用户参与记录存储的演变
有这样一个应用场景:用户有两个连续的操作A和操作B,必须是操作A完成后才能执行操作B,如果操作A没有完成就触发了操作B,则显示用户需要先执行操作A,即在操作B执行需要查询操作A是否执行过。这里引申出来的问题是,记录用户参与记录,提供针对用户和操作的查询方法。当不同的数据量时,我们的存储方案会大不相同,随着数据的增长,方案不断演变。
1、数据量较小,用户操作行为固定:
存储:MySQL
方案:我们以UID为key,一行一个用户,每个用户包括的用户作为列存储,比如UID=100,固定存储为操作A和操作B,则表结构大致如下:
table_operation
uid operation_a operation_b
100 1 1
如果我们要查询用户是否参与A或B时,直接使用SQL: SELECT * FROM table_operation WHERE uid=100 AND action_a=1就可以达成目标。
问题:用户操作固定,扩展较难,如果需要增加用户操作行为,则需要增加字段或增加表存储,增加字段的方法在一定的数据量级以下(比如100万)是可行的,如果行为间无关,则增加表存储方案的表现会很不错。
2、数据量较小、用户操作行为不固定:
与场景1相比,当前场景除了uid这个变量,增加了用户操作变量,即我们需要关注用户和用户操作两个变量。
存储:MySQL
方案1:增加操作表,生成操作id,用户操作行为表存储uid和oid。当用户执行一个新的操作时就在操作行为表插入一条记录。其表结构大致如下:
table_operation_info
oid name
1 operation_a
2 operation_b
table_operation
uid oid
1 1
1 2
当需要查询用户1是否执行过操作A时,使用SQL:SELECT * FROM table_operation WHERE oid=1 AND oid=1。
问题:当用户的操作行为较多时,用户操作行为增长速度很快,数据量也为逐渐增大,可能MySQL单表无法负载。解决方案在后续场景中说明。
3、数据量较大,用户行为固定
存储:MySQL
方案:与场景1相比,当前场景不同在于数据量比场景1大,数据量大到MySQL单表负载不过来。此方案解决的就是这个问题,当单表太大时,性价比较高的方法一般是采用分表。我们当前场景的变量是uid,只要依据uid按水平分表即可。
4、数据量较大,用户行为不固定
存储: MySQL
方案1:此方案应用于用户的操作行为可以分类的情况,即在场景1的基础上增加两次分表操作,按操作行为类分表和按用户分表。当前方案中我们需要应对两个变量:操作行为和用户。两次分表分别对应这两个变量,按业务规则做操作行为的分表操作,按用户id水平切分减少数据量。
方案2:此方案是完全的水平分表操作,在场景2的方案基础上,按用户水平切分。
5、数据量超大
存储: MySQL
方案1:分库分表,此时一个库已经无法满足需求,规则依据前面的场景实现,根据实际的需求可以考虑把不同的库放不同的机器上。
方案2:在分库分表的基础上,按位存储,因为一个操作行为有没有执行过是一个是否的状态,即0,1状态,因此我们可以用一个位来存储,64位可以存储64个操作行为的标记。
其它存储
key-value数据库
我们的需求实际上并不需要太多的关系型数据库的功能,简单的 k-v数据库就可以实现我们的功能,并且在性能上也会有所提升,毕竟做得少,会快。
先不管是选择基于内存的,还是非内存的(可以根据实际需求来选择,也可以是热点数据在内存,沉默数据在非内存中),假设我们有足够的空间存储。
方案1:
以uid+oid为key,值可以存储状态,也可以只存储是否参与(0和1),但是会存在key太多的情况,特别是当数据量超大时,uid的个数*oid的个数,可能是你无法相像的量级。
方案2:
一般来说,用户操作行为的数据量完全小于用户的量级,并且用户操作行为的数据可控。如果要减少key的个数,我们可以使用oid+用户分区索引id作为key,这里所谓的用户分区索引是指将用户以某个数量分成一个区,所有的用户都记录在这个这个区间内,比如以10000为一个区间,则uid为1到9999的用户分到区间0,这里可以以1和0存储用户是否执行了此操作,一个key对应的value初始化存储10000个0。当uid=100的用户执行了某操作,则将第100个0置为1。
方案3:
在方案2的基础上,将10000个0转换为10000个01位,假设一个位存储50位,则总共只需要200个。
方案4:
当用户量超大时,大多数的用户对于某个操作可能都是没有参与的,则在方案3的基础上我们增加简单的稀疏矩阵压缩,给每个存储位添加索引,当存储值不为0时才会存储。
方案5:
我还没想到,期待你的分享
小结
•随着数据量的增大,总的思路是分冶,当一个表搞不定时分表,当一个库搞不定时分库,当一台机器搞不定时加机器。
•对于不同的存储介质选择需要考虑成本和需求,所有的选择都是平衡后的结果。
•节省空间,按位存储。
•不要过早优化。

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1385
1385
 52
52
 How to use Xiaohongshu account to find users? Can I find my mobile phone number?
Mar 22, 2024 am 08:40 AM
How to use Xiaohongshu account to find users? Can I find my mobile phone number?
Mar 22, 2024 am 08:40 AM
With the rapid development of social media, Xiaohongshu has become one of the most popular social platforms. Users can create a Xiaohongshu account to show their personal identity and communicate and interact with other users. If you need to find a user’s Xiaohongshu number, you can follow these simple steps. 1. How to use Xiaohongshu account to find users? 1. Open the Xiaohongshu APP, click the "Discover" button in the lower right corner, and then select the "Notes" option. 2. In the note list, find the note posted by the user you want to find. Click to enter the note details page. 3. On the note details page, click the "Follow" button below the user's avatar to enter the user's personal homepage. 4. In the upper right corner of the user's personal homepage, click the three-dot button and select "Personal Information"
 Log in to Ubuntu as superuser
Mar 20, 2024 am 10:55 AM
Log in to Ubuntu as superuser
Mar 20, 2024 am 10:55 AM
In Ubuntu systems, the root user is usually disabled. To activate the root user, you can use the passwd command to set a password and then use the su- command to log in as root. The root user is a user with unrestricted system administrative rights. He has permissions to access and modify files, user management, software installation and removal, and system configuration changes. There are obvious differences between the root user and ordinary users. The root user has the highest authority and broader control rights in the system. The root user can execute important system commands and edit system files, which ordinary users cannot do. In this guide, I'll explore the Ubuntu root user, how to log in as root, and how it differs from a normal user. Notice
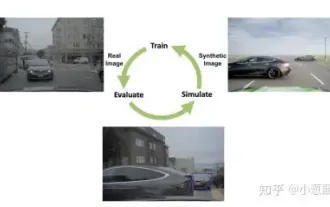 How to solve the long tail problem in autonomous driving scenarios?
Jun 02, 2024 pm 02:44 PM
How to solve the long tail problem in autonomous driving scenarios?
Jun 02, 2024 pm 02:44 PM
Yesterday during the interview, I was asked whether I had done any long-tail related questions, so I thought I would give a brief summary. The long-tail problem of autonomous driving refers to edge cases in autonomous vehicles, that is, possible scenarios with a low probability of occurrence. The perceived long-tail problem is one of the main reasons currently limiting the operational design domain of single-vehicle intelligent autonomous vehicles. The underlying architecture and most technical issues of autonomous driving have been solved, and the remaining 5% of long-tail problems have gradually become the key to restricting the development of autonomous driving. These problems include a variety of fragmented scenarios, extreme situations, and unpredictable human behavior. The "long tail" of edge scenarios in autonomous driving refers to edge cases in autonomous vehicles (AVs). Edge cases are possible scenarios with a low probability of occurrence. these rare events
 How to Undo Delete from Home Screen in iPhone
Apr 17, 2024 pm 07:37 PM
How to Undo Delete from Home Screen in iPhone
Apr 17, 2024 pm 07:37 PM
Deleted something important from your home screen and trying to get it back? You can put app icons back on the screen in a variety of ways. We have discussed all the methods you can follow and put the app icon back on the home screen. How to Undo Remove from Home Screen in iPhone As we mentioned before, there are several ways to restore this change on iPhone. Method 1 – Replace App Icon in App Library You can place an app icon on your home screen directly from the App Library. Step 1 – Swipe sideways to find all apps in the app library. Step 2 – Find the app icon you deleted earlier. Step 3 – Simply drag the app icon from the main library to the correct location on the home screen. This is the application diagram
 The role and practical application of arrow symbols in PHP
Mar 22, 2024 am 11:30 AM
The role and practical application of arrow symbols in PHP
Mar 22, 2024 am 11:30 AM
The role and practical application of arrow symbols in PHP In PHP, the arrow symbol (->) is usually used to access the properties and methods of objects. Objects are one of the basic concepts of object-oriented programming (OOP) in PHP. In actual development, arrow symbols play an important role in operating objects. This article will introduce the role and practical application of arrow symbols, and provide specific code examples to help readers better understand. 1. The role of the arrow symbol to access the properties of an object. The arrow symbol can be used to access the properties of an object. When we instantiate a pair
 From beginner to proficient: Explore various application scenarios of Linux tee command
Mar 20, 2024 am 10:00 AM
From beginner to proficient: Explore various application scenarios of Linux tee command
Mar 20, 2024 am 10:00 AM
The Linuxtee command is a very useful command line tool that can write output to a file or send output to another command without affecting existing output. In this article, we will explore in depth the various application scenarios of the Linuxtee command, from entry to proficiency. 1. Basic usage First, let’s take a look at the basic usage of the tee command. The syntax of tee command is as follows: tee[OPTION]...[FILE]...This command will read data from standard input and save the data to
 Analysis of user password storage mechanism in Linux system
Mar 20, 2024 pm 04:27 PM
Analysis of user password storage mechanism in Linux system
Mar 20, 2024 pm 04:27 PM
Analysis of user password storage mechanism in Linux system In Linux system, the storage of user password is one of the very important security mechanisms. This article will analyze the storage mechanism of user passwords in Linux systems, including the encrypted storage of passwords, the password verification process, and how to securely manage user passwords. At the same time, specific code examples will be used to demonstrate the actual operation process of password storage. 1. Encrypted storage of passwords In Linux systems, user passwords are not stored in the system in plain text, but are encrypted and stored. L
 Huawei Mate60 Pro screenshot operation steps sharing
Mar 23, 2024 am 11:15 AM
Huawei Mate60 Pro screenshot operation steps sharing
Mar 23, 2024 am 11:15 AM
With the popularity of smartphones, the screenshot function has become one of the essential skills for daily use of mobile phones. As one of Huawei's flagship mobile phones, Huawei Mate60Pro's screenshot function has naturally attracted much attention from users. Today, we will share the screenshot operation steps of Huawei Mate60Pro mobile phone, so that everyone can take screenshots more conveniently. First of all, Huawei Mate60Pro mobile phone provides a variety of screenshot methods, and you can choose the method that suits you according to your personal habits. The following is a detailed introduction to several commonly used interceptions:




