 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 The Essence of Script Security_PHP+MYSQL Page 1/3_PHP Tutorial
The Essence of Script Security_PHP+MYSQL Page 1/3_PHP Tutorial
The Essence of Script Security_PHP+MYSQL Page 1/3_PHP Tutorial
Preface to the existence of problems
If you consider code security from the code level, that is, the application level (that is, without considering the vulnerabilities of the underlying language itself), script security issues are functions and variables problem. Variables directly or indirectly receive unsafe input from users. Due to the characteristics of PHP itself, it is easier to find this kind of variable confusion in PHP (many PHP programs are used to define, initialize and receive variables, which can be used directly in the program The initialization of variables such as $id is completely completed by PHP settings. If you are not careful, it may cause confusion in the variables and lead to attacks).
After a variable receives unsafe input and is used in different places without proper filtering, it may cause different harms. If you directly enter the database and display it to the user, it will cause a cross-site scripting attack. If it is used in a sql statement, it may cause a Sql injection attack. These attacks have nothing to do with the specific scripting language. In various scripting languages All may exist. Since PHP variables are very flexible, if these harmful variables are used in some logical statements, it will cause the skipping of critical code such as authentication failure and skipping the initialization of some variables, causing confusion in the program logic and other vulnerabilities. If this variable is used in dangerous functions such as include, etc., of course there will be a file inclusion vulnerability. If it appears in the fopen function, it may cause a file writing vulnerability. If it appears in the mysql_query function, it will be a Sql injection vulnerability, eval and preg_replace. It may lead to the execution of code, appearing in the htmlspecia function may cause errors, and the environment in which the absolute path leak variable appears determines its possible harm.
After thinking about the existence of the problem, how to check this kind of vulnerability from the code level? Of course, being familiar with the PHP language is the most basic. You should also grasp functions and variables. If there are variables in dangerous functions, please determine the source of the variables, whether they are correctly initialized, and whether sensitive characters can be injected by users after initialization. Whether these sensitive characters have been completely cleared before entering the function. The difficulty in code review work may lie in determining the source of variables, which requires familiarity with PHP features and the code you are reviewing, but not all sources of variables are clearly visible, and some initialization codes may not be as clear as When you run it imaginatively, some of the things in the variables may come from places you don't want them to come from, and some variables may come from the database or system configuration files, but it is very likely that the database and configuration files have been modified before, or These variables are unsafely manipulated later and cannot be trusted. Next, we will think about the security of script code according to the ideas of variables and functions.
2 Where do variables come from?
1 Displayed input
Where does the variable come from? In fact, it means where the threat comes from. Just thinking about it from the web, what kind of website is the safest? Obviously, those websites that only provide static Html pages are the safest, because such websites do not interact with the browser in any way. It is like robbing an airtight bank. It is difficult to achieve, but for a large forum or script The program is different. When you log in, you need to pass variables such as username and password to the server. Even the IP and browser you logged in to are the objects captured by the program. The process of capturing an interaction with the server, such as posting a post, is captured by the program. Wait and you will find that the data transmission between the browser and the server may be visible to you, including the submitted form, address bar parameters, etc., but what you cannot see includes cookies, and HTTP headers are submitted data, that is, variables. place. These places are also the original entrances for the server to process data. So how does the PHP program accept variables? All submitted variables are saved in some arrays by PHP, including
$_GET
$_POST
$_COOKIE
$_FILES
$_SERVER
For initial convenience and flexibility, There is such an option in the php settings
register_globals
When this option is on, the variables that appear above will become a member of $GLOBALS and can be used directly without obtaining them in the script. , and overridden in the order of
variables_order
. Many programs consider register_globals to be off, so they use the following code when initializing the program:
@extract(daddslashes($_POST));
@extract(daddslashes($_GET));
These codes play the role of register_globals, which also releases the contents of POST and GET as global variables, but the danger may be greater, which will be mentioned later.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to Undo Delete from Home Screen in iPhone
Apr 17, 2024 pm 07:37 PM
How to Undo Delete from Home Screen in iPhone
Apr 17, 2024 pm 07:37 PM
Deleted something important from your home screen and trying to get it back? You can put app icons back on the screen in a variety of ways. We have discussed all the methods you can follow and put the app icon back on the home screen. How to Undo Remove from Home Screen in iPhone As we mentioned before, there are several ways to restore this change on iPhone. Method 1 – Replace App Icon in App Library You can place an app icon on your home screen directly from the App Library. Step 1 – Swipe sideways to find all apps in the app library. Step 2 – Find the app icon you deleted earlier. Step 3 – Simply drag the app icon from the main library to the correct location on the home screen. This is the application diagram
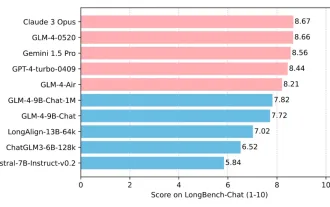 Tsinghua University and Zhipu AI open source GLM-4: launching a new revolution in natural language processing
Jun 12, 2024 pm 08:38 PM
Tsinghua University and Zhipu AI open source GLM-4: launching a new revolution in natural language processing
Jun 12, 2024 pm 08:38 PM
Since the launch of ChatGLM-6B on March 14, 2023, the GLM series models have received widespread attention and recognition. Especially after ChatGLM3-6B was open sourced, developers are full of expectations for the fourth-generation model launched by Zhipu AI. This expectation has finally been fully satisfied with the release of GLM-4-9B. The birth of GLM-4-9B In order to give small models (10B and below) more powerful capabilities, the GLM technical team launched this new fourth-generation GLM series open source model: GLM-4-9B after nearly half a year of exploration. This model greatly compresses the model size while ensuring accuracy, and has faster inference speed and higher efficiency. The GLM technical team’s exploration has not
 Create Agent in one sentence! Robin Li: The era is coming when everyone is a developer
Apr 17, 2024 pm 02:28 PM
Create Agent in one sentence! Robin Li: The era is coming when everyone is a developer
Apr 17, 2024 pm 02:28 PM
The big model subverts everything, and finally got to the head of this editor. It is also an Agent that was created in just one sentence. Like this, give him an article, and in less than 1 second, fresh title suggestions will come out. Compared to me, this efficiency can only be said to be as fast as lightning and as slow as a sloth... What's even more incredible is that creating this Agent really only takes a few minutes. Prompt belongs to Aunt Jiang: And if you also want to experience this subversive feeling, now, based on the new Wenxin intelligent agent platform launched by Baidu, everyone can create their own intelligent assistant for free. You can use search engines, smart hardware platforms, speech recognition, maps, cars and other Baidu mobile ecological channels to let more people use your creativity! Robin Li himself
 How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
How should the Java framework security architecture design be balanced with business needs?
Jun 04, 2024 pm 02:53 PM
Java framework design enables security by balancing security needs with business needs: identifying key business needs and prioritizing relevant security requirements. Develop flexible security strategies, respond to threats in layers, and make regular adjustments. Consider architectural flexibility, support business evolution, and abstract security functions. Prioritize efficiency and availability, optimize security measures, and improve visibility.
 The Mistral open source code model takes the throne! Codestral is crazy about training in over 80 languages, and domestic Tongyi developers are asking to participate!
Jun 08, 2024 pm 09:55 PM
The Mistral open source code model takes the throne! Codestral is crazy about training in over 80 languages, and domestic Tongyi developers are asking to participate!
Jun 08, 2024 pm 09:55 PM
Produced by 51CTO technology stack (WeChat ID: blog51cto) Mistral released its first code model Codestral-22B! What’s crazy about this model is not only that it’s trained on over 80 programming languages, including Swift, etc. that many code models ignore. Their speeds are not exactly the same. It is required to write a "publish/subscribe" system using Go language. The GPT-4o here is being output, and Codestral is handing in the paper so fast that it’s hard to see! Since the model has just been launched, it has not yet been publicly tested. But according to the person in charge of Mistral, Codestral is currently the best-performing open source code model. Friends who are interested in the picture can move to: - Hug the face: https
 How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to implement PHP security best practices
May 05, 2024 am 10:51 AM
How to Implement PHP Security Best Practices PHP is one of the most popular backend web programming languages used for creating dynamic and interactive websites. However, PHP code can be vulnerable to various security vulnerabilities. Implementing security best practices is critical to protecting your web applications from these threats. Input validation Input validation is a critical first step in validating user input and preventing malicious input such as SQL injection. PHP provides a variety of input validation functions, such as filter_var() and preg_match(). Example: $username=filter_var($_POST['username'],FILTER_SANIT
 Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
Security configuration and hardening of Struts 2 framework
May 31, 2024 pm 10:53 PM
To protect your Struts2 application, you can use the following security configurations: Disable unused features Enable content type checking Validate input Enable security tokens Prevent CSRF attacks Use RBAC to restrict role-based access
 Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
Implementing Machine Learning Algorithms in C++: Security Considerations and Best Practices
Jun 01, 2024 am 09:26 AM
When implementing machine learning algorithms in C++, security considerations are critical, including data privacy, model tampering, and input validation. Best practices include adopting secure libraries, minimizing permissions, using sandboxes, and continuous monitoring. The practical case demonstrates the use of the Botan library to encrypt and decrypt the CNN model to ensure safe training and prediction.





