 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Require password to log in to phpmyadmin setup method_PHP tutorial
Require password to log in to phpmyadmin setup method_PHP tutorial
Require password to log in to phpmyadmin setup method_PHP tutorial
Find the config.inc.php tutorial
1. Use cookie authorization mode to change 'auth_type' to 'cookie', and then modify 'blowfish_secret' to use an arbitrary string as the cookie encryption string. If there is no encryption key, the system will display "The configuration file now requires top secret Phrase password (blowfish_secret) ", the configuration file is as follows: $cfg['Servers'][$i]['auth_type'] = 'cookie'; $cfg['blowfish_secret'] = '44e2f5aece2855.93921574'; After modification , enter the login window
4
Web login page in http authorization mode
2. Use config authorization mode
config requires these parameters:
$cfg['Servers'][$i]['auth_type'] = 'config';
//Authorization mode $cfg['Servers'][$i]['user'] = 'root';
//mysql tutorial login user $cfg['Servers'][$i]['password'] = '12345';
//mysql login user password
$cfg['Servers'][$i]['auth_type'] = 'cookie'; // Authentication method (config, http or cookie based)?
Note, it’s not http but cookie! ! !
$cfg['Servers'][$i]['auth_type'] = 'http';
Note: If the mysql server uses version 4.1 or above, and the client connection uses mysql 4.1 or lower, be sure to use the OLD_PASSWORD function when setting the password for the user, for example:
mysql > SET PASSWORD = OLD_PASSWORD('12345')
mysql > /G
Appendix: (The following content is written by myself) In addition to the above three methods that come with phpmyadmin, you can also use apache configuration to restrict login. Place an .htaccess file in the phpmyadmin directory and specify the password record file to be used. Then use htpasswd to generate a password and save it in the password record file (the content of the file is encrypted, use the method htpasswd /etc/php_passwd username).
Contents in httpd.conf: phpmyadmin's directory"> AllowOverride AuthConfig
Contents of .htaccess file
authtype basic authuserfile /etc/php_passwd authname information require valid-user
We can see that the content in the /etc/php_passwd file is similar to this:
username:2Y2CD6nfJuwL6
More detailed tutorial
Find $cfg['servers'][$i]['user'] = ' ', add 'root' to ' '
Find $cfg['servers'][$i]['password'] = ' ', add '123456' to ' ';
The modification in these two places is to add the user name and password of the Mysql just installed. Readers can modify it by themselves.
This is the configuration file and needs to be modified.
config.inc.php
// vim: expandtab sw=4 ts=4 sts=4:
* phpMyAdmin sample configuration, you can use it as base for
* This is needed for cookie based authentication to encrypt password in
* Servers configuration
* First server
* End of servers configuration
* Directories for saving/loading files from server
* manual configuration. For easier setup you can use scripts/setup.php
*
* All directives are explained in Documentation.html and on phpMyAdmin
* wiki
*/
/*
* cookie
*/
$cfg['blowfish_secret'] = 'afafafaf'; /* YOU MUST FILL IN THIS FOR COOKIE AUTH! */
*/
$i = 0;
*/
$i++;
/* Authentication type */
$cfg['Servers'][$i]['auth_type'] = 'cookie';
/* Server parameters */
$cfg['Servers'][$i]['host'] = 'localhost';
$cfg['Servers'][$i]['connect_type'] = 'tcp';
$cfg['Servers'][$i]['compress'] = false;
/* Select mysqli if your server has it */
$cfg['Servers'][$i]['extension'] = 'mysql';
/* User for advanced features */
$cfg['Servers'][$i]['controluser'] = ''; //Username
$cfg['Servers'][$i]['controlpass'] = '';//Password
/* Advanced phpMyAdmin features */
// $cfg['Servers'][$i]['pmadb'] = 'phpmyadmin';
// $cfg['Servers'][$i]['bookmarktable'] = 'pma_bookmark';
// $cfg['Servers'][$i]['relation'] = 'pma_relation';
// $cfg['Servers'][$i]['table_info'] = 'pma_table_info';
// $cfg['Servers'][$i]['table_coords'] = 'pma_table_coords';
// $cfg['Servers'][$i]['pdf_pages'] = 'pma_pdf_pages';
// $cfg['Servers'][$i]['column_info'] = 'pma_column_info';
// $cfg['Servers'][$i]['history'] = 'pma_history';
// $cfg['Servers'][$i]['designer_coords'] = 'pma_designer_coords';
*/
*/
$cfg['UploadDir'] = '';
$cfg['SaveDir'] = '';

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 How to recover deleted contacts on WeChat (simple tutorial tells you how to recover deleted contacts)
May 01, 2024 pm 12:01 PM
How to recover deleted contacts on WeChat (simple tutorial tells you how to recover deleted contacts)
May 01, 2024 pm 12:01 PM
Unfortunately, people often delete certain contacts accidentally for some reasons. WeChat is a widely used social software. To help users solve this problem, this article will introduce how to retrieve deleted contacts in a simple way. 1. Understand the WeChat contact deletion mechanism. This provides us with the possibility to retrieve deleted contacts. The contact deletion mechanism in WeChat removes them from the address book, but does not delete them completely. 2. Use WeChat’s built-in “Contact Book Recovery” function. WeChat provides “Contact Book Recovery” to save time and energy. Users can quickly retrieve previously deleted contacts through this function. 3. Enter the WeChat settings page and click the lower right corner, open the WeChat application "Me" and click the settings icon in the upper right corner to enter the settings page.
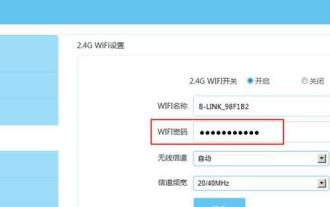 How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
How to set router WiFi password using mobile phone (using mobile phone as tool)
Apr 24, 2024 pm 06:04 PM
Wireless networks have become an indispensable part of people's lives in today's digital world. Protecting the security of personal wireless networks is particularly important, however. Setting a strong password is key to ensuring that your WiFi network cannot be hacked by others. To ensure your network security, this article will introduce in detail how to use your mobile phone to change the router WiFi password. 1. Open the router management page - Open the router management page in the mobile browser and enter the router's default IP address. 2. Enter the administrator username and password - To gain access, enter the correct administrator username and password in the login page. 3. Navigate to the wireless settings page - find and click to enter the wireless settings page, in the router management page. 4. Find the current Wi
 How to set font size on mobile phone (easily adjust font size on mobile phone)
May 07, 2024 pm 03:34 PM
How to set font size on mobile phone (easily adjust font size on mobile phone)
May 07, 2024 pm 03:34 PM
Setting font size has become an important personalization requirement as mobile phones become an important tool in people's daily lives. In order to meet the needs of different users, this article will introduce how to improve the mobile phone use experience and adjust the font size of the mobile phone through simple operations. Why do you need to adjust the font size of your mobile phone - Adjusting the font size can make the text clearer and easier to read - Suitable for the reading needs of users of different ages - Convenient for users with poor vision to use the font size setting function of the mobile phone system - How to enter the system settings interface - In Find and enter the "Display" option in the settings interface - find the "Font Size" option and adjust it. Adjust the font size with a third-party application - download and install an application that supports font size adjustment - open the application and enter the relevant settings interface - according to the individual
 The secret of hatching mobile dragon eggs is revealed (step by step to teach you how to successfully hatch mobile dragon eggs)
May 04, 2024 pm 06:01 PM
The secret of hatching mobile dragon eggs is revealed (step by step to teach you how to successfully hatch mobile dragon eggs)
May 04, 2024 pm 06:01 PM
Mobile games have become an integral part of people's lives with the development of technology. It has attracted the attention of many players with its cute dragon egg image and interesting hatching process, and one of the games that has attracted much attention is the mobile version of Dragon Egg. To help players better cultivate and grow their own dragons in the game, this article will introduce to you how to hatch dragon eggs in the mobile version. 1. Choose the appropriate type of dragon egg. Players need to carefully choose the type of dragon egg that they like and suit themselves, based on the different types of dragon egg attributes and abilities provided in the game. 2. Upgrade the level of the incubation machine. Players need to improve the level of the incubation machine by completing tasks and collecting props. The level of the incubation machine determines the hatching speed and hatching success rate. 3. Collect the resources required for hatching. Players need to be in the game
 BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
MetaMask (also called Little Fox Wallet in Chinese) is a free and well-received encryption wallet software. Currently, BTCC supports binding to the MetaMask wallet. After binding, you can use the MetaMask wallet to quickly log in, store value, buy coins, etc., and you can also get 20 USDT trial bonus for the first time binding. In the BTCCMetaMask wallet tutorial, we will introduce in detail how to register and use MetaMask, and how to bind and use the Little Fox wallet in BTCC. What is MetaMask wallet? With over 30 million users, MetaMask Little Fox Wallet is one of the most popular cryptocurrency wallets today. It is free to use and can be installed on the network as an extension
 In summer, you must try shooting a rainbow
Jul 21, 2024 pm 05:16 PM
In summer, you must try shooting a rainbow
Jul 21, 2024 pm 05:16 PM
After rain in summer, you can often see a beautiful and magical special weather scene - rainbow. This is also a rare scene that can be encountered in photography, and it is very photogenic. There are several conditions for a rainbow to appear: first, there are enough water droplets in the air, and second, the sun shines at a low angle. Therefore, it is easiest to see a rainbow in the afternoon after the rain has cleared up. However, the formation of a rainbow is greatly affected by weather, light and other conditions, so it generally only lasts for a short period of time, and the best viewing and shooting time is even shorter. So when you encounter a rainbow, how can you properly record it and photograph it with quality? 1. Look for rainbows. In addition to the conditions mentioned above, rainbows usually appear in the direction of sunlight, that is, if the sun shines from west to east, rainbows are more likely to appear in the east.
 Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Tutorial on changing wifi password on mobile phone (simple operation)
Apr 26, 2024 pm 06:25 PM
Wireless networks have become an indispensable part of our lives with the rapid development of the Internet. In order to protect personal information and network security, it is very important to change your wifi password regularly, however. To help you better protect your home network security, this article will introduce you to a detailed tutorial on how to use your mobile phone to change your WiFi password. 1. Understand the importance of WiFi passwords. WiFi passwords are the first line of defense to protect personal information and network security. In the Internet age, understanding its importance can better understand why passwords need to be changed regularly. 2. Confirm that the phone is connected to wifi. First, make sure that the phone is connected to the wifi network whose password you want to change before changing the wifi password. 3. Open the phone’s settings menu and enter the phone’s settings menu.
 What should I do if navicat cannot connect?
Apr 23, 2024 am 10:00 AM
What should I do if navicat cannot connect?
Apr 23, 2024 am 10:00 AM
When Navicat cannot connect, you can try the following solutions in order: Check whether the connection information is correct, such as database name, host name, port number, user name and password. Make sure the database is up and running. Check the firewall rules to confirm that Navicat and related services are not blocked. Try using the ping command to test your network connection. Update Navicat client software to the latest version. Check the server logs for error messages related to failed connections. Try connecting using other database tools to troubleshoot Navicat-specific issues.



