 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Detailed explanation of the use of regular expressions (2)_PHP tutorial
Detailed explanation of the use of regular expressions (2)_PHP tutorial
Detailed explanation of the use of regular expressions (2)_PHP tutorial
After having a more comprehensive understanding of regular expressions, let’s take a look at how to use regular expressions in Perl, PHP, and JavaScript/" target="_blank">JavaScript.
Usually, the format of regular expressions in Perl is as follows:
Operator / regular-expression / string-to-replace / modifiers
The operator item can be m or s, which represent matching operation and substitution operation respectively.
Among them, the regular expression item is the pattern to be matched or replaced, which can be composed of any characters, metacharacters, or locators. The replacement string item is the string that replaces the found pattern matching object when using the s operator. The last parameter is used to control different matching or replacement methods. For example:
s/geed/good/
Will find the first occurrence of the geed string in the target object and replace it with good. If we want to perform multiple search-replace operations in the global scope of the target object, we can use the parameter "g", that is, s/love/lust/g.
In addition, if we do not need to limit the matching case, we can use the parameter "i". For example,
m/JewEL/i
The above regular expression will match jewel, Jewel, or JEWEL in the target object.
In Perl, use the special operator "=~" to specify the matching object of the regular expression. For example:
$flag =~ s/abc/ABC/
The above regular expression will replace the string abc in the variable $flag with ABC.
Next, we will add regular expressions to the Perl program to verify the validity of the user's email address format. The code is as follows:
#!/usr/bin/perl
# get input
print “Whats your email address?
”;
$email = $#@60;STDIN$#@62;;
chomp($email);
# match and display result
if($email =~ /^([ a-zA-Z0-9_-])+@([a-zA-Z0-9_-])+(.[a-zA-Z0-9_-])+/)
{
print( "Your email address is correct!
”);
}
else
{
print(“Please try again!
”);
}
If the user prefers PHP, the ereg() function can be used for pattern matching operations. The usage format of the ereg() function is as follows:
ereg(pattern, string)
Among them, pattern represents the pattern of the regular expression, and string is the target object for performing the search and replace operation. The same is to verify the email address. The program code written in PHP is as follows:
$#@60;?php
if (ereg(“^([a-zA-Z0-9_ +@([a-zA-Z0-9_-])+(.[a-zA- Z0-9_-])+”,$email))
{ echo “Your email address is correct!”;}
else
{ echo “Please try again!”;}
?$ #@62;
Finally, let’s take a look at JavaScript/" target="_blank">JavaScript. JavaScript/" target="_blank">JavaScript 1.2 comes with a powerful RegExp() object. It can be used to perform regular expression matching operations. The test() method can check whether the target object contains a matching pattern and return true or false accordingly.
$#@60;html$#@62;
$#@60;head$#@62;
$#@60;script language="Javascript1.2"$#@62;
$#@60;!-- start hiding
function verifyAddress(obj)
{
var email = obj.email.value;
var pattern = /^([a-zA- Z0-9_-])+@([a-zA-Z0-9_-])+(.[a-zA-Z0-9_-])+/;
flag = pattern.test(email);
if(flag)
{
alert(“Your email address is correct!”);
return true; alert(“Please try again!");
return false;
}
}
// stop hiding --$#@62;
$#@60;/script$#@62;
$#@60;/head$#@62;
$#@60;body$#@62;
$#@60;form onSubmit="return verifyAddress(this);"$#@ 62;
$#@60;input name="email" type="text"$#@62;
$#@60;input type="submit"$#@62;
$# @60;/form$#@62;
$#@60;/body$#@62;
$#@60;/html$#@62;
www.bkjia.com

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1664
1664
 14
14
 1423
1423
 52
52
 1317
1317
 25
25
 1268
1268
 29
29
 1242
1242
 24
24
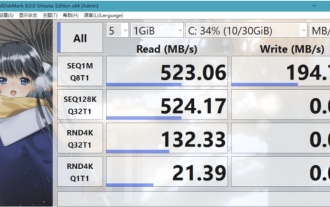 What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
What software is crystaldiskmark? -How to use crystaldiskmark?
Mar 18, 2024 pm 02:58 PM
CrystalDiskMark is a small HDD benchmark tool for hard drives that quickly measures sequential and random read/write speeds. Next, let the editor introduce CrystalDiskMark to you and how to use crystaldiskmark~ 1. Introduction to CrystalDiskMark CrystalDiskMark is a widely used disk performance testing tool used to evaluate the read and write speed and performance of mechanical hard drives and solid-state drives (SSD). Random I/O performance. It is a free Windows application and provides a user-friendly interface and various test modes to evaluate different aspects of hard drive performance and is widely used in hardware reviews
 How to download foobar2000? -How to use foobar2000
Mar 18, 2024 am 10:58 AM
How to download foobar2000? -How to use foobar2000
Mar 18, 2024 am 10:58 AM
foobar2000 is a software that can listen to music resources at any time. It brings you all kinds of music with lossless sound quality. The enhanced version of the music player allows you to get a more comprehensive and comfortable music experience. Its design concept is to play the advanced audio on the computer The device is transplanted to mobile phones to provide a more convenient and efficient music playback experience. The interface design is simple, clear and easy to use. It adopts a minimalist design style without too many decorations and cumbersome operations to get started quickly. It also supports a variety of skins and Theme, personalize settings according to your own preferences, and create an exclusive music player that supports the playback of multiple audio formats. It also supports the audio gain function to adjust the volume according to your own hearing conditions to avoid hearing damage caused by excessive volume. Next, let me help you
 BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
BTCC tutorial: How to bind and use MetaMask wallet on BTCC exchange?
Apr 26, 2024 am 09:40 AM
MetaMask (also called Little Fox Wallet in Chinese) is a free and well-received encryption wallet software. Currently, BTCC supports binding to the MetaMask wallet. After binding, you can use the MetaMask wallet to quickly log in, store value, buy coins, etc., and you can also get 20 USDT trial bonus for the first time binding. In the BTCCMetaMask wallet tutorial, we will introduce in detail how to register and use MetaMask, and how to bind and use the Little Fox wallet in BTCC. What is MetaMask wallet? With over 30 million users, MetaMask Little Fox Wallet is one of the most popular cryptocurrency wallets today. It is free to use and can be installed on the network as an extension
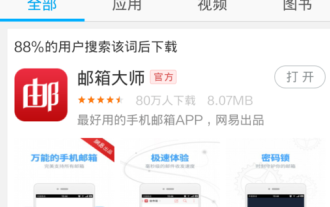 How to use NetEase Mailbox Master
Mar 27, 2024 pm 05:32 PM
How to use NetEase Mailbox Master
Mar 27, 2024 pm 05:32 PM
NetEase Mailbox, as an email address widely used by Chinese netizens, has always won the trust of users with its stable and efficient services. NetEase Mailbox Master is an email software specially created for mobile phone users. It greatly simplifies the process of sending and receiving emails and makes our email processing more convenient. So how to use NetEase Mailbox Master, and what specific functions it has. Below, the editor of this site will give you a detailed introduction, hoping to help you! First, you can search and download the NetEase Mailbox Master app in the mobile app store. Search for "NetEase Mailbox Master" in App Store or Baidu Mobile Assistant, and then follow the prompts to install it. After the download and installation is completed, we open the NetEase email account and log in. The login interface is as shown below
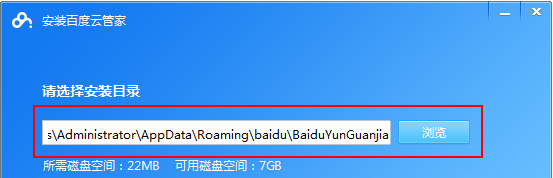 How to use Baidu Netdisk app
Mar 27, 2024 pm 06:46 PM
How to use Baidu Netdisk app
Mar 27, 2024 pm 06:46 PM
Cloud storage has become an indispensable part of our daily life and work nowadays. As one of the leading cloud storage services in China, Baidu Netdisk has won the favor of a large number of users with its powerful storage functions, efficient transmission speed and convenient operation experience. And whether you want to back up important files, share information, watch videos online, or listen to music, Baidu Cloud Disk can meet your needs. However, many users may not understand the specific use method of Baidu Netdisk app, so this tutorial will introduce in detail how to use Baidu Netdisk app. Users who are still confused can follow this article to learn more. ! How to use Baidu Cloud Network Disk: 1. Installation First, when downloading and installing Baidu Cloud software, please select the custom installation option.
 Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Detailed explanation of obtaining administrator rights in Win11
Mar 08, 2024 pm 03:06 PM
Windows operating system is one of the most popular operating systems in the world, and its new version Win11 has attracted much attention. In the Win11 system, obtaining administrator rights is an important operation. Administrator rights allow users to perform more operations and settings on the system. This article will introduce in detail how to obtain administrator permissions in Win11 system and how to effectively manage permissions. In the Win11 system, administrator rights are divided into two types: local administrator and domain administrator. A local administrator has full administrative rights to the local computer
 Teach you how to use the new advanced features of iOS 17.4 'Stolen Device Protection'
Mar 10, 2024 pm 04:34 PM
Teach you how to use the new advanced features of iOS 17.4 'Stolen Device Protection'
Mar 10, 2024 pm 04:34 PM
Apple rolled out the iOS 17.4 update on Tuesday, bringing a slew of new features and fixes to iPhones. The update includes new emojis, and EU users will also be able to download them from other app stores. In addition, the update also strengthens the control of iPhone security and introduces more "Stolen Device Protection" setting options to provide users with more choices and protection. "iOS17.3 introduces the "Stolen Device Protection" function for the first time, adding extra security to users' sensitive information. When the user is away from home and other familiar places, this function requires the user to enter biometric information for the first time, and after one hour You must enter information again to access and change certain data, such as changing your Apple ID password or turning off stolen device protection.
 Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in Oracle SQL
Mar 10, 2024 am 09:51 AM
Detailed explanation of division operation in OracleSQL In OracleSQL, division operation is a common and important mathematical operation, used to calculate the result of dividing two numbers. Division is often used in database queries, so understanding the division operation and its usage in OracleSQL is one of the essential skills for database developers. This article will discuss the relevant knowledge of division operations in OracleSQL in detail and provide specific code examples for readers' reference. 1. Division operation in OracleSQL



