 Backend Development
Backend Development
 PHP Tutorial
PHP Tutorial
 Complete explanation of PHP vulnerabilities (3)-Client script implantation
Complete explanation of PHP vulnerabilities (3)-Client script implantation
Complete explanation of PHP vulnerabilities (3)-Client script implantation
Client-side script insertion (Script Insertion) refers to inserting executable scripts into objects such as forms, pictures, animations, or hyperlink text. When the user opens these objects, the script implanted by the attacker will be executed, and the attack will begin.
HTML tags that can be used as script implants generally include the following:
1. Page scripts such as javascript and vbscript marked by the <script> tag. You can specify the js program code in the <script> tag, or you can specify the URL path of the js file in the src attribute. 2. The object marked by the <object> tag. These objects are java applets, multimedia files, ActiveX controls, etc. Usually the URL path of the object is specified in the data attribute </script>
3. Object marked with
4. Object marked with
The attack steps of client-side script implantation
1. The attacker logs in to the website after registering as a normal user
2. Open the message page and insert the attack js code
3. Other users log in to the website (including administrators) and browse the content of this message
4. The js code hidden in the message content is executed, and the attack is successful
Instance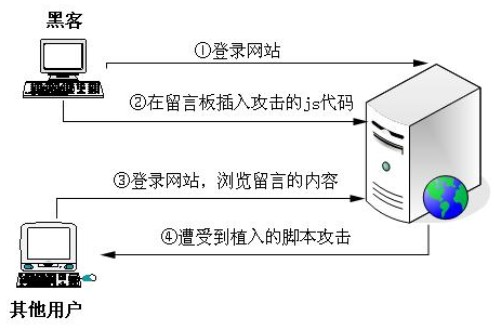 Database
Database
CREATE TABLE `postmessage` (
`id` int(11) NOT NULL auto_increment,
`subject` varchar(60) NOT NULL default ”,
`name` varchar(40) NOT NULL default ”,
`email ` varchar(25) NOT NULL default ”,
`question` mediumtext NOT NULL,
`postdate` datetime NOT NULL default '0000-00-00 00:00:00′,
PRIMARY KEY (`id`)
) ENGINE=MyISAM DEFAULT CHARSET=gb2312 COMMENT='User's Message' AUTO_INCREMENT=69;
//add.php insert message
//list.php message list
//show.php display message
Submit the message below
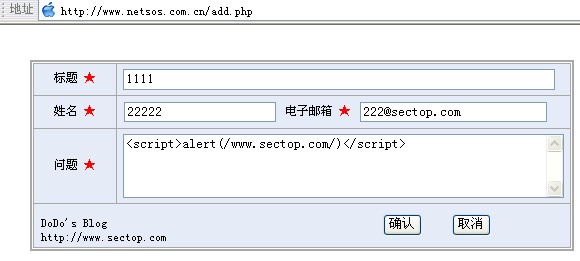
Insert <script>while(1){windows.open();}</script> infinite pop-up box
Insert<script>location.href="http://www.php1.cn/"></script>
or use other self-constructed js code to attack
Prevention methods
Generally use the htmlspecialchars function to Convert special characters to HTML encoding
Function prototype
string htmlspecialchars (string string, int quote_style, string charset)
string is the string to be encoded
quote_style optional, the value can be ENT_COMPAT, ENT_QUOTES, ENT_NOQUOTES, default value ENT_COMPAT means converting only double quotes but not single quotes. ENT_QUOTES means converting both double quotes and single quotes. ENT_NOQUOTES, indicating that double quotes and single quotes will not be converted.
charset is optional, indicating the character set used. The
function will convert the following special characters into html encoding:
& —-> &
" —-> "
' —-> '
> —-> >
Change line 98 of show.php to
Then check the vulnerability page where js is inserted
The above is the complete solution of PHP vulnerabilities (3) - the content of client script implantation, For more related content, please pay attention to the PHP Chinese website (www.php.cn)!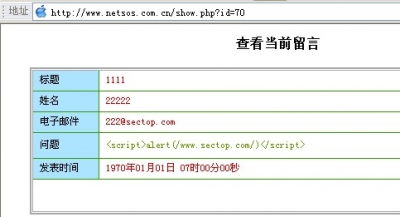

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
![VMware Horizon Client cannot be opened [Fix]](https://img.php.cn/upload/article/000/887/227/170835607042441.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) VMware Horizon Client cannot be opened [Fix]
Feb 19, 2024 pm 11:21 PM
VMware Horizon Client cannot be opened [Fix]
Feb 19, 2024 pm 11:21 PM
VMware Horizon Client helps you access virtual desktops conveniently. However, sometimes the virtual desktop infrastructure may experience startup issues. This article discusses the solutions you can take when the VMware Horizon client fails to start successfully. Why won't my VMware Horizon client open? When configuring VDI, if the VMWareHorizon client is not open, an error may occur. Please confirm that your IT administrator has provided the correct URL and credentials. If everything is fine, follow the solutions mentioned in this guide to resolve the issue. Fix VMWareHorizon Client Not Opening If VMW is not opening on your Windows computer
![VMware Horizon client freezes or stalls while connecting [Fix]](https://img.php.cn/upload/article/000/887/227/170942987315391.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) VMware Horizon client freezes or stalls while connecting [Fix]
Mar 03, 2024 am 09:37 AM
VMware Horizon client freezes or stalls while connecting [Fix]
Mar 03, 2024 am 09:37 AM
When connecting to a VDI using the VMWareHorizon client, we may encounter situations where the application freezes during authentication or the connection blocks. This article will explore this issue and provide ways to resolve this situation. When the VMWareHorizon client experiences freezing or connection issues, there are a few things you can do to resolve the issue. Fix VMWareHorizon client freezes or gets stuck while connecting If VMWareHorizon client freezes or fails to connect on Windows 11/10, do the below mentioned solutions: Check network connection Restart Horizon client Check Horizon server status Clear client cache Fix Ho
 PHP MQTT Client Development Guide
Mar 27, 2024 am 09:21 AM
PHP MQTT Client Development Guide
Mar 27, 2024 am 09:21 AM
MQTT (MessageQueuingTelemetryTransport) is a lightweight message transmission protocol commonly used for communication between IoT devices. PHP is a commonly used server-side programming language that can be used to develop MQTT clients. This article will introduce how to use PHP to develop an MQTT client and include the following content: Basic concepts of the MQTT protocol Selection and usage examples of the PHPMQTT client library: Using the PHPMQTT client to publish and
 How to solve the problem that the Baidu Netdisk webpage cannot start the client?
Mar 13, 2024 pm 05:00 PM
How to solve the problem that the Baidu Netdisk webpage cannot start the client?
Mar 13, 2024 pm 05:00 PM
When many friends download files, they will first browse on the web page and then transfer to the client to download. But sometimes users will encounter the problem that the Baidu Netdisk webpage cannot start the client. In response to this problem, the editor has prepared a solution for you to solve the problem that the Baidu Netdisk webpage cannot start the client. Friends in need can refer to it. Solution: 1. Maybe Baidu Netdisk is not the latest version. Manually open the Baidu Netdisk client, click the settings button in the upper right corner, and then click version upgrade. If there is no update, the following prompt will appear. If there is an update, please follow the prompts to update. 2. The detection service program of Baidu Cloud Disk may be disabled. It is possible that we manually or use security software to automatically disable the detection service program of Baidu Cloud Disk. Please check it out
 What is the mobile client
Aug 16, 2023 pm 01:40 PM
What is the mobile client
Aug 16, 2023 pm 01:40 PM
A mobile client refers to an application that runs on a smartphone and provides users with various functions and services in the form of a native client or a web client. Mobile clients can be divided into two forms: original clients and web clients. Native clients refer to applications written for specific operating systems using specific programming languages and development tools. The advantage of web clients is that they have good cross-platform compatibility. , can run on different devices without operating system restrictions, but compared to the native client, the performance and user experience of the web client may be reduced.
 How to write an FTP client in PHP
Aug 01, 2023 pm 07:23 PM
How to write an FTP client in PHP
Aug 01, 2023 pm 07:23 PM
How to write an FTP client in PHP 1. Introduction FTP (File Transfer Protocol) is a protocol used for file transfer on the network. In web development, we often need to upload or download files through FTP. As a popular server-side language, PHP provides powerful FTP functions, allowing us to easily write FTP clients. This article will introduce how to write a simple FTP client using PHP and provide code examples. 2. Connect to the FTP server in PHP, we can use f
 How to remove the shield logo above the Win11 client?
Jan 05, 2024 am 11:21 AM
How to remove the shield logo above the Win11 client?
Jan 05, 2024 am 11:21 AM
Some Win11 users have noticed that the shield logo appears next to some software icons on their personal computers. This protects computer systems and even the important information and data stored in them from infringement. If you don't like it, you can solve it by the following method. How to remove the shield logo on the win11 client 1. Right-click the taskbar on the computer and select "Task Manager" 2. Then click "Start" above 3. Find "Windows Defender" here and right-click and select "Disable", then Just restart the computer.
 win11 client and server do not support commonly used ssl
Dec 29, 2023 pm 02:09 PM
win11 client and server do not support commonly used ssl
Dec 29, 2023 pm 02:09 PM
If neither the client nor the server implements SSL encryption technology, it is very easy for information to be stolen by intermediary attackers during the transmission process, thus causing serious risks to data security. For this reason, corresponding measures should be taken urgently to effectively ensure the security of sensitive data. You can refer to the following methods to operate. The win11 client and server do not support the commonly used SSL1. When upgrading and transforming the server system, you can give priority to upgrading and optimizing the server system, or supplementing the required necessary components to ensure that it can smoothly support the latest SSL protocol. 2. Deploy SSL certificates. You can purchase and deploy SSL certificates issued by prestigious certification centers, and install them in the server to achieve this function. 3. Enable SSL protocol





