求php高手,看上这一段加密算法的原理
求php高手,看下这一段加密算法的原理
- PHP code
<!--
Code highlighting produced by Actipro CodeHighlighter (freeware)
http://www.CodeHighlighter.com/
-->
function sys_auth($str, $action = 'encode', $key = ''){
$key = md5($key);
$str = $action == 'encode' ? $str : base64_decode($str);
$strlen = strlen($str);
$keylen = strlen($key);
$code = '';
for($i = 0; $i 我将每句都echo 下的代码:
- PHP code
<!--
Code highlighting produced by Actipro CodeHighlighter (freeware)
http://www.CodeHighlighter.com/
-->
function sys_auth($str, $action = 'encode', $key = ''){
$key = md5($key);
echo '<br>$key:'.$key;
$str = $action == 'encode' ? $str : base64_decode($str);
echo '<br>加密方式的$str:'.$str;
$strlen = strlen($str);
echo '<br>$str长度'.$strlen;
$keylen = strlen($key);
echo '<br>$keylen长度'.$keylen;
$code = '';
for($i = 0; $i 第".$i."次循环的\$k的值是".$k;
$code .= $str[$i] ^ $key[$k];
echo "<br>第".$i.'次循环$k值是'.$k;
echo "<br>第".$i.'次循环$str[$i]值是'.$str[$i];
echo "<br>第".$i.'次循环$key[$k]值是'.$key[$k];
echo "<br>第".$i."次循环的\$code的值是".$code."<br><br><br><br><br>";
}
$code = $action == "decode" ? $code : base64_encode($code);
echo "<br>".$code;
return $code;
}
得到的结果是:
[code=PHP]
$key:c81e728d9d4c2f636f067f89cc14862c
加密方式的$str:123456
$str长度6
$keylen长度32
第0次循环的$k的值是0
第0次循环$k值是0
第0次循环$str[$i]值是1
第0次循环$key[$k]值是c
第0次循环的$code的值是R
第1次循环的$k的值是1
第1次循环$k值是1
第1次循环$str[$i]值是2
第1次循环$key[$k]值是8
第1次循环的$code的值是R
第2次循环的$k的值是2
第2次循环$k值是2
第2次循环$str[$i]值是3
第2次循环$key[$k]值是1
第2次循环的$code的值是R
第3次循环的$k的值是3
第3次循环$k值是3
第3次循环$str[$i]值是4
第3次循环$key[$k]值是e
第3次循环的$code的值是R Q
第4次循环的$k的值是4
第4次循环$k值是4
第4次循环$str[$i]值是5
第4次循环$key[$k]值是7
第4次循环的$code的值是R Q
第5次循环的$k的值是5
第5次循环$k值是5
第5次循环$str[$i]值是6
第5次循环$key[$k]值是2
第5次循环的$code的值是R Q
UgoCUQIE
加密后:UgoCUQIE
[/code]
现在的问题是:第0次循环$str[0]值是1,$key[0]值是c
我直接按照上面的 $str[0]^$key[0],(即1^0)却报错,怎么回事,另外 $str[0]^$key[0]不懂
------解决方案--------------------
手册,运算符

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1359
1359
 52
52
 What does the identity attribute in SQL mean?
Feb 19, 2024 am 11:24 AM
What does the identity attribute in SQL mean?
Feb 19, 2024 am 11:24 AM
What is Identity in SQL? Specific code examples are needed. In SQL, Identity is a special data type used to generate auto-incrementing numbers. It is often used to uniquely identify each row of data in a table. The Identity column is often used in conjunction with the primary key column to ensure that each record has a unique identifier. This article will detail how to use Identity and some practical code examples. The basic way to use Identity is to use Identit when creating a table.
 How SpringBoot monitors redis Key change events
May 26, 2023 pm 01:55 PM
How SpringBoot monitors redis Key change events
May 26, 2023 pm 01:55 PM
1. Function Overview Keyspace notification allows clients to receive events that modify Rediskey changes in some way by subscribing to channels or patterns. All commands that modify key keys. All keys that received the LPUSHkeyvalue[value…] command. All expired keys in the db database. Events are distributed through Redis's subscription and publishing functions (pub/sub), so all clients that support subscription and publishing functions can directly use the keyspace notification function without any modifications. Because the current subscription and publishing functions of Redis adopt a fireandforget strategy, if your program
 Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
Unpatchable Yubico two-factor authentication key vulnerability breaks the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices
Sep 04, 2024 pm 06:32 PM
An unpatchable Yubico two-factor authentication key vulnerability has broken the security of most Yubikey 5, Security Key, and YubiHSM 2FA devices. The Feitian A22 JavaCard and other devices using Infineon SLB96xx series TPMs are also vulnerable.All
 How to solve the problem of batch deletion of key values in redis
May 31, 2023 am 08:59 AM
How to solve the problem of batch deletion of key values in redis
May 31, 2023 am 08:59 AM
Problems encountered: During the development process, you will encounter keys that need to be deleted in batches according to certain rules, such as login_logID (ID is a variable). Now you need to delete data such as "login_log*", but redis itself only has batch query. Command keys for class key values, but there is no command for batch deletion of a certain class. Solution: Query first, then delete, use xargs to pass parameters (xargs can convert pipe or standard input (stdin) data into command line parameters), execute the query statement first, and then remove the queried key value and the original del parameters. delete. redis-cliKEYSkey* (search condition)|xargsr
 Edit your Unity project in Visual Studio Code and you are now ready to go
Aug 08, 2023 am 10:21 AM
Edit your Unity project in Visual Studio Code and you are now ready to go
Aug 08, 2023 am 10:21 AM
Microsoft has released a preview version of the Unity extension for Visual Studio Code. This new Unity extension will allow you to write and debug Unity games. This new Unity extension brings some popular features already available in Visual Studio and Visual Studio Tools for Unity, making C# in Visual Studio Code better for Unity development. Currently, the Unity extension for VSCode provides the following: A Unity debugger for debugging your Unity editor and Unity player. Unity-specific C# analyzer and refactoring. Uni
 php提交表单通过后,弹出的对话框怎样在当前页弹出,该如何解决
Jun 13, 2016 am 10:23 AM
php提交表单通过后,弹出的对话框怎样在当前页弹出,该如何解决
Jun 13, 2016 am 10:23 AM
php提交表单通过后,弹出的对话框怎样在当前页弹出php提交表单通过后,弹出的对话框怎样在当前页弹出而不是在空白页弹出?想实现这样的效果:而不是空白页弹出:------解决方案--------------------如果你的验证用PHP在后端,那么就用Ajax;仅供参考:HTML code
 How to determine whether a JSONObject contains a certain key in Java?
May 08, 2023 pm 12:25 PM
How to determine whether a JSONObject contains a certain key in Java?
May 08, 2023 pm 12:25 PM
Determine whether a KeyJSONObject exists in JSONObjectjsonObj=newJSONObject();jsonObj.put("version","1.0.0");//version number jsonObj.put("encoding","UTF-8");//encoding method Determine whether the vesion attribute exists in jsonObject jsonObj.has("version");//Return true to check whether the k exists in the json string
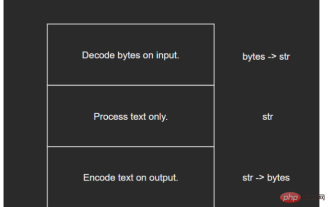 Python built-in type str source code analysis
May 09, 2023 pm 02:16 PM
Python built-in type str source code analysis
May 09, 2023 pm 02:16 PM
1The basic unit of Unicode computer storage is the byte, which is composed of 8 bits. Since English only consists of 26 letters plus a number of symbols, English characters can be stored directly in bytes. But other languages (such as Chinese, Japanese, Korean, etc.) have to use multiple bytes for encoding due to the large number of characters. With the spread of computer technology, non-Latin character encoding technology continues to develop, but there are still two major limitations: no multi-language support: the encoding scheme of one language cannot be used in another language and there is no unified standard: for example There are many encoding standards in Chinese such as GBK, GB2312, GB18030, etc. Since the encoding methods are not unified, developers need to convert back and forth between different encodings, and many errors will inevitably occur.




