BKDRHash php兑现
BKDRHash php实现
接上一帖 BKDRHash的php实现 比c语言版本复杂的部分,是由于php中整型数的范围是,且一定是-2147483648 到2147483647,并且没有无符号整形数,在算法中会出现大数溢出的问题,不能使用intval,需要用floatval,同时在运算过程中取余保证不溢出。
<?phpfunction BKDRHash($str){ $seed = 131; // 31 131 1313 13131 131313 etc.. $hash = 0; $cnt = strlen($str); for($i = 0; $i < $cnt; $i++) { $hash = ((floatval($hash * $seed) & 0x7FFFFFFF) + ord($str[$i])) & 0x7FFFFFFF; } return ($hash & 0x7FFFFFFF);}echo BKDRHash('ggsonic');//1471979560echo BKDRHash('asdfasdfasdf123'); // 1220655578?>
Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1377
1377
 52
52
 How to implement Redis Hash operation in php
May 30, 2023 am 08:58 AM
How to implement Redis Hash operation in php
May 30, 2023 am 08:58 AM
Hash operation //Assign values to fields in the hash table. Returns 1 on success and 0 on failure. If the hash table does not exist, the table will be created first and then the value will be assigned. If the field already exists, the old value will be overwritten. $ret=$redis->hSet('user','realname','jetwu');//Get the value of the specified field in the hash table. If the hash table does not exist, return false. $ret=$redis->hGet('user','rea
 Laravel development: How to generate password hash using Laravel Hash?
Jun 17, 2023 am 10:59 AM
Laravel development: How to generate password hash using Laravel Hash?
Jun 17, 2023 am 10:59 AM
Laravel is currently one of the most popular PHP web frameworks, providing developers with many powerful features and components, among which LaravelHash is one of them. LaravelHash is a PHP library for password hashing that can be used to keep passwords secure and make your application's user data more secure. In this article, we will learn how LaravelHash works and how to use it to hash and verify passwords. Prerequisite knowledge in learning Lara
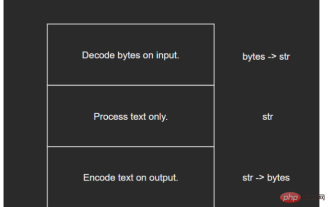 Python built-in type str source code analysis
May 09, 2023 pm 02:16 PM
Python built-in type str source code analysis
May 09, 2023 pm 02:16 PM
1The basic unit of Unicode computer storage is the byte, which is composed of 8 bits. Since English only consists of 26 letters plus a number of symbols, English characters can be stored directly in bytes. But other languages (such as Chinese, Japanese, Korean, etc.) have to use multiple bytes for encoding due to the large number of characters. With the spread of computer technology, non-Latin character encoding technology continues to develop, but there are still two major limitations: no multi-language support: the encoding scheme of one language cannot be used in another language and there is no unified standard: for example There are many encoding standards in Chinese such as GBK, GB2312, GB18030, etc. Since the encoding methods are not unified, developers need to convert back and forth between different encodings, and many errors will inevitably occur.
 What are the similarities and differences between __str__ and __repr__ in Python?
Apr 29, 2023 pm 07:58 PM
What are the similarities and differences between __str__ and __repr__ in Python?
Apr 29, 2023 pm 07:58 PM
What are the similarities and differences between __str__ and __repr__? We all know the representation of strings. Python's built-in function repr() can express objects in the form of strings to facilitate our identification. This is the "string representation". repr() obtains the string representation of an object through the special method __repr__. If __repr__ is not implemented, when we print an instance of a vector to the console, the resulting string may be. >>>classExample:pass>>>print(str(Example()))>>>
 Understand the Hash algorithm and application scenarios in one article
Apr 13, 2023 am 11:55 AM
Understand the Hash algorithm and application scenarios in one article
Apr 13, 2023 am 11:55 AM
1. What is a hashing algorithm? Both hashing and hashing come from the word hash. The former is a transliteration and the latter is a free translation. It is an algorithm that can map a binary value of any length into a fixed-length binary value. The mapped fixed-length binary value is called a hash value. An excellent hash algorithm needs to meet the following requirements: it cannot reversely deduce the original data from the hash value; it is very sensitive to the input data, and a different bit will cause the hash value to be very different; the probability of hash conflict must be Very small; the calculation process of the hash algorithm must be simple and efficient enough, even if the original data is very long, the hash value can be obtained quickly; 2. Usage scenarios of the hash algorithm 2.1 Secure encryption The more common hash encryption algorithms include MD5 ( MD5 Message-Dige
 Convert variable to float using PHP function 'floatval'
Jul 24, 2023 pm 11:57 PM
Convert variable to float using PHP function 'floatval'
Jul 24, 2023 pm 11:57 PM
Convert a variable to a floating point type using the PHP function "floatval" In PHP, we often need to convert a variable to a floating point type. This is useful when dealing with numerical calculations, currency transactions, etc. PHP provides a built-in function called "floatval" that can help us quickly convert variables to floating point types. The syntax of the "floatval" function is as follows: floatval(mixed$var): float This function accepts a parameter $var
 Analysis of common operation examples of Hash, the basic data type of Redis
May 31, 2023 am 10:43 AM
Analysis of common operation examples of Hash, the basic data type of Redis
May 31, 2023 am 10:43 AM
Common operations of Redis data type Hash Hash in redis is a mapping table of string type fields and values. Particularly suitable for storing objects, each hash can store more than 4 billion key-value pairs. Children's shoes who are familiar with python can think of it as a dictionary dict. The previous data type storage was k-v, and the hash storage is k-dict, and the dict will have its own k-v. 1. hset assigns values to the fields in the hash table. If the hash table does not exist, create a new hash table and perform the hset operation. If the field already exists in the hash table, the old value will be overwritten. hsetmyhashk1v1 two, h
 Use it every day! Do you know what HASH is?
Jul 26, 2023 pm 02:47 PM
Use it every day! Do you know what HASH is?
Jul 26, 2023 pm 02:47 PM
The main idea of the hashing method is to determine the storage address of the node based on its key value: taking the key value K as the independent variable, and through a certain functional relationship h(K) (called a hash function), the corresponding The function value comes




