PHP commonly used escape character functions
|
This article introduces the commonly used character escape functions and security functions in PHP. These functions can be used to filter most common attack methods, such as SQL injection.
Contents of this section: PHP escape character function usage. 1. addslashes addslashes escapes special characters in SQL statements, including ('), ("), (), (NUL) four characters. This function is used when the DBMS does not have its own escape function, but if the DBMS has its own Escape function, it is recommended to use the original function. For example, MySQL has the mysql_real_escape_string function to escape SQL. Note that before PHP5.3, magic_quotes_gpc is enabled by default, which mainly performs addslashes on $GET, $POST, and $COOKIE. operation, so there is no need to call addslashes repeatedly on these variables, otherwise it will double escaping. However, magic_quotes_gpc has been abandoned in PHP5.3 and has been removed since PHP5.4. If you use the latest version of PHP, you don’t have to worry. This question. stripslashes is the unescape function of addslashes. 2.htmlspecialchars htmlspecialchars escapes several special characters in HTML into HTML Entity (format: &xxxx;) form, including (&), (‘), (“), () five characters. & (AND) => & " (double quotes) => " (when ENT_NOQUOTES is not set) ' (single quote) => ' (when ENT_QUOTES is set) (greater than sign) => > htmlspecialchars can be used to filter $GET, $POST, $COOKIE data to prevent XSS. Note that the htmlspecialchars function only escapes HTML characters that are considered security risks. If you want to escape all characters that can be escaped in HTML, please use htmlentities. htmlspecialchars_decode is the decode function of htmlspecialchars. 3.htmlentities htmlentities escapes the escapable content in HTML into HTML Entities. html_entity_decode is the decode function of htmlentities.4. mysql_real_escape_string mysql_real_escape_string will call the MySQL library function mysql_real_escape_string to escape (x00), (n), (r), (), (‘), (x1a), that is, add a backslash () in front to prevent SQL injection. Note that you do not need to call stripslashes to unescape when reading the database data, because these backslashes are added when the database executes SQL, and the backslashes will be removed when the data is written to the database, so The content written to the database is the original data, and there will be no backslashes in front. 5. strip_tags strip_tags will filter out NUL, HTML and PHP tags. 6. Conclusion The security functions that come with PHP cannot completely avoid XSS. It is recommended to use HTML Purifier. Detailed explanation of PHP escaping usage Magic quotation function for data in php magic_quotes_gpc or magic_quotes_runtime When set to on, when the data we quote encounters single quotes', double quotes" and backslashes, backslashes are automatically added to help us automatically translate symbols and ensure the correct operation of data operations. The difference between the two: magic_quotes_gpc The scope of action is: WEB client server; When: The request starts, for example when the script is run. magic_quotes_runtime Scope of scope: Data read from a file or the result of executing exec() or obtained from a SQL query; Time of action: Every time the script accesses data generated in the running state. As can be seen The setting value of magic_quotes_gpc will affect the data obtained through Get/Post/Cookies The setting value of magic_quotes_runtime will affect the data read from the file or the data obtained from the database query Several functions that I want to associate: set_magic_quotes_runtime(): Set the magic_quotes_runtime value. 0=off. 1=on. The default state is off. You can view magic_quotes_runtime through echo phpinfo(); get_magic_quotes_gpc(): View magic_quotes_gpc value.0=off.1=on get_magic_quotes_runtime(): Check the magic_quotes_runtime value. 0=off. 1=on. Note that there is no set_magic_quotes_gpc() function, that is, the value of magic_quotes_gpc cannot be set in the program. Due to the setting problem of the two values, it will cause some confusion during programming or add an extra escape. In this case, it needs to be set and judged at the beginning of the program, or the default configuration Both values are off. The escaping part is performed programmatically. To ensure that the data is inserted normally, addslashes is usually used to process it. When reading data, stripslashes is often used to remove the added backslashes. Similar character conversion functions in php addslashes adds a backslash before the predefined characters specified by stripslashes removes backslashes added by addslashes() function htmlspecialchars converts some predefined characters into HTML entities htmlspecialchars_decode converts some predefined HTML entities into characters html_entity_decode() converts HTML entities into characters htmlentities() Convert characters to HTML entities |

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
11 Best PHP URL Shortener Scripts (Free and Premium)
Mar 03, 2025 am 10:49 AM
Long URLs, often cluttered with keywords and tracking parameters, can deter visitors. A URL shortening script offers a solution, creating concise links ideal for social media and other platforms. These scripts are valuable for individual websites a
 Introduction to the Instagram API
Mar 02, 2025 am 09:32 AM
Introduction to the Instagram API
Mar 02, 2025 am 09:32 AM
Following its high-profile acquisition by Facebook in 2012, Instagram adopted two sets of APIs for third-party use. These are the Instagram Graph API and the Instagram Basic Display API.As a developer building an app that requires information from a
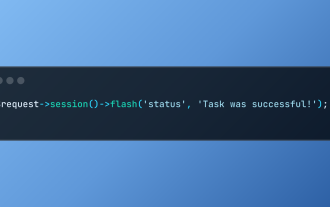 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
Build a React App With a Laravel Back End: Part 2, React
Mar 04, 2025 am 09:33 AM
This is the second and final part of the series on building a React application with a Laravel back-end. In the first part of the series, we created a RESTful API using Laravel for a basic product-listing application. In this tutorial, we will be dev
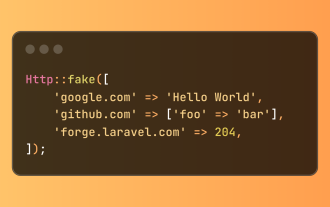 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
Announcement of 2025 PHP Situation Survey
Mar 03, 2025 pm 04:20 PM
The 2025 PHP Landscape Survey investigates current PHP development trends. It explores framework usage, deployment methods, and challenges, aiming to provide insights for developers and businesses. The survey anticipates growth in modern PHP versio






