 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Analysis of PHP encryption function principle of discuz x1.5 discuz program
Analysis of PHP encryption function principle of discuz x1.5 discuz program
Analysis of PHP encryption function principle of discuz x1.5 discuz program
The principle is as follows, if:
Encryption
Plain text: 1010 1001
Key: 1110 0011 Cipher text: 0100 1010
The cipher text is 0100 1010. The decryption need is XORed with the key
Decryption cipher text: 0100 1010
Key: 1110 0011
Clear text: 1010 1001
There is no sophisticated algorithm. The key is very important, so the key lies in how to generate the key.
Let’s take a look at how Kangsheng’s authcode is done
Copy the code The code is as follows:
// Parameter explanation// $string: plain text or cipher text
// $operation: DECODE means Decryption, others represent encryption
// $key: secret key
// $expiry: ciphertext validity period
function authcode($string, $operation = 'DECODE', $key = '', $expiry = 0) {
/ / Dynamic key length, the same plaintext will generate different ciphertext, relying on the dynamic key
$ckey_length = 4;
// Key
$key = md5($key ? $key : $GLOBALS['discuz_auth_key']) ;
// Key a will participate in encryption and decryption
$keya = md5(substr($key, 0, 16));
// Key b will be used for data integrity verification
$keyb = md5(substr( $key, 16, 16));
// Key c is used to change the generated ciphertext
$keyc = $ckey_length ? ($operation == 'DECODE' ? substr($string, 0, $ckey_length):
substr(md5(microtime()), -$ckey_length)) : '';
//Key involved in the operation
$cryptkey = $keya.md5($keya.$keyc);
$key_length = strlen($cryptkey ; // If decoding, it will start from the $ckey_length bit, because the dynamic key is stored in the $ckey_length bit before the ciphertext to ensure correct decryption
$string = $operation == 'DECODE' ? base64_decode(substr($string, $ckey_length)) :
sprintf('%010d', $expiry ? $expiry + time() : 0).substr(md5($string.$keyb), 0, 16).$string;
$string_length = strlen ($string);
$result = '';
$box = range(0, 255);
$rndkey = array();
// Generate key book
for($i = 0; $i < = 255; $i++) {
$rndkey[$i] = ord($cryptkey[$i % $key_length]);
}
// Use a fixed algorithm to scramble the key book and increase randomness. It seems very Complex, in fact the pair does not increase the strength of the ciphertext
for($j = $i = 0; $i < 256; $i++) {
$j = ($j + $box[$i] + $ rndkey[$i]) % 256;
$tmp = $box[$i];
$box[$i] = $box[$j];
$box[$j] = $tmp;
}
/ / Core encryption and decryption part
for($a = $j = $i = 0; $i < $string_length; $i++) {
$a = ($a + 1) % 256;
$j = ($j + $box[$a]) % 256;
$tmp = $box[$a];
$box[$a] = $box[$j];
$box[$j] = $tmp;
/ / Get the key from the key book, perform XOR, and then convert it into characters
$result .= chr(ord($string[$i]) ^ ($box[($box[$a] + $box[$ j]) % 256]));
}
if($operation == 'DECODE') {
// substr($result, 0, 10) == 0 Verify data validity
// substr($result, 0, 10) - time() > 0 Verify data validity
// substr($result, 10, 16) == substr(md5(substr($result, 26).$keyb), 0, 16) Verify Data integrity
// Verify data validity, please see the format of unencrypted plaintext
if((substr($result, 0, 10) == 0 || substr($result, 0, 10) - time() > ; 0) &&
substr($result, 10, 16) == substr(md5(substr($result, 26).$keyb), 0, 16)) {
return substr($result, 26);
} else {
return '';
}
} else {
// Save the dynamic key in the ciphertext, which is why the same plaintext can be decrypted after producing different ciphertexts
// Because the encrypted password The text may contain some special characters and may be lost during the copying process, so use base64 encoding
return $keyc.str_replace('=', '', base64_encode($result));
}
}
But it’s a bit regretful, this The function ownership belongs to Kangsheng Chuangxiang and cannot be used freely.
The above introduces the analysis of the PHP encryption function principle of the discuz x1.5 discuz program, including the content of discuz x1.5. I hope it will be helpful to friends who are interested in PHP tutorials.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1376
1376
 52
52
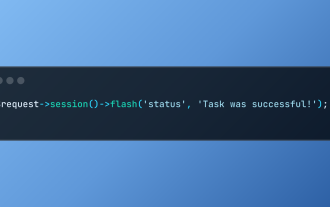 Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Working with Flash Session Data in Laravel
Mar 12, 2025 pm 05:08 PM
Laravel simplifies handling temporary session data using its intuitive flash methods. This is perfect for displaying brief messages, alerts, or notifications within your application. Data persists only for the subsequent request by default: $request-
 cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
cURL in PHP: How to Use the PHP cURL Extension in REST APIs
Mar 14, 2025 am 11:42 AM
The PHP Client URL (cURL) extension is a powerful tool for developers, enabling seamless interaction with remote servers and REST APIs. By leveraging libcurl, a well-respected multi-protocol file transfer library, PHP cURL facilitates efficient execution of various network protocols, including HTTP, HTTPS, and FTP. This extension offers granular control over HTTP requests, supports multiple concurrent operations, and provides built-in security features.
 Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP SDK transfer error: How to solve the problem of 'Cannot declare class SignData'?
Apr 01, 2025 am 07:21 AM
Alipay PHP...
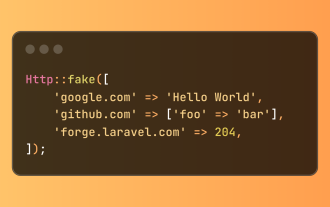 Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Simplified HTTP Response Mocking in Laravel Tests
Mar 12, 2025 pm 05:09 PM
Laravel provides concise HTTP response simulation syntax, simplifying HTTP interaction testing. This approach significantly reduces code redundancy while making your test simulation more intuitive. The basic implementation provides a variety of response type shortcuts: use Illuminate\Support\Facades\Http; Http::fake([ 'google.com' => 'Hello World', 'github.com' => ['foo' => 'bar'], 'forge.laravel.com' =>
 12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
12 Best PHP Chat Scripts on CodeCanyon
Mar 13, 2025 pm 12:08 PM
Do you want to provide real-time, instant solutions to your customers' most pressing problems? Live chat lets you have real-time conversations with customers and resolve their problems instantly. It allows you to provide faster service to your custom
 Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Explain the concept of late static binding in PHP.
Mar 21, 2025 pm 01:33 PM
Article discusses late static binding (LSB) in PHP, introduced in PHP 5.3, allowing runtime resolution of static method calls for more flexible inheritance.Main issue: LSB vs. traditional polymorphism; LSB's practical applications and potential perfo
 Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
Customizing/Extending Frameworks: How to add custom functionality.
Mar 28, 2025 pm 05:12 PM
The article discusses adding custom functionality to frameworks, focusing on understanding architecture, identifying extension points, and best practices for integration and debugging.
 Framework Security Features: Protecting against vulnerabilities.
Mar 28, 2025 pm 05:11 PM
Framework Security Features: Protecting against vulnerabilities.
Mar 28, 2025 pm 05:11 PM
Article discusses essential security features in frameworks to protect against vulnerabilities, including input validation, authentication, and regular updates.



