linux ldap认证:windos 和 linux 下实现PHP和LDAP身份认证
我现在的老板曾要求我为企业内部互联网的Web服务提供一种标准的身份验证方法。我遇到的一个主要问题就是我们公司主要使用了两种平台:UNIX和Windows。所以,我的第一个想法并不很成功:它要求每个员工都使用UNIX或者Linux而放弃Windows。
我认为解决现在的UNIX/Windows问题的最好方法就是利用PHP的LDAP特性。由于LDAP服务器,要求我使用现有的系统,主要指的是一个巨大的Microsoft Exchange Server系统。我非常高兴使用Exchange,它很可靠,而且LDAP特性的使用和配置也极为简单。不过,请你注意:这套方案就身份验证角度来看并不是最安全的。如果有较高等级的安全需求,我强烈建议你采用LDAP和SSL。
从哪里开始学习
为了让你入门,我给出了一个PHP LDAP函数的清单并对函数的功能给以简要说明。然后,我将演示如何建立到LDAP服务器的连接并验证用户。为了代码简单起见,我将演示PHP连接的功能以及如何绑定到LDAP服务器。
一对绝配:PHP和LADP
下面是我在例子中将要使用的函数的清单。网上有相关资料。
ldap_connect—用来连接LDAP服务。
ldap_bind—用来绑定到特定的LDAP目录。
ldap_error—从LDAP服务器上获得错误信息。
ldap_search—用来开始搜索。
ldap_get_entries—从搜索结果中获得多个结果。
ldap_close—关闭LDAP连接。
现在我在例子中演示如何使用第一个函数(代码清单A)并适当介绍该函数的功能。
// LDAP variables
$ldap[‘user’] = ‘uname’;
$ldap[‘pass’] = ‘password’;
$ldap[‘host’] = ‘ldap.example.com’;
$ldap[‘port’] = 389;
$ldap[‘dn’] = ‘cn’.$ldap[‘user’].’,ou=Department,o=Company Name’;
$ldap[‘base’] = ‘’;
// connecting to ldap
$ldap[‘conn’] = ldap_connect( $ldap[‘host’], $ldap[‘port’] )
or die( “Could not connect to {$ldap[‘host’]}” );
?>
将会返回一个到LDAP服务器的连接(也称为资源,即resource)。ldap_connect函数有两个参数:主机(host)和端口。第一个参数:主机就是LDAP主机名称,第二个参数是LDAP运行的端口。默认情况下,LDAP使用的端口号为389。如果你需要到LDAP服务器的一个安全连接,你可以把参数host改为一个你可以访问的LDAP服务器的URL,如下所示:
$ldap[‘conn’] = ldap_connect( “ldaps://ldap.example.com” );
由于你指定了URL而不是服务器名称,在这种方法下,你就不需要使用端口参数了。需要牢记的一点就是确切名称需要与加密套接字协议层证书(the SSL certificate)对应。
// LDAP variables
$ldap[‘user’] = ‘uname’;
$ldap[‘pass’] = ‘password’;
$ldap[‘host’] = ‘ldap.example.com’;
$ldap[‘port’] = 389;
$ldap[‘dn’] = ‘cn’.$ldap[‘user’].’,ou=Department,o=Company Name’;
$ldap[‘base’] = ‘’;
// connecting to ldap
$ldap[‘conn’] = ldap_connect( $ldap[‘host’], $ldap[‘port’] )
or die( “Could not connect to {$ldap[‘host’]}” );
// binding to ldap
$ldap[‘bind’] = ldap_bind( $ldap[‘conn’], $ldap[‘dn’], $ldap[‘pass’] );
?>
演示了如何用用户名和口令来绑定到服务器。我创建了一个合适的域名(domain name ,DN)并用用户的口令来合法连接到LDAP。我们通过使用域名和口令就可以让LDAP服务器通过身份认证并允许绑定连接,这样我们就成功的绑定上了。ldap_bind的返回值是一个布尔类型。我们可以根据返回值判断用户的登录证书是否有效。当这个过程结束后,你就可以知道用户身份是否得到了认证。
如果发生了错误会怎样?调用ldap_error函数是判断发生了什么错误的好方法。ldap_error函数返回了一个字符串,其中包含了LDAP服务器发生的最后错误的信息。
在
// LDAP variables
$ldap[‘user’] = ‘uname’;
$ldap[‘pass’] = ‘password’;
$ldap[‘host’] = ‘ldap.example.com’;
$ldap[‘port’] = 389;
$ldap[‘dn’] = ‘cn’.$ldap[‘user’].’,ou=Department,o=Company Name’;
$ldap[‘base’] = ‘’;
// connecting to ldap
$ldap[‘conn’] = ldap_connect( $ldap[‘host’], $ldap[‘port’] )
or die( “Could not connect to server {$ldap[‘host’]} );
// binding to ldap
$ldap[‘bind’] = ldap_bind( $ldap[‘conn’], $ldap[‘dn’], $ldap[‘pass’] );
if( !$ldap[‘bind’] )
{
echo ldap_error( $ldap[‘conn’] );
exit;
}
?>
中,我向脚本中添加了ldap_error函数,如果绑定到LDAP服务器的用户身份没有得到确认,那么代码将退出运行。该函数返回一个字符串,该字符串包含了发送到LDAP服务器的最后一条指令产生的错误信息。如果你按给定用户名和口令的绑定没有成功登录,那么错误信息将包含这对无效的用户名和口令。
在我们的最后一个例子中
// LDAP variables
$ldap[‘user’] = ‘uname’;
$ldap[‘pass’] = ‘password’;
$ldap[‘host’] = ‘ldap.example.com’; 本文链接http://www.cxybl.com/html/wlbc/Php/20121126/34395.html

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1387
1387
 52
52
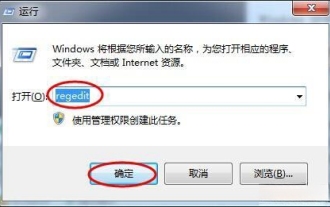 Windows 11 shutdown prompts task host window task host is executing the shutdown task solution
Feb 12, 2024 pm 12:40 PM
Windows 11 shutdown prompts task host window task host is executing the shutdown task solution
Feb 12, 2024 pm 12:40 PM
Recently, many Win11 users have reported that when shutting down, they are prompted that the taskhostwindow task host is executing the shutdown task. So what is going on? Users can enter the Desktop folder under the local registry editor, and then select AutoEndTasks in the right window to set it. Let this site carefully introduce to users the solution to this problem when shutting down. Windows 11 shutdown prompts that the taskhostwindow task host is executing the shutdown task. Solution 1. Use the key combination win key + r key, enter "regedit" and press Enter, as shown in the figure below. 2. Search for [HKEY
 How to check if aggregator host.exe is safe in Windows 11
Apr 13, 2023 pm 04:22 PM
How to check if aggregator host.exe is safe in Windows 11
Apr 13, 2023 pm 04:22 PM
When we launch Task Manager to terminate a task or stop an application, we usually find a large number of processes running. This is completely normal. However, sometimes we see programs that are using system resources that we are completely unaware of. One of these processes is the aggregator host.exe, which has been causing some confusion among users recently. Some of these processes may be legitimate Windows requirements, but others may be malicious programs running in the background and causing problems without the user's knowledge or consent. After we've seen the five ways you can launch Task Manager in Windows 11, we'll show you how to check if aggregator host.exe is safe or a virus. keep up
 What is the difference between master and host
Sep 28, 2023 pm 01:34 PM
What is the difference between master and host
Sep 28, 2023 pm 01:34 PM
The differences between master and host are: 1. Host can play the role of client or server, while master is the central server responsible for coordinating and managing other slave servers in a distributed system; 2. Host is an ordinary computer device, and master usually has Higher processing power and resources are used to process and distribute tasks, manage data, and maintain the stability of the entire system; 3. The host is a node in the network, and the master is the server that plays a core role in the distributed system.
 What to do if no route to host
Oct 07, 2023 am 10:50 AM
What to do if no route to host
Oct 07, 2023 am 10:50 AM
The solutions to "no route to host" include checking the network connection, checking the IP address and port, checking the firewall configuration, checking the routing configuration, checking the network device configuration, checking the network service status, checking the network configuration and contacting the network administrator. Detailed introduction: 1. Check the network connection to ensure that the network connection between the client and the target host is normal. You can try to test network connectivity through the ping command or other network tools, and check whether hardware devices such as network cables, wireless networks, and routers are working properly. Make sure the network connection is stable, etc.
 How to understand LDAP injection
May 22, 2023 pm 09:47 PM
How to understand LDAP injection
May 22, 2023 pm 09:47 PM
1. LDAP injection LDAP (Light Directory Access Portocol) is a lightweight directory access protocol based on the X.500 standard. It provides services and protocols for accessing directory databases. It is often used to form directory services with directory databases. The directory is a professional distributed database optimized for query, browsing and search. It organizes data in a tree structure, similar to the file directory in Linux/Unix systems. Data that is not modified frequently, such as public certificates, security keys, and company physical device information, is suitable for storage in the directory. LDAP can be understood as a search protocol, which is similar to SQL and has query syntax, but also has the risk of injection attacks. LDAP injection refers to the client
 How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
How to conduct range practice with bee-box LDAP injection
May 13, 2023 am 09:49 AM
If the essence of sql injection is to splice strings, then the essence of everything that can be injected is to splice strings. LDAP injection is no exception as a kind of injection. What is more interesting is that it is splicing parentheses (sql injection is also concatenates parentheses, but it is more conventional to say that it concatenates strings). In the environment configuration chapter, the configuration of the ldap environment in bee-box has been discussed in great detail. The shooting range practice chapter is more about the connection process between php and ldap, the introduction of the special functions used in the middle, and some techniques for splicing parentheses. Let’s first talk about the login process of the ldap shooting range in bwapp: First, this is an LDAP login interface, the URL is http://192.168.3.184/bW
 Where is the host file
Jan 04, 2021 am 11:25 AM
Where is the host file
Jan 04, 2021 am 11:25 AM
The host file is located under the path "C:\Windows\System32\drivers\etc"; the host file is a plain text file that can be opened with ordinary text editing software, such as Notepad; the function of the host file is to contain the IP address Mapping relationship with Host name.
 How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
How to configure the environment for bee-box LDAP injection
May 12, 2023 pm 08:37 PM
1. Overview According to my learning process, I must know what the model and vulnerability of my web attack are. Now I have encountered an unexpected situation. The first time I saw LDAP was during a penetration test in a state-owned enterprise. I found an unpopular one (authorized) and piqued my interest in it. The concept of LDAP: Full name: Lightweight Directory Access Protocol (Lightweight Directory Access Protocol), features: I won’t talk about the protocol, it’s too esoteric, it can be understood as a database for storing data, its special feature is that it is a tree A database in the form of a database. First, the name of the database is equivalent to the root of the tree (i.e. DB=dc), and then the process from the root to a leaf node is




