 headlines
headlines
 A comprehensive inventory of the most internationally influential hacking incidents in 2016!
A comprehensive inventory of the most internationally influential hacking incidents in 2016!
A comprehensive inventory of the most internationally influential hacking incidents in 2016!
In the past 2016, many large-scale and shocking cyber attacks occurred. The targets of the attacks include many large technology companies, government organizations, and even national party and government agencies, which have been attacked many times in high-profile cases! These attacks directly led to the leakage of millions of people’s sensitive personal information, which was illegally sold on the underground black market.
During the year, Yahoo’s massive information leak was revealed. Even national intelligence service agencies such as the NSA cannot avoid being used and attacked by hackers. This year's US election was also exposed to the interference of Russian hackers in the election. As this year comes to an end, cybercrime will also undergo new evolutions and upgrades, and the challenges we face will become more difficult!
The following PHP Chinese website, China’s largest PHP community (www.php.cn), takes stock of the most internationally influential hacking incidents in 2016!
The official website of Thinkphp, the most widely used open source framework by domestic users, was attacked
In the first week of the new year of 2017, Thinkphp, the most widely used open source framework by domestic users, was attacked The official website could not be opened normally,  , and later tp official responded that it was hacked.
, and later tp official responded that it was hacked.
Next, let’s take a look at the most influential hacking incidents at home and abroad in 2016!
Not only suffered the largest data breach of the year, but one of the two largest. In September, Yahoo announced it had discovered a data breach in late 2014 that affected more than 500 million user accounts. The incident resulted in the leak of some user account information, including names, email addresses, phone numbers, dates of birth, hashed passwords, and some encrypted or unencrypted security questions and answers. Yahoo said it believed a nation-state attack was behind the incident. Just a few months later, in December Yahoo announced a second, larger attack affecting 1 billion user accounts. The second data breach, said to be independent of the first breach that occurred in August 2013, saw an unauthorized third party steal data including names, email addresses, phone numbers, and dates of birth. , data including hashed passwords. Yahoo said some encrypted and unencrypted security questions and answers may also be included. Yahoo said at the time that it had not yet discovered how the attacker gained access to its systems but was working with law enforcement agencies to resolve the matter. Both data breaches can be considered the largest breaches in history. In addition, this period was also the darkest period since the founding of Yahoo. Later, Verizon successfully acquired Yahoo for 4.8 billion. company.
# counter adult dating website is hacked again, causing huge controversy. Previously, the Ashley Madison hack that occurred in July 2015 only exposed the information of 32 million accounts. This attack directly led to the leakage of more than 300 million accounts, email addresses and passwords from the website. In addition, more than 60 million accounts from Cams.com were also affected. Other companies such as Penthouse, Stripshow and iCams were also breached. Therefore, a total of nearly 412 million users were affected by this attack! What does this mean? The "shameful" things you have done on these adult websites in the past 20 years may be exposed, your orientation and your sex partners may be known to the people around you, and all the things you think about yourself are "shady" Things may become known to everyone overnight... It's scary to think about it.
The "Shadow Brokers" hacker group breached the NSA
## Hackers have even targeted the National Security Agency of the United States. A mysterious hacker group called "The Shadow Brokers" claims that they have successfully attacked the NSA and obtained NSA's internal information and the attack tool kit used by the "Equation Group". The Shadow Brokers then shared some of their stolen cyber loot online. At the same time, it was announced that this set of "cyber weapons" used by the US government would be auctioned on the Internet, with a asking price of 1 million Bitcoins (as of around 8:00 on January 6, Beijing time, the price of Bitcoin was 8,592 yuan). The SWIFT hacking incident broke out and many banks lost huge sums of money The Bangladesh Bank was hacked, is one of the most successful cyberattackers to date. In February, the account opened by the Central Bank of Bangladesh at the Federal Reserve Bank of New York in the United States was hacked in early February, and US$81 million was stolen. According to investigations by relevant law enforcement agencies, the stolen money was transferred in batches and finally flowed into the accounts of two casinos in the Philippines and a gambling intermediary. Then it was likely to be turned into a pile of chips and disappeared without a trace. The Bangladesh Bank is not an isolated case. In January 2015, hackers attacked Ecuador’s Southern Bank and used the SWIFT system to transfer US$12 million. At the end of 2015, Vietnam’s Pioneer Commercial Joint Stock Bank was also exposed to an attempted hacker attack. Europol accidentally leaked 54 counter-terrorism investigation data ## Although technically speaking, the Europol data breach was not caused by a hacker attack. However, its impact is huge. Data from a counter-terrorism investigation was accidentally leaked due to errors by Europol staff. The data includes 54 files and more than 700 pages of undercover investigative files. The document involves the investigation results of many anti-terrorism incidents such as the Madrid bombings from 2006 to 2008, and also includes anti-terrorism investigations that have never been made public! Myspace account information leaked ## In May, many users received reminders that they still held Myspace accounts, as Myspace announced a data breach that would affect 360 million accounts. In a blog post announcing the incident, Myspace said it discovered that email addresses, usernames and password information for accounts created before June 11, 2013, were posted on a hacking forum. Myspace updated its platform in 2013, including improving account security. Myspace blamed the incident on Russian hacker "Peace". 900,000 households in Germany were cut off from the Internet and hackers deliberately invaded ## In November, Deutsche Telekom encountered a large-scale network failure. About 900,000 routers out of 20 million fixed network users (about 4.5%) failed, resulting in limited network access in large areas. Deutsche Telekom further confirmed that the problem was caused by the maintenance interface of the routing equipment being exposed to the Internet and that targeted attacks were taking place on the Internet. The Russian hacker group Fancy Bear is suspected of interfering with the US election # The cyberattack on the Democratic National Committee is said to have been launched by the Russian state-backed hacker group Fancy Bear. They obtained the email accounts of many senior officials, including that of Hillary Clinton's chief executive, John Podesta. These data obtained by hackers, including nearly 20,000 emails, were disclosed by WikiLeaks. Many saw this as a major blow to the Clinton team and a huge boost to Donald Trump in the 2016 US presidential election. After lengthy debate and analysis, U.S. intelligence agencies, including the CIA, NSA, Defense Intelligence Department and FBI, have reached a consensus that Russia is seeking to exploit cyber The attacks hit the Democratic Party and pushed and helped Trump win the election. The address of this article: 


 # In October, a botnet controlled by the malware Mirai launched a DDoS attack on Dyn, a US domain name server management service provider. As a result, many websites were down on the east coast of the United States, such as GitHub, Twitter, PayPal, etc., and users were unable to access these sites through domain names. Supporters of WikiLeaks became suspects in the attack.
# In October, a botnet controlled by the malware Mirai launched a DDoS attack on Dyn, a US domain name server management service provider. As a result, many websites were down on the east coast of the United States, such as GitHub, Twitter, PayPal, etc., and users were unable to access these sites through domain names. Supporters of WikiLeaks became suspects in the attack. 


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 1392
1392
 52
52
 Canada plans to ban hacking tool Flipper Zero as car theft problem surges
Jul 17, 2024 am 03:06 AM
Canada plans to ban hacking tool Flipper Zero as car theft problem surges
Jul 17, 2024 am 03:06 AM
This website reported on February 12 that the Canadian government plans to ban the sale of hacking tool FlipperZero and similar devices because they are labeled as tools that thieves can use to steal cars. FlipperZero is a portable programmable test tool that helps test and debug various hardware and digital devices through multiple protocols, including RFID, radio, NFC, infrared and Bluetooth, and has won the favor of many geeks and hackers. Since the release of the product, users have demonstrated FlipperZero's capabilities on social media, including using replay attacks to unlock cars, open garage doors, activate doorbells and clone various digital keys. ▲FlipperZero copies the McLaren keychain and unlocks the car Canadian Industry Minister Franço
 php CodeIgniter Security Guide: Protect your website from attacks
Feb 19, 2024 pm 06:21 PM
php CodeIgniter Security Guide: Protect your website from attacks
Feb 19, 2024 pm 06:21 PM
1. Use the latest version of CodeIgniter The CodeIgniter team regularly releases security patches and updates to fix known vulnerabilities. Therefore, it is important to ensure that you are always using the latest version of CodeIgniter. You can download the latest version by visiting CodeIgniter’s official website. 2. Enforce the use of secure connections (HTTPS) https can encrypt the data passed between your website and users, making it more difficult for malicious users to intercept and steal. You can enable HTTPS by installing an SSL certificate on your server. 3. Avoid using default configurations CodeIgniter provides many default configurations to simplify the development process. However, these default configurations may not
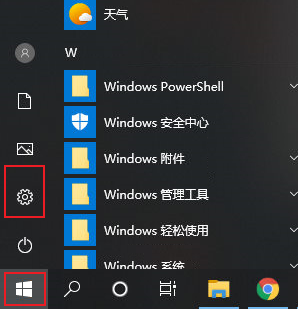 How to set up Win10 firewall whitelist? Win10 plus firewall whitelist
Jul 14, 2023 pm 03:18 PM
How to set up Win10 firewall whitelist? Win10 plus firewall whitelist
Jul 14, 2023 pm 03:18 PM
The built-in firewall function of win10 can block the attacks of some malicious programs for us, but occasionally it may be blocked by the firewall and prevent the program from being installed normally. If we can understand the security of this software and the importance of installation, then we can allow the installation by adding a whitelist to the firewall. 1. Use the win key to open the win10 system menu window, and click on the left side of the menu window to open the "Settings" dialog box. 2. In the Windows Settings dialog box that opens, you can look for the "Update & Security" item and click to open it. 3. After entering the upgrade and security policy page, click the "Windows Security Manager" sub-menu in the left toolbar. 4. Then in the specific content on the right
 Master network security and penetration testing in Go
Nov 30, 2023 am 10:16 AM
Master network security and penetration testing in Go
Nov 30, 2023 am 10:16 AM
With the development of the Internet, network security has become an urgent issue. For technical personnel engaged in network security work, it is undoubtedly necessary to master an efficient, stable, and secure programming language. Among them, Go language has become the first choice of many network security practitioners. Go language, referred to as Golang, is an open source programming language created by Google. The language has outstanding features such as high efficiency, high concurrency, high reliability and high security, so it is widely used in network security and penetration testing.
 Artificial Intelligence in Cybersecurity: Current Issues and Future Directions
Mar 01, 2024 pm 08:19 PM
Artificial Intelligence in Cybersecurity: Current Issues and Future Directions
Mar 01, 2024 pm 08:19 PM
Artificial intelligence (AI) has revolutionized every field, and cybersecurity is no exception. As our reliance on technology continues to increase, so do the threats to our digital infrastructure. Artificial intelligence (AI) has revolutionized the field of cybersecurity, providing advanced capabilities for threat detection, incident response, and risk assessment. However, there are some difficulties with using artificial intelligence in cybersecurity. This article will delve into the current status of artificial intelligence in cybersecurity and explore future directions. The role of artificial intelligence in cybersecurity Governments, businesses and individuals are facing increasingly severe cybersecurity challenges. As cyber threats become more sophisticated, the need for advanced security protection measures continues to increase. Artificial intelligence (AI) relies on its unique method to identify, prevent
 How do C++ functions implement network security in network programming?
Apr 28, 2024 am 09:06 AM
How do C++ functions implement network security in network programming?
Apr 28, 2024 am 09:06 AM
C++ functions can achieve network security in network programming. Methods include: 1. Using encryption algorithms (openssl) to encrypt communication; 2. Using digital signatures (cryptopp) to verify data integrity and sender identity; 3. Defending against cross-site scripting attacks ( htmlcxx) to filter and sanitize user input.
 Ten methods in AI risk discovery
Apr 26, 2024 pm 05:25 PM
Ten methods in AI risk discovery
Apr 26, 2024 pm 05:25 PM
Beyond chatbots or personalized recommendations, AI’s powerful ability to predict and eliminate risks is gaining momentum in organizations. As massive amounts of data proliferate and regulations tighten, traditional risk assessment tools are struggling under the pressure. Artificial intelligence technology can quickly analyze and supervise the collection of large amounts of data, allowing risk assessment tools to be improved under compression. By using technologies such as machine learning and deep learning, AI can identify and predict potential risks and provide timely recommendations. Against this backdrop, leveraging AI’s risk management capabilities can ensure compliance with changing regulations and proactively respond to unforeseen threats. Leveraging AI to tackle the complexities of risk management may seem alarming, but for those passionate about staying on top in the digital race
 Roborock sweeping robot passed Rheinland dual certification, leading the industry in corner cleaning and sterilization
Mar 19, 2024 am 10:30 AM
Roborock sweeping robot passed Rheinland dual certification, leading the industry in corner cleaning and sterilization
Mar 19, 2024 am 10:30 AM
Recently, TUV Rheinland Greater China ("TUV Rheinland"), an internationally renowned third-party testing, inspection and certification agency, issued important network security and privacy protection certifications to three sweeping robots P10Pro, P10S and P10SPro owned by Roborock Technology. certificate, as well as the "Efficient Corner Cleaning" China-mark certification. At the same time, the agency also issued self-cleaning and sterilization performance test reports for sweeping robots and floor washing machines A20 and A20Pro, providing an authoritative purchasing reference for consumers in the market. As network security is increasingly valued, TUV Rheinland has implemented strict network security and privacy protection for Roborock sweeping robots in accordance with ETSIEN303645 standards.


