An in-depth analysis of PHP data encryption methods
Then, we assume that the following data is already stored in the table:
I will be using Apache's password-response authentication configuration to prompt the user for their username and password. A little known fact about PHP is that it can pass the Apache password-response system input to the user. The name and password are identified as $PHP_AUTH_USER and $PHP_AUTH_PW, which I will use in the authentication script. Take some time to read the script below carefully and pay more attention to the explanations to better understand the following code: Application of crypt() and Apache's password-response verification system
The above is a simple authentication system to verify user access rights. When using crypt() to protect important confidential information, remember that crypt() used by default is not the most secure and can only be used in systems with lower security requirements. If higher security is required Performance requires the algorithm I introduce later in this article. Next I will introduce another function supported by PHP━━md5(). This function uses the MD5 hash algorithm. It has several interesting uses worth mentioning: Mixed A hash function transforms a variable-length message into a fixed-length hashed output, also known as a "message digest". This is useful because a fixed-length string can be used to check file integrity and verify digital signatures and user authentication. As it is suitable for PHP, PHP's built-in md5() hash function will convert a variable-length message into a 128-bit (32-character) message digest. An interesting feature of mixed encoding is that the original plain code cannot be obtained by analyzing the mixed information, because the mixed result has no dependence on the original plain code content. Even changing only one character in a string will cause the MD5 hybrid algorithm to calculate two completely different results. Let’s first look at the contents of the following table and its corresponding results: Use md5() to mix strings
Results: hash: 81ea092649ca32b5ba375e81d8f4972c Note that the result is 32 characters long. Take a look at the following table again, where the value of $msg has changed slightly: Use md5() to shuffle a slightly changed string
Results: hash2: e86cf511bd5490d46d5cd61738c82c0c It can be found that although the length of both results is 32 characters, a small change in the plaintext causes a big change in the result. Therefore, the hashing and md5() functions are a good way to check small changes in the data. Tool of. Although crypt() and md5() have their uses, both are subject to certain limitations in functionality. In the following sections, we will introduce two very useful PHP extensions called Mcrypt and Mhash, which will greatly expand the encryption options for PHP users. Although we have explained the importance of one-way encryption in the above section, sometimes we may need to restore the password data to the original data after encryption. Fortunately, PHP provides this in the form of the Mcrypt extension library possibility. Mcrypt Mcrypt 2.5.7 Unix | Win32 Mcrypt 2.4.7 is a powerful encryption algorithm extension library, which includes 22 algorithms, including the following algorithms: Blowfish RC2 Safer-sk64 xtea Cast-256 RC4 Safer-sk128 DES RC4-iv Serpent Enigma Rijndael-128 Threeway Gost Rijndael-192 TripleDES LOKI97 Rijndael-256 Twofish PanamaSaferplus Wake 1 2 Next Page Last Page |

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
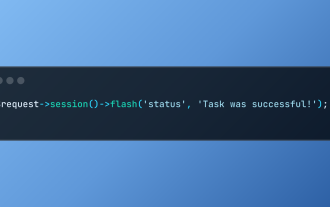 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
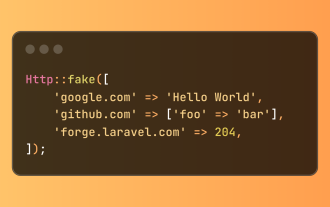 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot
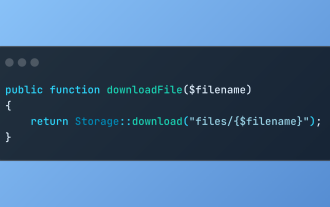 Discover File Downloads in Laravel with Storage::download
Mar 06, 2025 am 02:22 AM
Discover File Downloads in Laravel with Storage::download
Mar 06, 2025 am 02:22 AM
The Storage::download method of the Laravel framework provides a concise API for safely handling file downloads while managing abstractions of file storage. Here is an example of using Storage::download() in the example controller:
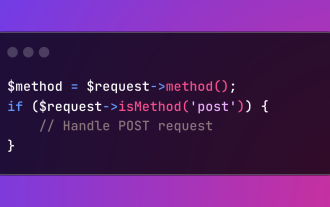 HTTP Method Verification in Laravel
Mar 05, 2025 pm 04:14 PM
HTTP Method Verification in Laravel
Mar 05, 2025 pm 04:14 PM
Laravel simplifies HTTP verb handling in incoming requests, streamlining diverse operation management within your applications. The method() and isMethod() methods efficiently identify and validate request types. This feature is crucial for building






