These containers bundle all your backup files into a single, easily transferable file.
-
Download and Install VeraCrypt: Download VeraCrypt from its official website and install it.
-
Create a Volume: Open VeraCrypt and select "Create Volume."

- Choose Container Type: Select "Create an encrypted file container" and then "Standard VeraCrypt volume."

- Select Location and Name: Choose your backup drive and give the container a descriptive name (e.g., "offsite_backups.veracrypt").

- Encryption Options: Accept the default encryption settings. Set the volume size according to your data and drive capacity.
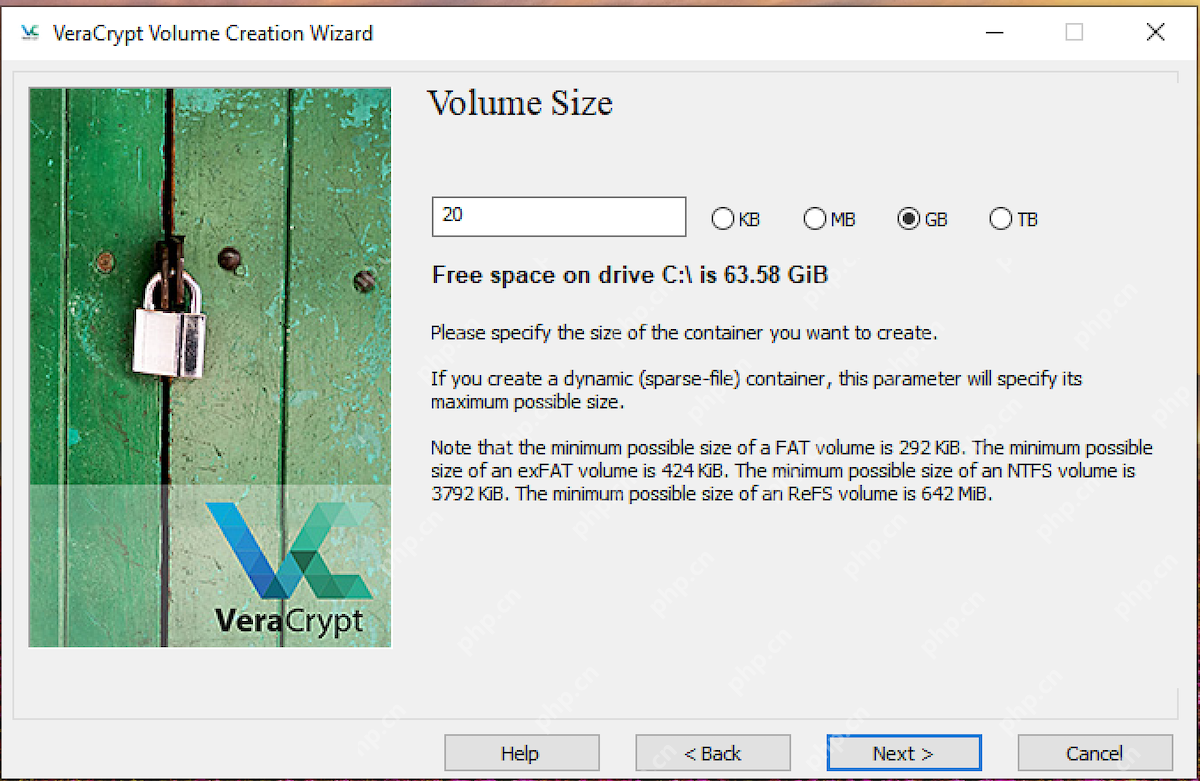
- Set a Strong Password: Create a robust password to protect your container.

- Large Files and Filesystem: Select "Yes" for large files and ensure the Filesystem is set to exFAT for broad compatibility.

- Create Random Data: Move your mouse randomly to generate encryption keys. Click "Format."

- Mount the Container: Select an unused drive letter, choose your encrypted container, and click "Mount." Enter your password.

- Access and Use: The mounted volume will appear in File Explorer. Remember to safely dismount it using VeraCrypt before disconnecting the drive.

Automating Backups with SyncBack (or rsync)
Once your encrypted container is ready, use a backup tool like SyncBack (cross-platform) or rsync (command-line) to automate regular backups. Remember to always verify your backups are accessible and contain the necessary files.

Your Responsibility: Proactive Cybersecurity
Regular backups and secure practices are essential for protecting your digital life. Don't wait for disaster—take action today.
The above is the detailed content of Creating an Encrypted Backup Drive That Works on Windows, Mac, and Linux. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1378
1378
 52
52
 win11 activation key permanent 2025
Mar 18, 2025 pm 05:57 PM
win11 activation key permanent 2025
Mar 18, 2025 pm 05:57 PM
Article discusses sources for a permanent Windows 11 key valid until 2025, legal issues, and risks of using unofficial keys. Advises caution and legality.
 win11 activation key permanent 2024
Mar 18, 2025 pm 05:56 PM
win11 activation key permanent 2024
Mar 18, 2025 pm 05:56 PM
Article discusses reliable sources for permanent Windows 11 activation keys in 2024, legal implications of third-party keys, and risks of using unofficial keys.
 Acer PD163Q Dual Portable Monitor Review: I Really Wanted to Love This
Mar 18, 2025 am 03:04 AM
Acer PD163Q Dual Portable Monitor Review: I Really Wanted to Love This
Mar 18, 2025 am 03:04 AM
The Acer PD163Q Dual Portable Monitor: A Connectivity Nightmare I had high hopes for the Acer PD163Q. The concept of dual portable displays, conveniently connecting via a single cable, was incredibly appealing. Unfortunately, this alluring idea quic
 How to Create a Dynamic Table of Contents in Excel
Mar 24, 2025 am 08:01 AM
How to Create a Dynamic Table of Contents in Excel
Mar 24, 2025 am 08:01 AM
A table of contents is a total game-changer when working with large files – it keeps everything organized and easy to navigate. Unfortunately, unlike Word, Microsoft Excel doesn’t have a simple “Table of Contents” button that adds t
 ReactOS, the Open-Source Windows, Just Got an Update
Mar 25, 2025 am 03:02 AM
ReactOS, the Open-Source Windows, Just Got an Update
Mar 25, 2025 am 03:02 AM
ReactOS 0.4.15 includes new storage drivers, which should help with overall stability and UDB drive compatibility, as well as new drivers for networking. There are also many updates to fonts support, the desktop shell, Windows APIs, themes, and file
 Shopping for a New Monitor? 8 Mistakes to Avoid
Mar 18, 2025 am 03:01 AM
Shopping for a New Monitor? 8 Mistakes to Avoid
Mar 18, 2025 am 03:01 AM
Buying a new monitor isn't a frequent occurrence. It's a long-term investment that often moves between computers. However, upgrading is inevitable, and the latest screen technology is tempting. But making the wrong choices can leave you with regret
 How to Use Voice Access in Windows 11
Mar 18, 2025 pm 08:01 PM
How to Use Voice Access in Windows 11
Mar 18, 2025 pm 08:01 PM
Detailed explanation of the voice access function of Windows 11: Free your hands and control your computer with voice! Windows 11 provides numerous auxiliary functions to help users with various needs to use the device easily. One of them is the voice access function, which allows you to control your computer completely through voice. From opening applications and files to entering text with voice, everything is at your fingertips, but first you need to set up and learn key commands. This guide will provide details on how to use voice access in Windows 11. Windows 11 Voice Access Function Settings First, let's take a look at how to enable this feature and configure Windows 11 voice access for the best results. Step 1: Open the Settings menu
 New to Multi-Monitors? Don't Make These Mistakes
Mar 25, 2025 am 03:12 AM
New to Multi-Monitors? Don't Make These Mistakes
Mar 25, 2025 am 03:12 AM
Multi-monitor setups boost your productivity and deliver a more immersive experience. However, it's easy for a novice to stumble while assembling the setup and make mistakes. Here are some of the most common ones and how to avoid them.



