用户权力详解
有耐心就看完(还是算法重要)
用户初始权值:Enable = 0;
假如一个用户有第一项权力Select,则用户权值:Enable = Enable + 1;
假如一个用户有第二项权力Insert,则用户权值:Enable = Enable + 2;
假如一个用户有第三项权力Update,则用户权值:Enable = Enable + 4;
假如一个用户有第四项权力Delete,则用户权值:Enable = Enable + 8;
为什么依次+1、+2、+4、+8,而不是+1、+2、+3、+4呢?
假如是+1、+2、+3、+4:
假如一个用户有第一项权力Select,则用户权值:Enable = Enable + 1;
假如一个用户有第二项权力Insert,则用户权值:Enable = Enable + 2;
假如一个用户有第三项权力Update,则用户权值:Enable = Enable + 3;
假如一个用户有第四项权力Delete,则用户权值:Enable = Enable + 4;
那么当用户权值:Enable = 3时,你就无法判断用户到底是同时拥有
第一项权力Select和第二项权力Insert两项权利,还是仅拥有第三项权力Update,
前一种权值算法就可以避免这种情况。
但是当采用前一种权值算法时,怎样由用户的权值Enable快速知道用户拥有哪几项权
力呢?假如是用户权值Enable = 5,用户拥有第一项权力Select和第三项权力Update,
注意不拥有第二项权力Insert。
下面我将用户权力列表:
权力 拥有权力用户的权值Enable
SelectItem:( 1, 3, 5, 7, 9, 11, 13, 15 )
InsertItem:( 2, 3, 6, 7, 10, 11, 14, 15 )
UpdateItem:( 4, 5, 6, 7, 12, 13, 14, 15 )
DeleteItem:( 8, 9, 10, 11, 12, 13, 14, 15 )
可见并不是权值Enable大的用户就拥有“更多”的权力,
假如 :用户权值Enable = 3,用户拥有第一项权力(Select)和第二项权力(Insert),共两项权利,
用户权值Enable = 4,用户拥有第三项权力(Update),仅一项权利。
仔细观察“用户权力列表”:
SelectItem:( 1, 3, 5, 7, 9, 11, 13, 15 ): 1 = 0 + 2 的0次幂;3 = 2 的1次幂 + 2 的0次幂;5 = 2 的2次幂 + 2 的0次幂;
InsertItem:( 2, 3, 6, 7, 10, 11, 14, 15 ): 2 = 0 + 2 的1次幂;3 = 2 的0次幂 + 2 的1次幂;6 = 2 的2次幂 + 2 的1次幂;
UpdateItem:( 4, 5, 6, 7, 12, 13, 14, 15 ): 4 = 0 + 2 的2次幂;5 = 2 的0次幂 + 2 的2次幂;6 = 2 的2次幂 + 2 的2次幂;
DeleteItem:( 8, 9, 10, 11, 12, 13, 14, 15 ):8 = 0 + 2 的3次幂;9 = 2 的0次幂 + 2 的3次幂 10 = 2 的1次幂 + 2 的3次幂;
规律总结如下:
拥有第一项权力Select用户的权值:Enable = ? + 2 的0次幂;(其中?亦必须拆成2 的N次幂相加的情况)
拥有第二项权力Insert用户的权值:Enable = ? + 2 的1次幂;(其中?亦必须拆成2 的N次幂相加的情况)
拥有第三项权力Update用户的权值:Enable = ? + 2 的2次幂;(其中?亦必须拆成2 的N次幂相加的情况)
拥有第四项权力Delete用户的权值:Enable = ? + 2 的3次幂;(其中?亦必须拆成2 的N次幂相加的情况)
到此已经很清楚了:
只要将用户的权值Enable拆成2 的N次幂相加的情况,
如果其中有N=0,则拥有第一项权力Select,
如果其中有N=1,则拥有第二项权力Insert,
如果其中有N=2,则拥有第三项权力Update,
如果其中有N=3,则拥有第四项权力Delete,
那么怎样将用户权值Enable快拆成2 的N次幂相加的情况呢?
呵呵!只要将Enable转化为二进制,从右向左依次取基,若基为的位则拥有相应权利,
举例:
(11)10=(1011)2,即拥有第一、二、四项权力,和“用户权力列表”相符;
(12)10=(1100)2,即拥有第三、四项权力,和“用户权力列表”相符;
(15)10=(1111)2,即拥有第一、二、三、四项权力,和“用户权力列表”相符;
当权利等级极其复杂时,该算法可以很快知道用户权力:
例如:
共8个等级,用户权值Enable=67;(67)10=(1000011)2,即拥有第一、六、七项权力,
用户权值Enable=67;(159)10=(10011111)2,即拥有第一、四、五、六、七、八项权力。
到此结束,希望没有浪费您的时间,对您有所启发。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use Xiaohongshu account to find users? Can I find my mobile phone number?
Mar 22, 2024 am 08:40 AM
How to use Xiaohongshu account to find users? Can I find my mobile phone number?
Mar 22, 2024 am 08:40 AM
With the rapid development of social media, Xiaohongshu has become one of the most popular social platforms. Users can create a Xiaohongshu account to show their personal identity and communicate and interact with other users. If you need to find a user’s Xiaohongshu number, you can follow these simple steps. 1. How to use Xiaohongshu account to find users? 1. Open the Xiaohongshu APP, click the "Discover" button in the lower right corner, and then select the "Notes" option. 2. In the note list, find the note posted by the user you want to find. Click to enter the note details page. 3. On the note details page, click the "Follow" button below the user's avatar to enter the user's personal homepage. 4. In the upper right corner of the user's personal homepage, click the three-dot button and select "Personal Information"
 Log in to Ubuntu as superuser
Mar 20, 2024 am 10:55 AM
Log in to Ubuntu as superuser
Mar 20, 2024 am 10:55 AM
In Ubuntu systems, the root user is usually disabled. To activate the root user, you can use the passwd command to set a password and then use the su- command to log in as root. The root user is a user with unrestricted system administrative rights. He has permissions to access and modify files, user management, software installation and removal, and system configuration changes. There are obvious differences between the root user and ordinary users. The root user has the highest authority and broader control rights in the system. The root user can execute important system commands and edit system files, which ordinary users cannot do. In this guide, I'll explore the Ubuntu root user, how to log in as root, and how it differs from a normal user. Notice
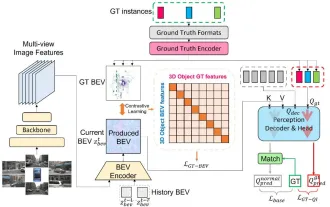 CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
CLIP-BEVFormer: Explicitly supervise the BEVFormer structure to improve long-tail detection performance
Mar 26, 2024 pm 12:41 PM
Written above & the author’s personal understanding: At present, in the entire autonomous driving system, the perception module plays a vital role. The autonomous vehicle driving on the road can only obtain accurate perception results through the perception module. The downstream regulation and control module in the autonomous driving system makes timely and correct judgments and behavioral decisions. Currently, cars with autonomous driving functions are usually equipped with a variety of data information sensors including surround-view camera sensors, lidar sensors, and millimeter-wave radar sensors to collect information in different modalities to achieve accurate perception tasks. The BEV perception algorithm based on pure vision is favored by the industry because of its low hardware cost and easy deployment, and its output results can be easily applied to various downstream tasks.
 Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Windows operating system is one of the most popular operating systems in the world, and its new version Win11 has attracted much attention. In the Win11 system, obtaining administrator rights is an important operation. Administrator rights allow users to perform more operations and settings on the system. This article will introduce in detail how to obtain administrator permissions in Win11 system and how to effectively manage permissions. In the Win11 system, administrator rights are divided into two types: local administrator and domain administrator. A local administrator has full administrative rights to the local computer
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in OracleSQL In OracleSQL, division operation is a common and important mathematical operation, used to calculate the result of dividing two numbers. Division is often used in database queries, so understanding the division operation and its usage in OracleSQL is one of the essential skills for database developers. This article will discuss the relevant knowledge of division operations in OracleSQL in detail and provide specific code examples for readers' reference. 1. Division operation in OracleSQL
 Analysis of user password storage mechanism in Linux system
Mar 20, 2024 pm 04:27 PM
Analysis of user password storage mechanism in Linux system
Mar 20, 2024 pm 04:27 PM
Analysis of user password storage mechanism in Linux system In Linux system, the storage of user password is one of the very important security mechanisms. This article will analyze the storage mechanism of user passwords in Linux systems, including the encrypted storage of passwords, the password verification process, and how to securely manage user passwords. At the same time, specific code examples will be used to demonstrate the actual operation process of password storage. 1. Encrypted storage of passwords In Linux systems, user passwords are not stored in the system in plain text, but are encrypted and stored. L
 Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
Explore the underlying principles and algorithm selection of the C++sort function
Apr 02, 2024 pm 05:36 PM
The bottom layer of the C++sort function uses merge sort, its complexity is O(nlogn), and provides different sorting algorithm choices, including quick sort, heap sort and stable sort.






