 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 How to prevent a website from being accessed by a malicious reverse proxy_PHP Tutorial
How to prevent a website from being accessed by a malicious reverse proxy_PHP Tutorial
How to prevent a website from being accessed by a malicious reverse proxy_PHP Tutorial
Recently, someone used small site data and reverse proxy technology to create a thief site. The user visited his URL, but the content data is actually mine. This is a malicious reverse proxy incident
What is a reverse proxy? Let’s first talk about the concept of forward agency: The forward agent, also known as the legendary agent, works like a springboard. To put it simply, I am a user and I cannot access a certain website, but I can access a proxy server. As for this proxy server, it can access the website that I cannot access, so I first connect to the proxy server and tell it that I need the content of the website that cannot be accessed. The proxy server will retrieve it and return it to me. From the website's perspective, there is only one record when the proxy server comes to retrieve the content. Sometimes it is not known that it is the user's request, and the user's information is also hidden. This depends on whether the proxy tells the website or not. The conclusion is that a forward proxy is a server between the client and the origin server. In order to obtain content from the origin server, the client sends a request to the proxy and specifies the target (origin server), and then the proxy sends the content to the origin server. Hands off the request and returns the obtained content to the client. The client must make some special settings to use the forward proxy. So what about the concept of reverse proxy? For example, a user visits the page http://www.nowamagic.net/librarys/veda, but www.nowamagic.net does not actually exist. It secretly retrieves it from another server and uses it as its own content. spit to the user. But users don't know this. This is normal. Users are generally stupid. The server corresponding to the domain name www.nowamagic.net mentioned here has a reverse proxy function. The conclusion is that a reverse proxy is just the opposite, it acts like the original server to the client, and the client does not need to make any special settings. The client sends a normal request to the content in the reverse proxy's namespace (name-space), and then the reverse proxy will determine where to forward the request (original server) and return the obtained content to the client, like these The content is its own original content. The Dangers of Malicious Reverse Proxies What are the dangers of a malicious reverse proxy on a website? Here are some examples: •First of all, it will definitely occupy server resources and affect the website opening speed. •Secondly, if someone else steals your website data through a proxy, for users and less intelligent search engines, it is equivalent to building a site exactly like yours. Then it is very likely that your site will be entered into the search engine sandbox, or even Demoted. •If the maliciously proxied page also has your affiliate advertisement (such as Adsense), this is very dangerous. If someone clicks on the above advertisement, it is easy to be banned by Adsense. •There are many dangers, readers can figure it out on their own... js level solution The code is as follows: The script is very simple. If the URL in the address bar is not one of nowamagic.net and www.nowamagic.net, then redirect the address bar to http://www.nowamagic.net/. This code can also prevent people from using reverse proxy technology to "fake" a website that is exactly like your own. Off topic: How to prevent websites from being embedded by iframes. Some people use iframes to create a framework and embed our website into it. When visitors come to browse, it seems like they are browsing their own website. So how to solve it? The following methods can be broken: The code is as follows: PHP level solution Although the js-level solution can make the malicious proxy page jump back, it is not very friendly to search engines. The following is the server-side (PHP) solution. The code is relatively simple, so I won’t go into details. The code is as follows: $proxy_rs = $this -> proxy_filter(); if( $proxy_rs != 'nowamagic.net' || $proxy_rs != 'www.nowamagic.net' ) { echo 'Illegal reverse proxy access'; //header('Location: http://www.nowamagic.net/'); exit; } public function proxy_filter() { /* $svrUrl = 'http://' . $_SERVER['SERVER_NAME'].$_SERVER["PHP_SELF"]; if (!empty($_SERVER["QUERY_STRING"])) { $svrUrl .= "?".$_SERVER["QUERY_STRING"]; } return $svrUrl; */ return $_SERVER['SERVER_NAME']; } htaccess level solution .htaccess The code is as follows: RewriteEngineOn RewriteBase/ php_value auto_append_file proxy.php proxy.php The code is as follows: Due to the particularity of my website, I have not tested this method, but this method is commonly used on the Internet. Apache httpd.conf level solution I haven't figured out how to ban this on Apache. Nginx can do it, but I use Apache. If you know, please tell me ~
Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1371
1371
 52
52
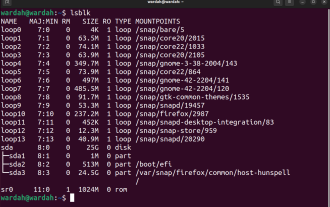 Use ddrescue to recover data on Linux
Mar 20, 2024 pm 01:37 PM
Use ddrescue to recover data on Linux
Mar 20, 2024 pm 01:37 PM
DDREASE is a tool for recovering data from file or block devices such as hard drives, SSDs, RAM disks, CDs, DVDs and USB storage devices. It copies data from one block device to another, leaving corrupted data blocks behind and moving only good data blocks. ddreasue is a powerful recovery tool that is fully automated as it does not require any interference during recovery operations. Additionally, thanks to the ddasue map file, it can be stopped and resumed at any time. Other key features of DDREASE are as follows: It does not overwrite recovered data but fills the gaps in case of iterative recovery. However, it can be truncated if the tool is instructed to do so explicitly. Recover data from multiple files or blocks to a single
 Open source! Beyond ZoeDepth! DepthFM: Fast and accurate monocular depth estimation!
Apr 03, 2024 pm 12:04 PM
Open source! Beyond ZoeDepth! DepthFM: Fast and accurate monocular depth estimation!
Apr 03, 2024 pm 12:04 PM
0.What does this article do? We propose DepthFM: a versatile and fast state-of-the-art generative monocular depth estimation model. In addition to traditional depth estimation tasks, DepthFM also demonstrates state-of-the-art capabilities in downstream tasks such as depth inpainting. DepthFM is efficient and can synthesize depth maps within a few inference steps. Let’s read about this work together ~ 1. Paper information title: DepthFM: FastMonocularDepthEstimationwithFlowMatching Author: MingGui, JohannesS.Fischer, UlrichPrestel, PingchuanMa, Dmytr
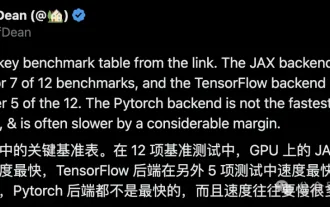 Google is ecstatic: JAX performance surpasses Pytorch and TensorFlow! It may become the fastest choice for GPU inference training
Apr 01, 2024 pm 07:46 PM
Google is ecstatic: JAX performance surpasses Pytorch and TensorFlow! It may become the fastest choice for GPU inference training
Apr 01, 2024 pm 07:46 PM
The performance of JAX, promoted by Google, has surpassed that of Pytorch and TensorFlow in recent benchmark tests, ranking first in 7 indicators. And the test was not done on the TPU with the best JAX performance. Although among developers, Pytorch is still more popular than Tensorflow. But in the future, perhaps more large models will be trained and run based on the JAX platform. Models Recently, the Keras team benchmarked three backends (TensorFlow, JAX, PyTorch) with the native PyTorch implementation and Keras2 with TensorFlow. First, they select a set of mainstream
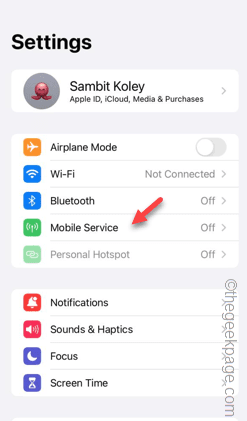 Slow Cellular Data Internet Speeds on iPhone: Fixes
May 03, 2024 pm 09:01 PM
Slow Cellular Data Internet Speeds on iPhone: Fixes
May 03, 2024 pm 09:01 PM
Facing lag, slow mobile data connection on iPhone? Typically, the strength of cellular internet on your phone depends on several factors such as region, cellular network type, roaming type, etc. There are some things you can do to get a faster, more reliable cellular Internet connection. Fix 1 – Force Restart iPhone Sometimes, force restarting your device just resets a lot of things, including the cellular connection. Step 1 – Just press the volume up key once and release. Next, press the Volume Down key and release it again. Step 2 – The next part of the process is to hold the button on the right side. Let the iPhone finish restarting. Enable cellular data and check network speed. Check again Fix 2 – Change data mode While 5G offers better network speeds, it works better when the signal is weaker
 The vitality of super intelligence awakens! But with the arrival of self-updating AI, mothers no longer have to worry about data bottlenecks
Apr 29, 2024 pm 06:55 PM
The vitality of super intelligence awakens! But with the arrival of self-updating AI, mothers no longer have to worry about data bottlenecks
Apr 29, 2024 pm 06:55 PM
I cry to death. The world is madly building big models. The data on the Internet is not enough. It is not enough at all. The training model looks like "The Hunger Games", and AI researchers around the world are worrying about how to feed these data voracious eaters. This problem is particularly prominent in multi-modal tasks. At a time when nothing could be done, a start-up team from the Department of Renmin University of China used its own new model to become the first in China to make "model-generated data feed itself" a reality. Moreover, it is a two-pronged approach on the understanding side and the generation side. Both sides can generate high-quality, multi-modal new data and provide data feedback to the model itself. What is a model? Awaker 1.0, a large multi-modal model that just appeared on the Zhongguancun Forum. Who is the team? Sophon engine. Founded by Gao Yizhao, a doctoral student at Renmin University’s Hillhouse School of Artificial Intelligence.
 The U.S. Air Force showcases its first AI fighter jet with high profile! The minister personally conducted the test drive without interfering during the whole process, and 100,000 lines of code were tested for 21 times.
May 07, 2024 pm 05:00 PM
The U.S. Air Force showcases its first AI fighter jet with high profile! The minister personally conducted the test drive without interfering during the whole process, and 100,000 lines of code were tested for 21 times.
May 07, 2024 pm 05:00 PM
Recently, the military circle has been overwhelmed by the news: US military fighter jets can now complete fully automatic air combat using AI. Yes, just recently, the US military’s AI fighter jet was made public for the first time and the mystery was unveiled. The full name of this fighter is the Variable Stability Simulator Test Aircraft (VISTA). It was personally flown by the Secretary of the US Air Force to simulate a one-on-one air battle. On May 2, U.S. Air Force Secretary Frank Kendall took off in an X-62AVISTA at Edwards Air Force Base. Note that during the one-hour flight, all flight actions were completed autonomously by AI! Kendall said - "For the past few decades, we have been thinking about the unlimited potential of autonomous air-to-air combat, but it has always seemed out of reach." However now,
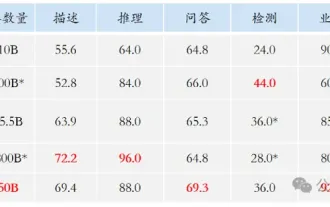
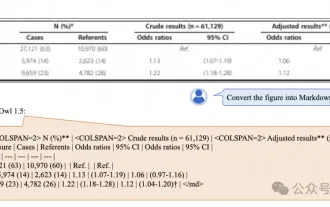 Alibaba 7B multi-modal document understanding large model wins new SOTA
Apr 02, 2024 am 11:31 AM
Alibaba 7B multi-modal document understanding large model wins new SOTA
Apr 02, 2024 am 11:31 AM
New SOTA for multimodal document understanding capabilities! Alibaba's mPLUG team released the latest open source work mPLUG-DocOwl1.5, which proposed a series of solutions to address the four major challenges of high-resolution image text recognition, general document structure understanding, instruction following, and introduction of external knowledge. Without further ado, let’s look at the effects first. One-click recognition and conversion of charts with complex structures into Markdown format: Charts of different styles are available: More detailed text recognition and positioning can also be easily handled: Detailed explanations of document understanding can also be given: You know, "Document Understanding" is currently An important scenario for the implementation of large language models. There are many products on the market to assist document reading. Some of them mainly use OCR systems for text recognition and cooperate with LLM for text processing.
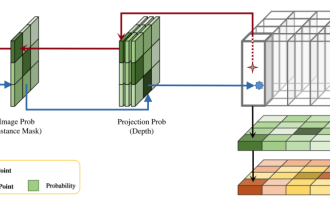 DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
DualBEV: significantly surpassing BEVFormer and BEVDet4D, open the book!
Mar 21, 2024 pm 05:21 PM
This paper explores the problem of accurately detecting objects from different viewing angles (such as perspective and bird's-eye view) in autonomous driving, especially how to effectively transform features from perspective (PV) to bird's-eye view (BEV) space. Transformation is implemented via the Visual Transformation (VT) module. Existing methods are broadly divided into two strategies: 2D to 3D and 3D to 2D conversion. 2D-to-3D methods improve dense 2D features by predicting depth probabilities, but the inherent uncertainty of depth predictions, especially in distant regions, may introduce inaccuracies. While 3D to 2D methods usually use 3D queries to sample 2D features and learn the attention weights of the correspondence between 3D and 2D features through a Transformer, which increases the computational and deployment time.



