Universal encrypted php file restoration method
The previous article Practical Restoration of PHP Encrypted Files mentioned that I discovered the shortcomings of the PHP encryption method, so I wrote this article.
Background analysis
As we all know, PHP is a scripting language. Scripting languages mainly use interpretation instead of compilation. So compared to compiled languages (C, C#, C++), it does not have the ability to directly generate exedll. Therefore, the traditional encryption method cannot be used.
So there are generally two encryption methods in PHP: obfuscation and encryption.
Obfuscation is not encryption in the strict sense. This kind of code is like the code that uses pinyin abbreviations to name variables, but it looks like you have worked harder. This is beyond the scope of our discussion.
Encryption is performed in two ways: one is with extension (Loader). The other is no extension.
First, let’s talk about the encryption method without expansion. This encryption method is very brainless, because its decryption process is public and requires the use of known PHP functions. The encrypted code is generally similar to the following:
<?phpeval(base64_decode("cGhwaW5mbygpOw=="));Even the one that looks very complicated:

is just a variation of the above. This decryption form is very easy to crack if it is exposed. Just find eval and change it to echo.
The other extension method is more complicated. The function of the extension here is mainly to decrypt and execute the code. Compared with the non-extension form, it hides the decryption and execution code in the extension, so the cracking is more complicated.
The extensions here are generally divided into two types: 1. Those that provide decryption execution functions. 2. Directly overwrite zend_compile_file to implement the function of parsing custom php files.
The first and most typical example is the zoeeyguard mentioned in my last article, which mainly uses the zend_eval_string function to execute PHP code.
The second representative includes: Zend Guard and Song Ge’s php-beast.
It can be said that the two cracking ideas are similar. You can give priority to trying the ideas in my previous article.
Of course, what if I didn’t solve the problem in my previous article?
At this time, you need to use a big killer weapon.
You will find that I have been talking about the two functions zend_compile_file and zend_eval_string in the previous article. Some smart phpers have already thought of it, yes! The idea is still to find eval and change it to echo.
Practical examples
We can’t just talk without doing anything. Let’s take an example:
This time we’ll start with Brother Song’s php-beast. Brother Song's code is very beautifully written. Knowing that AES DES decryption takes time, he wrote a Cache.
1. Download the php source code package for Linux (it is best to choose one between 5.6 and 5.5. 7 is not supported. BTW: 7 has a lot of changes. Many things are not compatible. Zend Guard does not support 7 either. I took a detour here.)
2. Find the function in the file Zendzend_language_scanner.c: zend_op_array *compile_file(zend_file_handle *file_handle, int type TSRMLS_DC) which is about 500 lines long. Add the following code in front of it (the code is written It sucks, don’t complain):
ZEND_API zend_op_array *compile_file(zend_file_handle *file_handle, int type TSRMLS_DC)
{
zend_lex_state original_lex_state;
zend_op_array *op_array = (zend_op_array *) emalloc(sizeof(zend_op_array));
zend_op_array *original_active_op_array = CG(active_op_array);
zend_op_array *retval=NULL;
int compiler_result;
zend_bool compilation_successful=0;
znode retval_znode;
zend_bool original_in_compilation = CG(in_compilation);
/** BEGIN **/
//加在这里的含义就是每次php编译php源码的时候都把这份源码打印一份
char *buf;
size_t size;
zend_stream_fixup(file_handle, &buf, &size);
printf("\n#######\nFILE TYPE: %d FILE NAME: %s CONTENT: %s\n#######\n", (*file_handle).type, (*file_handle).filename, buf);
/** END **/Execute in the php folder:
//节省点时间 ./configure --disable-ipv6 --disable-all make make install
4. If everything goes well, PHP has been installed successfully.
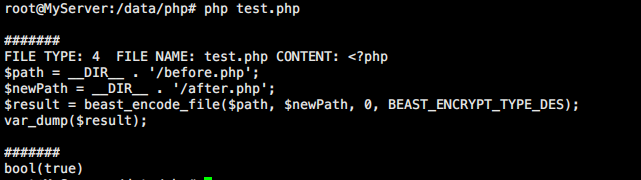
5. We write two test files: the function is: test.php executes it to encrypt before.php to generate after.php.
//test.php <?php $path = __DIR__ . '/before.php'; $newPath = __DIR__ . '/after.php'; $result = beast_encode_file($path, $newPath, 0, BEAST_ENCRYPT_TYPE_DES); var_dump($result);
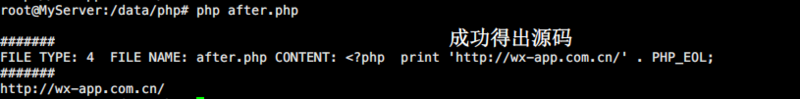
//before.php <?php print 'http://wx-app.com.cn/' . PHP_EOL;
7. Execute the following php test.php and then execute php after.php.
Look at the screenshots below:
Summary
1. There is no password that cannot be broken. All we can do is increase the cracking time. If the cracking time is greater than a person's lifespan, then this encryption method is definitely successful.
2. For encrypted programs, just as the cracker needs to understand and guess the writer's thinking, the writer also needs to understand the cracker's methods and means. Only in this way can we write programs that are more difficult to crack.
3. Compared with encryption, I think obfuscation is more suitable for "encryption" of PHP source code.
4. If you want to encrypt your PHP code and publish it, the best way is to increase the fee and provide the source code directly.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1389
1389
 52
52
 PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 Installation and Upgrade guide for Ubuntu and Debian
Dec 24, 2024 pm 04:42 PM
PHP 8.4 brings several new features, security improvements, and performance improvements with healthy amounts of feature deprecations and removals. This guide explains how to install PHP 8.4 or upgrade to PHP 8.4 on Ubuntu, Debian, or their derivati
 7 PHP Functions I Regret I Didn't Know Before
Nov 13, 2024 am 09:42 AM
7 PHP Functions I Regret I Didn't Know Before
Nov 13, 2024 am 09:42 AM
If you are an experienced PHP developer, you might have the feeling that you’ve been there and done that already.You have developed a significant number of applications, debugged millions of lines of code, and tweaked a bunch of scripts to achieve op
 How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
How To Set Up Visual Studio Code (VS Code) for PHP Development
Dec 20, 2024 am 11:31 AM
Visual Studio Code, also known as VS Code, is a free source code editor — or integrated development environment (IDE) — available for all major operating systems. With a large collection of extensions for many programming languages, VS Code can be c
 Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
Explain JSON Web Tokens (JWT) and their use case in PHP APIs.
Apr 05, 2025 am 12:04 AM
JWT is an open standard based on JSON, used to securely transmit information between parties, mainly for identity authentication and information exchange. 1. JWT consists of three parts: Header, Payload and Signature. 2. The working principle of JWT includes three steps: generating JWT, verifying JWT and parsing Payload. 3. When using JWT for authentication in PHP, JWT can be generated and verified, and user role and permission information can be included in advanced usage. 4. Common errors include signature verification failure, token expiration, and payload oversized. Debugging skills include using debugging tools and logging. 5. Performance optimization and best practices include using appropriate signature algorithms, setting validity periods reasonably,
 How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
How do you parse and process HTML/XML in PHP?
Feb 07, 2025 am 11:57 AM
This tutorial demonstrates how to efficiently process XML documents using PHP. XML (eXtensible Markup Language) is a versatile text-based markup language designed for both human readability and machine parsing. It's commonly used for data storage an
 PHP Program to Count Vowels in a String
Feb 07, 2025 pm 12:12 PM
PHP Program to Count Vowels in a String
Feb 07, 2025 pm 12:12 PM
A string is a sequence of characters, including letters, numbers, and symbols. This tutorial will learn how to calculate the number of vowels in a given string in PHP using different methods. The vowels in English are a, e, i, o, u, and they can be uppercase or lowercase. What is a vowel? Vowels are alphabetic characters that represent a specific pronunciation. There are five vowels in English, including uppercase and lowercase: a, e, i, o, u Example 1 Input: String = "Tutorialspoint" Output: 6 explain The vowels in the string "Tutorialspoint" are u, o, i, a, o, i. There are 6 yuan in total
 Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Explain late static binding in PHP (static::).
Apr 03, 2025 am 12:04 AM
Static binding (static::) implements late static binding (LSB) in PHP, allowing calling classes to be referenced in static contexts rather than defining classes. 1) The parsing process is performed at runtime, 2) Look up the call class in the inheritance relationship, 3) It may bring performance overhead.
 What are PHP magic methods (__construct, __destruct, __call, __get, __set, etc.) and provide use cases?
Apr 03, 2025 am 12:03 AM
What are PHP magic methods (__construct, __destruct, __call, __get, __set, etc.) and provide use cases?
Apr 03, 2025 am 12:03 AM
What are the magic methods of PHP? PHP's magic methods include: 1.\_\_construct, used to initialize objects; 2.\_\_destruct, used to clean up resources; 3.\_\_call, handle non-existent method calls; 4.\_\_get, implement dynamic attribute access; 5.\_\_set, implement dynamic attribute settings. These methods are automatically called in certain situations, improving code flexibility and efficiency.




