 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 PPC has solved the Discuz!7.1 and 7.2 remote execution vulnerability_PHP tutorial
PPC has solved the Discuz!7.1 and 7.2 remote execution vulnerability_PHP tutorial
PPC has solved the Discuz!7.1 and 7.2 remote execution vulnerability_PHP tutorial
On the afternoon of January 6th, online release based on Discuz! 7.1&7.2 vulnerabilities and related attack methods. In response to this, PHPChina urgently contacted the DZ R&D department and made relevant patches for the PHPChina official forum program in the shortest possible time to ensure the normal use and safe operation of members in the PHPChina forum. Thank you for your concern and support for PHPChina. We will always adhere to the user-oriented principle and provide you with a safer and more convenient learning and communication environment. The following is the relevant introduction:
First of all, the vulnerability was transmitted from the t00ls core group. xhming read it first, and then I read it later. What was read was code execution. At 11 on the night of January 5 At around 1 o'clock, at the request of the core group of hackers, xhming gave me a POC and I gave me an exp. They found the same problem. As of around 2 o'clock in the night, I was offline. Only a few people in the t00ls core group knew the exp I gave, but I never expected that after half a day, the exp would be everywhere, and it was indeed from the version I had yesterday.
It is not difficult to imagine the speed at which exp spreads. A and B have a good relationship, and A sends it to B; B and C are good friends, and B sends it to C... There are always people who can't bear it and leak some rumors. , so everyone got one. The most unbearable thing is that some SBs are hawking in the group; I really don’t want to say anything, when will it be your turn to hawk? People's hearts are not ancient, so if you have any in the future, you should keep it to yourself.
I told Saiy about the vulnerability in the morning, and the official DZ patch will be out soon.
Related reading: Kangsheng Chuangxiang releases Discuz!7.2 patch 20100110
Special note: The $scriptlang array that generates the vulnerability has been initialized after the plug-in is installed, so users who have installed the plug-in are not affected.
Vulnerability introduction:
Discuz! The parameters executed in eval in the showmessage function in the new versions 7.1 and 7.2 are not initialized and can be submitted arbitrarily, so that any PHP command can be executed.
Vulnerability analysis:
Let’s analyze this remote code execution vulnerability. This problem is really serious. You can directly write the shell:
1. The vulnerability comes from the showmessage function:
Copy to Clipboard Quoted content: [www.bkjia.com]
function showmessage($message, $url_forward = '', $extra = '', $forwardtype = 0) {
Quoted content: [www.bkjia.com]
function showmessage($message, $url_forward = '', $extra = '', $forwardtype = 0) { extract($GLOBALS, EXTR_SKIP);//Dangerous usage, uninitialized variables can be brought directly into the function , directly caused the problem, from www.oldjun.com
global $hookscriptmessage, $extrahead, $discuz_uid, $discuz_action, $debuginfo, $seccode, $seccodestatus, $fid, $tid, $charset, $show_message, $inajax, $_DCACHE, $advlist;
define('CACHE_FORBIDDEN', TRUE);
$hookscriptmessage = $show_message = $message;$messagehandle = 0;
$msgforward = unserialize($_DCACHE[' settings']['msgforward']);
$refreshtime = intval($msgforward['refreshtime']);
$refreshtime = empty($forwardtype) ? $refreshtime : ($refreshtime ? $refreshtime : 3 );
$msgforward['refreshtime'] = $refreshtime * 1000;
$url_forward = empty($url_forward) ? '' : (empty($_DCOOKIE['sid']) && $transsidstatus ? transsid( $url_forward) : $url_forward);
$seccodecheck = $seccodestatus & 2;
if($_DCACHE['settings']['funcsiteid'] && $_DCACHE['settings']['funckey'] && $funcstatinfo && !IS_ROBOT) {
$statlogfile = DISCUZ_ROOT.'./forumdata/funcstat.log';
if($fp = @fopen($statlogfile, 'a')) {
@flock ($fp, 2);
if(is_array($funcstatinfo)) {
$funcstatinfo = array_unique($funcstatinfo);
foreach($funcstatinfo as $funcinfo) {
fwrite($fp , funcstat_query($funcinfo, $message)."n");
}
} else {
fwrite($fp, funcstat_query($funcstatinfo, $message)."n");
}
fclose($fp);
$funcstatinfo = $GLOBALS['funcstatinfo'] = '';
}
}
if(!defined('STAT_DISABLED') && STAT_ID > 0 && !IS_ROBOT) {
write_statlog($message);
}
if($url_forward && (!empty($quickforward) || empty($inajax) && $ msgforward['quick'] && $msgforward['messages'] && @in_array($message, $msgforward['messages']))) {
updatesession();
dheader("location: ".str_replace ('&', '&', $url_forward));
}
if(!empty($infloat)) {
if($extra) {
$messagehandle = $extra;
}
$extra = '';
}
if(in_array($extra, array('HALTED', 'NOPERM'))) {
$discuz_action = 254;
} else {
$discuz_action = 255;
}
include language('messages');
$vars = explode(':', $message);// Just include:
if(count($vars) == 2 && isset($scriptlang[$vars[0]][$vars[1]])) {//Two numbers are enough, use :Split
eval("$show_message = "".str_replace('"', '"', $scriptlang[$vars[0]][$vars[1]])."";");// $scriptlang is not initialized and can be customized, from www.oldjun.com
} elseif(isset($language[$message])) {
$pre = $inajax ? 'ajax_' : '';
eval("$show_message = "".(isset($language[$pre.$message]) ? $language[$pre.$message] : $language[$message])."";");
unset($pre);
}
......
}
- Total 2 pages:
- Previous page
- 1
- 2
- Next page

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1386
1386
 52
52
 Five tips to teach you how to solve the problem of Black Shark phone not turning on!
Mar 24, 2024 pm 12:27 PM
Five tips to teach you how to solve the problem of Black Shark phone not turning on!
Mar 24, 2024 pm 12:27 PM
As smartphone technology continues to develop, mobile phones play an increasingly important role in our daily lives. As a flagship phone focusing on gaming performance, the Black Shark phone is highly favored by players. However, sometimes we also face the situation that the Black Shark phone cannot be turned on. At this time, we need to take some measures to solve this problem. Next, let us share five tips to teach you how to solve the problem of Black Shark phone not turning on: Step 1: Check the battery power. First, make sure your Black Shark phone has enough power. It may be because the phone battery is exhausted
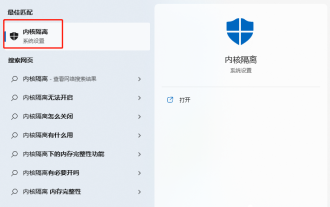 The driver cannot be loaded on this device. How to solve it? (Personally tested and valid)
Mar 14, 2024 pm 09:00 PM
The driver cannot be loaded on this device. How to solve it? (Personally tested and valid)
Mar 14, 2024 pm 09:00 PM
Everyone knows that if the computer cannot load the driver, the device may not work properly or interact with the computer correctly. So how do we solve the problem when a prompt box pops up on the computer that the driver cannot be loaded on this device? The editor below will teach you two ways to easily solve the problem. Unable to load the driver on this device Solution 1. Search for "Kernel Isolation" in the Start menu. 2. Turn off Memory Integrity, and it will prompt "Memory Integrity has been turned off. Your device may be vulnerable." Click behind to ignore it, and it will not affect the use. 3. The problem can be solved after restarting the machine.
 How to solve the problem of automatically saving pictures when publishing on Xiaohongshu? Where is the automatically saved image when posting?
Mar 22, 2024 am 08:06 AM
How to solve the problem of automatically saving pictures when publishing on Xiaohongshu? Where is the automatically saved image when posting?
Mar 22, 2024 am 08:06 AM
With the continuous development of social media, Xiaohongshu has become a platform for more and more young people to share their lives and discover beautiful things. Many users are troubled by auto-save issues when posting images. So, how to solve this problem? 1. How to solve the problem of automatically saving pictures when publishing on Xiaohongshu? 1. Clear the cache First, we can try to clear the cache data of Xiaohongshu. The steps are as follows: (1) Open Xiaohongshu and click the "My" button in the lower right corner; (2) On the personal center page, find "Settings" and click it; (3) Scroll down and find the "Clear Cache" option. Click OK. After clearing the cache, re-enter Xiaohongshu and try to post pictures to see if the automatic saving problem is solved. 2. Update the Xiaohongshu version to ensure that your Xiaohongshu
 How to publish works on Xiaohongshu How to publish articles and pictures on Xiaohongshu
Mar 22, 2024 pm 09:21 PM
How to publish works on Xiaohongshu How to publish articles and pictures on Xiaohongshu
Mar 22, 2024 pm 09:21 PM
You can view various contents on Xiaohongshu, which can provide you with various help and help you discover a better life. If you have anything you want to share, you can post it here so that everyone can take a look. , and at the same time, it can bring you profits. It is very cost-effective. If you don’t know how to publish your works here, you can check out the tutorial. You can use this software every day and publish various contents to help everyone use it better. Don’t miss it if you need it! 1. Open Xiaohongshu and click the plus icon below. 2. There are [Video] [Picture] [Live Picture] options here; select the content you want to publish and click to check. 3. Select [Next] on the content editing page. 4. Enter the text content you want to publish and click [Publish Pen]
 Why can't Xiaohongshu publish videos of works? How does it publish its work?
Mar 21, 2024 pm 06:36 PM
Why can't Xiaohongshu publish videos of works? How does it publish its work?
Mar 21, 2024 pm 06:36 PM
With the rapid development of social media, short video platforms have become the main channel for many users to express themselves and share their lives. Many users may encounter various problems when publishing videos of their works on Xiaohongshu. This article will discuss the reasons that may cause the video publishing of Xiaohongshu works to fail and provide the correct publishing method. 1. Why can’t Xiaohongshu publish videos of works? The Xiaohongshu platform may occasionally experience system failures, which may be caused by system maintenance or upgrades. In this case, users may encounter the problem of being unable to publish videos of their works. Users need to wait patiently for the platform to return to normal before trying to publish. An unstable or slow network connection may prevent users from posting videos of their work on Xiaohongshu. Users should confirm their network environment to ensure that the connection is stable and
 Why can't Xiaohongshu be released? What should I do if the content published by Xiaohongshu cannot be displayed?
Mar 21, 2024 pm 07:47 PM
Why can't Xiaohongshu be released? What should I do if the content published by Xiaohongshu cannot be displayed?
Mar 21, 2024 pm 07:47 PM
As a lifestyle sharing platform, Xiaohongshu has attracted a large number of users to share their daily life and grow products. Many users have reported that their published content cannot be displayed. What is going on? This article will analyze the possible reasons why Xiaohongshu cannot be released and provide solutions. 1. Why can’t Xiaohongshu be released? Xiaohongshu implements strict community guidelines and has zero tolerance for publishing advertisements, spam, vulgar content, etc. If the user's content violates the regulations, the system will block it and the content will not be displayed. Xiaohongshu requires users to publish high-quality and valuable content, and the content needs to be unique and innovative. If the content is too generic and lacks innovation, it may not pass review and therefore not be displayed on the platform. 3. Account abnormality
 When is the best time to publish Xiaohongshu? Where does it post the most traffic recommendations from?
Mar 21, 2024 pm 08:11 PM
When is the best time to publish Xiaohongshu? Where does it post the most traffic recommendations from?
Mar 21, 2024 pm 08:11 PM
In today's social network era, Xiaohongshu has become an important platform for young people to share their lives and obtain information. Many users hope to attract more attention and traffic by publishing content on Xiaohongshu. So, when is the best time to post content? This article will explore in detail the selection of Xiaohongshu’s publishing time and the publishing location with the most traffic recommendations. 1. When is the best time to publish Xiaohongshu? The best time to publish content on Xiaohongshu is usually during periods of high user activity. According to the characteristics and behavioral habits of Xiaohongshu users, there are several time periods that are more appropriate. During the time period from 7 pm to 9 pm, most users have returned home from get off work and started browsing content on their mobile phones in search of relaxation and entertainment. Therefore, content posted during this period is more likely to attract users
 How to delete Xiaohongshu releases? How to recover after deletion?
Mar 21, 2024 pm 05:10 PM
How to delete Xiaohongshu releases? How to recover after deletion?
Mar 21, 2024 pm 05:10 PM
As a popular social e-commerce platform, Xiaohongshu has attracted a large number of users to share their daily life and shopping experiences. Sometimes we may inadvertently publish some inappropriate content, which needs to be deleted in time to better maintain our personal image or comply with platform regulations. 1. How to delete Xiaohongshu releases? 1. Log in to your Xiaohongshu account and enter your personal homepage. 2. At the bottom of the personal homepage, find the "My Creations" option and click to enter. 3. On the "My Creations" page, you can see all published content, including notes, videos, etc. 4. Find the content that needs to be deleted and click the "..." button on the right. 5. In the pop-up menu, select the "Delete" option. 6. After confirming the deletion, the content will disappear from your personal homepage and public page.



