How to prevent sql injection in php
This is Because the user can enter something like VALUE "); DROP TABLE table; - , making the query become:
How to avoid this situation? Use prepared statements and parameterized queries. SQL statements with any parameters will be sent to the database server and parsed! It is impossible for an attacker to maliciously inject SQL! There are two options: 1. Use PDO (PHP Data Objects):
For a detailed introduction to using pdo to prevent sql injection, please refer to: Learn to use PDO to query Mysql to avoid SQL injection risk. 2. Use mysqli:
PDO (PHP Data Object) Note that when using PDO to access the mysql database, the real prepared statements are not used by default! To resolve this issue, you must disable emulation of prepared statements. An example of using PDO to create a connection is as follows:
The error mode ERRMODE is not strictly necessary in the above example, but it is recommended to add it. This method does not stop the script when a fatal error occurs. And give the developer a chance to catch any errors (when PDOException is thrown). The setAttribute() line is mandatory, it tells PDO to disable emulated prepared statements and use real prepared statements. This ensures that statements and values are not parsed by PHP before being sent to the MySQL database server (there is no opportunity for an attacker to inject malicious SQL). Of course you can set the character set parameter in the constructor options, especially note that 'old' PHP versions (5.3.6) will ignore the character set parameter in the DSN. Explanation What happens when the SQL prepared statement you pass is parsed and compiled by the database server? Tell the database engine what you want to filter by specifying characters (like a? or like :name in the above example). Then call execute to execute the combined prepared statement and the parameter value you specified. The most important thing here is that the parameter value is combined with a precompiled statement, not with a SQL string. SQL injection works by deceptively creating a SQL script that includes a malicious string and sends it to the database. Therefore, By sending actual separate sql parameters, you will reduce the risk. When using prepared statements, any parameters you send, will only be treated as strings (although the database engine may do some parameter optimization, which of course may eventually is a number). In the above example, if the variable $name contains 'sarah';DELETE * FROM employees, the result will only be a search string "'sarah';DELETE * FROM employees", you will not get an empty surface. Another benefit: if the same statement is executed multiple times in the same session, this will only be parsed and compiled once. Example (using PDO):
|

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
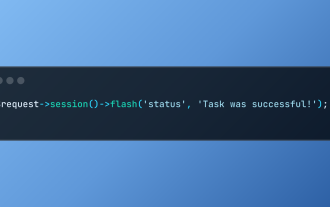 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
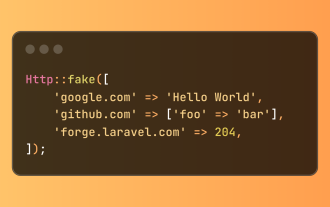 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP Logging: Best Practices for PHP Log Analysis
Mar 10, 2025 pm 02:32 PM
PHP logging is essential for monitoring and debugging web applications, as well as capturing critical events, errors, and runtime behavior. It provides valuable insights into system performance, helps identify issues, and supports faster troubleshoot
 How to Register and Use Laravel Service Providers
Mar 07, 2025 am 01:18 AM
How to Register and Use Laravel Service Providers
Mar 07, 2025 am 01:18 AM
Laravel's service container and service providers are fundamental to its architecture. This article explores service containers, details service provider creation, registration, and demonstrates practical usage with examples. We'll begin with an ove
 Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
The article discusses adding custom functionality to frameworks, focusing on understanding architecture, identifying extension points, and best practices for integration and debugging.






